Working from home has many advantages but also numerous risks
During the global pandemic in 2020 the German government has decided to restrict social contacts as much as possible. Companies increasingly allowed their employees to work from home.
According to the statista website, only 4% of all those surveyed have been working from home before 2020. This value increased to 27% during the first lockdown in April 2020, which is almost a quarter of all respondents who worked exclusively or mainly from home. The value fell over the year but increased to 24% in January 2021. This shows a clear trend towards more people working from home.
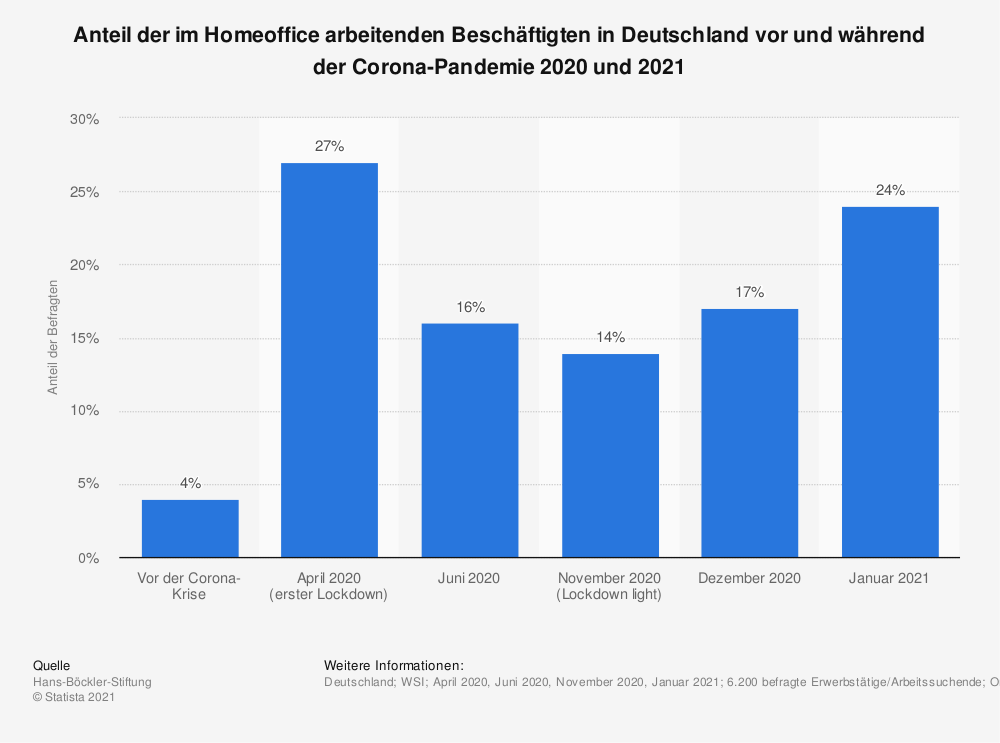
(statista 2021)
This blogpost pursues two central questions:
- What factors influence performance, commitment and job-satisfaction of employees working from home
- What are the risks for employers and how can these risks be reduced?
The magazine “Spiegel” published an article with the headline “Homeoffice mit drei Kindern Zu Hause im Versuchslabor” (Der Spiegel 2020). This article clearly shows the challenge of balancing work and childcare. A challenge that many people had to overcome during last year. But what are the advantages, and what are the disadvantages of working from home?
Not every job is suitable for remote work. A surgeon can hardly operate on his patients at home. Also a baker can not sell his rolls to his customers at home. A software developer, on the other hand, can easily program his application at home or anywhere else in the world. Industries that are most suitable for working at home include jobs in the IT industry, marketing, services such as travel agencies, and jobs in the service sector such as call centres. But also areas of public administration, such as the citizens’ office, increasingly worked from home last year. As schools were closed, teachers also had to restructure their teaching and offered online classes or provided teaching material while the students had to work independently from home.
So why was there less work from home in the past?
Fears and disadvantages
In addition to the technical requirements, such as a PC, a stable internet connection, ergonomic furniture, etc. the changes to do remote work also went hand in hand with the establishment of new structures. As can be seen in the Spiegel article, families had to learn how to reconcile work and family. Daily structures and family structures had to be changed. Working eight hours straight mostly doesn’t work if children want to play with their parents or are in need of support with their school-related tasks. But even if there are no children, internet outages may interrupt video conferences and calls. Furthermore, many people do not have a separate office and thus have to work at the kitchen table.
Another explanation can often be found in the consideration of the employees’ fears. Blurring of work and leisure, lack of IT knowledge, experience in teleworking or lack of direct contact with colleagues, reduced chances of promotion and career opportunities (Grunau et al. 2019). All according to the motto “out of sight out of mind”.
But employers were also hesitant, and in some cases still have doubts, about the meaningfulness and efficiency of working outside the company building. Among other things, they had to adapt organisationally and also find technical solutions to enable their employees to work. This was often accompanied by considerable costs, such as the purchase of laptops, cameras, etc. The price comparison website Idealo shows an increase in prices for PC systems of around 29% from April 2020 to April 2021 (idealo 2021). But not only costs play a role. Companies need managers with the ability to lead employees outside the company’s premises. They need to be able to accept – what is at least often a subjective feeling – the feeling of loss of control over their employees. Often, the experience in dealing with virtual teams is simply lacking here (Grunau et al. 2019).
Advantages
But after all these negative aspects and fears, why do people still decide to continue to work from home, also called “remote work”?
No more bland canteen food, no more colleagues who just come to your desk and stop you from working, no more traffic jams on the way to/from work, sleeping longer in the morning, wearing sweatpants or comfortable clothes all day, more time to spend with your children, doing the laundry at the same time, working in the garden, jumping into the pool in between… There are many different things that are important to people. They love their individuality and live it every day. They love to be able to organize their work time and -place themselves and for them, the new way of working is a big step towards a “work-life balance”. Not everyone struggles with coordinating children and work (Grunau et al. 2019).
For companies, outsourcing employees to their homes can also mean significant cost savings. Company buildings do not have to be expanded when more employees are hired, as they no longer need an individual workplace. This also adds to the cost savings in terms of water and electricity.
Different effects of working from home
Employees who haven’t already worked from home also experience the negative aspects of remote work. These include a closer intermingling of work and private life, supervisors assuming inferior performance, lack of recognition and/or interest on the part of the boss resulting in a lack of motivation, lack of support from colleagues, considerably greater communication effort associated with time delays (the way to the colleague’s desk is no longer possible), higher networking time (Grunau et al. 2019).
Factors that influence the performance, commitment and job satisfaction of employees working from home
Organizational framework conditions
One of the most important aspects is certainly the attitude of an employer. If he does not support working outside the company building and has no trust in his employees, the working relationship is doomed to failure. Ensuring the flow of information, transparency and the ability to lead (virtually) certainly play an important role. When designing flexible working hours, especially in the home office, it is important to have clear rules: time caps, time tracking, realistic workload targets, enough staff, and substitution rules. However, this must be used to the right extent, otherwise employees may get the feeling that they are not trusted and that they are being patronized.
Characteristics of the employees
As the paper by Prof. Dr. Nara Walter nicely illustrates, there are people who can work better or worse remotely because of their personality. Prof. Walter describes the five-factor model of personality according to Costa and McCrae and shows that especially introverts, who need fewer stimuli and stimulation from outside, i.e. less contact with other people, benefit more from remote work than introverts. People who are open to new experiences also cope better with changes coming with working from home.
Conscientious people are perfect candidates for working remotely. They love order and plan their day conscientiously. Working from home can involve certain risks for less conscientious people. Among other things, they tend to forget things, leave things, have an unstructured approach, difficulties with self-motivation, and hectic action under time pressure.
Individuals with a high neuroticism score can benefit from remote work, as their self-consciousness and anxiety in social situations can have less influence on job performance. However, social isolation can also lead to more insecurity. They need more feedback and confirmation about their progress.
Socially acceptable people are team players and enjoy working with others. They also do this remotely which means that this group of people has few problems working from home. Aside from that, a team usually benefits more from having these people physically around and maintaining personal contacts.
Prof. Walter makes it very clear that a person combines every characteristic. However, these are individually pronounced. Who is well suited to work successfully from home depends on the right mix and the environment (Prof. Dr. Nora Walter 2020).
Remote work as a security risk for companies
One of the big hurdles at the beginning of the changeover for many companies was certainly the opening of the company network to the outside. Employees had to be able to access company data and reach certain servers. However, not only employees want to access the company network from outside, but also hackers with less good intentions. The IT security of companies faced new challenges. Weaknesses of the infrastructure and ignorance of the employees were exploited.
The gathering of company-critical data and information by criminals can have serious and sometimes very expensive consequences for companies, such as loss of customers due to reputational damage. If company data falls into the wrong hands, e.g. competitors or industrial espionage, this can mean the end for companies. However, there are often demands for money and associated blackmail by paralysing IT systems. The possible publishment of customer data can result in high fines (deloitte 2021).
The following chart shows the analysis of a survey in May 2020 in Austria, in which companies provided information on whether they have had contact with cybercrime in the last two months. Even in this short period of time, a significant percentage of attacks occurred. In the following, I will briefly discuss some individual attacks and list possible approaches to reduce the threat of a cyber-attack.
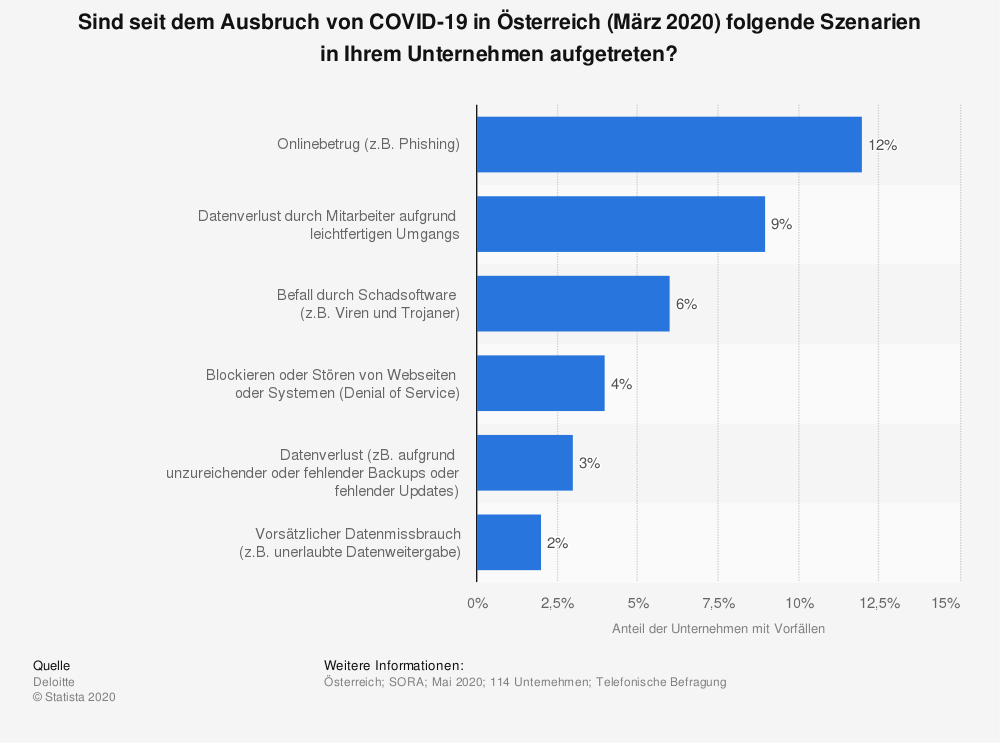
(statista 2020)
Phishing
Phishing attacks were one of the most common methods attackers used to gain access to desired networks. This is a method in which the attacker pretends to be a trustworthy company, e.g. a bank. The victims receive an email asking them to update their data. The pretext often given here is the expiry of contracts, bank data, etc. via a link provided in the email, the victims were taken to an authentic-looking copy of the original page with an input mask. After successfully entering the data and sending it to the attacker, he often gained full access to the desired portals. Last year in particular, this method has been used to gain access to company portals (deloitte).
When phishing emails were easy to spot a few years ago, by 2020 52% of all phishing sites used a target brand name in their website addresses. They were more difficult to detect and thus represented a greater source of danger. A study by F5 Labs found that criminals used stolen passwords within four hours of a phishing attack. Some attacks even occurred in realtime to enable the capture of security codes for multi-factor authentication (F5 Labs 2020).
Multi-Factor Authentication
Multi-Factor Authentication is an authentication method that requires the user to provide another identity proof (factor) in addition to their username and password for verification before gaining access to the desired resource, such as an application. Very often, the user must enter a one-time password (OTP) generated for this purpose as another factor. This is a 4- to 8-digit code that is sent to the user via email, SMS, or app, for example. However, fingerprint, face scan, voice recognition, retina or iris scan, or similar biometric features can also be used.
Malware infestation
According to the German Federal Office for Information Security (BSI), around 117.4 million new malware variants were released in the period from June 1, 2019 to May 31, 2020. Antivirus programs offer protection against such malware. These are designed to detect malicious software, prevent it from running successfully and remove it from the system. While detection methods exist for known malware variants, new variants are not yet recognizable as malware immediately after their appearance and are therefore particularly dangerous. New variants are created by program code changes. But what are malware programs and how do they get into victims’ systems?
Malware (a made-up word from “malicious” and “software”) refers to any type of malicious program. This can be, for example, viruses, worms, trojans, keyloggers, spyware, or rogueware that can perform harmful operations or enable other programs to do so.
Malware usually enters a computer via attachments or links in emails. For example, if a victim clicks on a link that leads to a manipulated website, the software will be downloaded in the background through an unnoticed download. A so-called drive-by download. However, the malware often gets into the victim’s system by means of integrated or removable media such as USB drives, or through the malware’s ability to move from computer to computer or over the network and thus spread independently. For the infection, malware usually exploits vulnerabilities. These can occur in software or hardware products.
The individual malware programs differ in terms of their functionality, and a malware program can also have multiple functionalities.
A computer virus is a type of malware that spreads by inserting a copy of itself into another program and thus becoming a part of it. It spreads from one computer to another. Viruses spread when the software or document they are attached to is transferred from one computer to another via the network, a hard drive, file-sharing, or infected email attachments. What exactly the virus does depends on its complexity. Simple malicious code damages hard drives or deletes files, for example. A more complex virus may hide on the system and perform unwanted activities such as spreading spam. Sophisticated viruses, called polymorphic viruses, hide by modifying their own code and thus remain unnoticed.
Computer worms are similar to viruses in that they can replicate functional copies of themselves and cause the same kind of damage. Unlike viruses, which require the propagation of an infected host file, worms are standalone software and do not require a host program to spread. They either exploit a vulnerability on the target system or use a form of social engineering to trick users into running them.
Trojans are programs that contain applications that are not what they appear to be. They usually disguise themselves as useful apps, but carry malicious code.
Ransomware is usually an encryption Trojan that encrypts the user’s files or makes applications inaccessible. Payment of a ransom is then required for decryption. However, whether or not the key is actually delivered is a gamble.
Rogueware is downloaded to computers via pop-ups on the internet. They imitate the look and behavior of a virus scanner. However, the virus detections reported by the program are fictitious. They are only used to sell an alleged antivirus program.
Keyloggers store the user’s keystrokes. Thus, all entered passwords, PINs, etc. can be recorded and sent to a third party. With data captured this way, criminals can penetrate the corporate network and copy, delete or modify data.
Spyware collects information about a device or network and transmits this data to the attacker. Often, this is how personal information, including login credentials, credit card numbers, or financial information, is collected for the purpose of fraud or identity theft.
New variants of the Emotet malware, which has been increasingly used for cyber attacks since September 2019, emerged. The appearance of Emotet marks a change in attackers’ methods. In the past, untargeted mass attacks were carried out which then randomly hit targets, but malware attacks are often cleverly merged by the combined usage of different malicious programs.
(Bundesamt für Sicherheit in der Informationstechnik 2020)
But what can companies do to increase their IT security?
In addition to the security-enhancing measures already mentioned, such as multi-factor authentication, there are many other, different approaches. For example, some companies tend to prohibit their employees from using private computers. This is also recommended by the Independent Center for Data Protection Schleswig-Holstein (ULD). They have published a paper with recommendations for working from home in 2020. The focus here lies on protecting personal data from unauthorized access at home, during transport, or during data transmission. Technical and organizational security measures, such as encrypting mobile device’s hard drives and external storage media, as well as the correct setup of workplaces, are addressed.
Many employees feel protected at home and forget, for instance, if a window is open, neighbors may be able to overhear a conversation with a customer or colleagues. If a data breach occurs, the employee must know who to report it to.
The following section lists individual tips from ULD.
- Paper documents are best taken and stored in a lockable container.
- Choose a location where others can not see the screen – even through a window. A privacy film for the monitor can help with this manner.
- Documents containing personal data should be kept locked, preferably in a locked room or container.
- In case you need to process data on a private computer, be sure to store official data encrypted.
- Do not throw official paper documents into your private paper trash.
- Dial into the network of your company or authority via a secure connection (VPN). If necessary, access to sensitive areas must be excluded.
(Unabhängiges Landeszentrum für Datenschutz Schleswig-Holstein 2020)
Often, companies already have policies, which regulate working off-site. If these do not exist, company owners and employees should agree on certain rules. But despite the guidelines, training is needed to educate employees and provide them with information so that they are better sensitized in everyday life and are more secure in dealing with phishing emails and malware, for example.
The IT department is particularly in demand because technical tools and security precautions are necessary for protecting the infrastructure.
Possible precautions can be such as antivirus programs, firewall settings, early updates of the software used, encryption when transferring data, backups, spam filters, monitoring, regular changes to passwords, restricting the rights of normal users, simulation games, and simulations of attacks.(Deloitte 2020)
A potentially big threat for companies is not having a clear plan for emergencies. If an attack occurs and your first action is having to figure out how to deal with the situation, it is clearly too late. Prevention before reaction (Deloitte 2020).
Literaturverzeichnis
- statista (2021): Anteil der im Homeoffice arbeitenden Beschäftigten in Deutschland vor und während der Corona-Pandemie 2020 und 2021 | Veröffentlicht durch: Hans-Böckler-Stiftung | Veröffentlichungsdatum: Februar 2021
URL: https://de.statista.com/statistik/daten/studie/1204173/umfrage/befragung-zur-homeoffice-nutzung-in-der-corona-pandemie/
Abrufdatum: 17.09.2021 - statista (2020): Sind seit dem Ausbruch von COVID-19 in Österreich (März 2020) folgende Szenarien in Ihrem Unternehmen aufgetreten? | Veröffentlicht durch: Deloitte | Veröffentlichungsdatum: Mai 2020
URL: https://de.statista.com/statistik/daten/studie/1120592/umfrage/vorfaelle-von-cyber-angriffen-und-datenverlusten-in-der-corona-krise-in-oesterreich/
Abrufdatum: 19.09.2021 - Grunau,P./Ruf,K./Steffes,S./Wolter,S. (2019): Mobile Arbeitsformen aus Sicht von Betrieben und Beschäftigten: Homeoffice bietet Vorteile, hat aber auch Tücken. In: IAB-Kurzbericht, Vol. 11/2019, Nürnberg
- Der Spiegel (2020): Zu Hause im Versuchslabor.
Onlinepublikation auf Spiegel.de: https://www.spiegel.de/karriere/wegen-corona-homeoffice-mit-drei-kindern-so-klappt-es-a-9c137d74-0c31-4710-936c-8d4bc475daae-amp
Abrufdatum: 17.09.2021 - idealo (2021): Halbleiter-Engpass: Verbraucherpreise für Elektroprodukte steigen
URL: https://www.idealo.de/unternehmen/pressemitteilungen/halbleiter-engpass-verbraucherpreise-fuer-elektroprodukte-steigen
Abrufdatum: 17.09.2021 - Prof. Dr. Nora Walter (2020): HOMEOFFICE UND DIE BIG 5
URL: https://www.wirtschaftspsychologie-rhein-ruhr.de/2020/03/31/homeoffice-und-die-big-5/
Abrufdatum: 17.09.2021 - deloitte (2021): Das Homeoffice als Sicherheitsrisiko Was Unternehmen tun können
URL: https://www2.deloitte.com/dl/de/pages/legal/articles/sicherheitsrisiko-homeoffice.html
Abrufdatum: 19.09.2021 - Deloitte (2020): Cyber Security Report Österreich 2020 | Eine Studie von Deloitte Österreich in Kooperation mit SORA
URL:
https://www2.deloitte.com/content/dam/Deloitte/at/Documents/risk/cyber-risk/at-cyber-security-report-2020.pdf
Abrufdatum: 28.09.2021 - F5 Labs (2020): Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
URL:
https://www.f5.com/de_de/company/news/features/phishing-attacks-soar-220–during-covid-19-peak-as-cybercriminal
Abgerufen am: 19.09.2021 - Unabhängiges Landeszentrum für Datenschutz Schleswig-Holstein (2020): Datenschutz: Plötzlich im Homeoffice – und nun?
URL: https://www.datenschutzzentrum.de/uploads/it/uld-ploetzlich-homeoffice.pdf
Abrufdatum: 28.09.2021 - Bundesamt für Sicherheit in der Informationstechnik (2020): Die Lage der IT-Sicherheit in Deutschland 2020
URL: https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/Publikationen/Lageberichte/Lagebericht2020.pdf;jsessionid=6569C9AFA24E9220DF92F3BD3931115D.internet081?__blob=publicationFile&v=1
Abrufdatum: 28.09.2021

Leave a Reply
You must be logged in to post a comment.