The majority of the 1 billion monthly whatsapp users may be a little confused about the tiny yellow info-box in their familiar chat. End-to-end encryption? Is this one of these silly annoying whatsapp-viruses or maybe something good?
The first big question is “why”. Why do we need a (so complicated) whatsapp end-to-end encryption? The most important answer is obvious: cause the sent messages are highly personal and worthy to protect against third-party attackers or facebook/ whatsapp itself. From facebook’s point of view there are some more reasons like pressure caused by competitors or loss of trust by the users.
How does it work?
The next question is, how does this end-to-end encryption work and is it really safe? As a foundation for their protocol they use the Signal Messaging protocol by Open Whisper Systems which security experts trust in. Namely Edward Snowden says: “Use anything by Open Whisper Systems.” With that said we want to take a closer look and check out a short white paper describing their use of the encryption mechanisms. The first statement answers one of our questions: Is whatsapp saving my data in cleartext on the server? They say no. The messages are encrypted so that no third party nor whatsapp itself are able to extract plain text from messages or calls. A picture says more than thousand words, so there is one, trying to grasp the concepts involved in the encryption process.
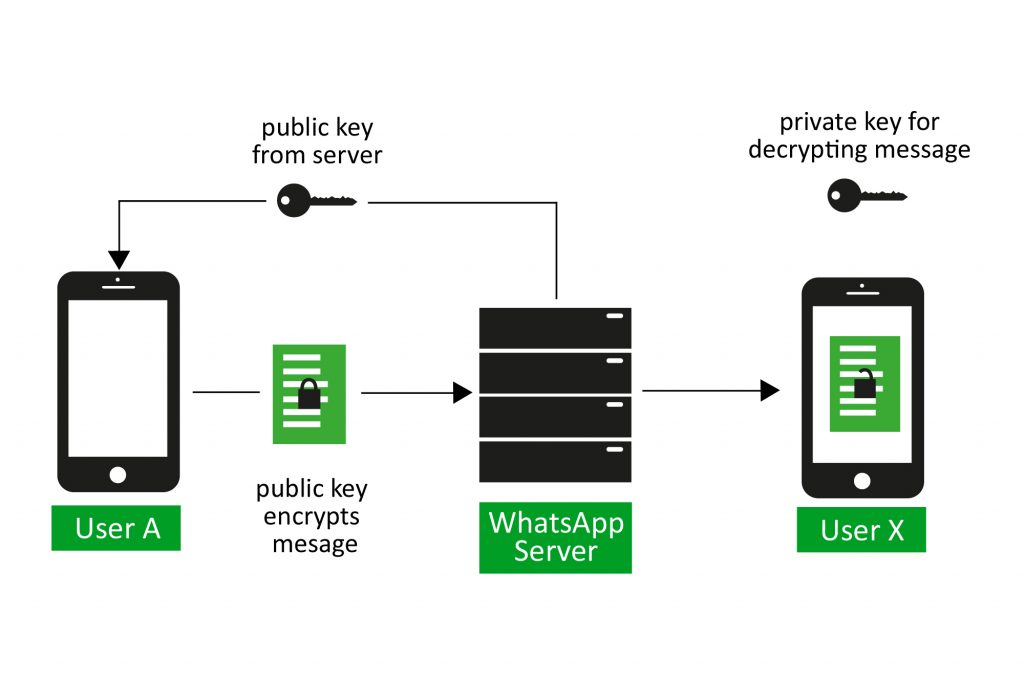 To be able to send messages back and forth three steps have to be performed beforehand.
To be able to send messages back and forth three steps have to be performed beforehand.
- client registration
- session initiation
- receiving session setup
After a long running session is established messages can be exchanged.
The client sends his public keys, which were generated at install time, to the server where they are saved with an user identifier. If User A wants to send a message to User X he requests the public keys from the Server and establishes a long running session by calculating a master secret with Elliptic Curve Diffie Hellman (ECDH). After that a so called root key and chain keys are generated with HKDF to transform the cryptographic weak material in cryptographic strong material. User X receives the public key material and generates a master secret, a root key and chain keys as well. After the session is established for each sent message a message key is generated by using a chain key, which is changed as well for each transmission and generated using the root key.
In the next section we want to look at the security aspects of the end-to-end encryption of whatsapp.
Loopholes and weak spots?
 Trying to understand the rough concept behind end-to-end encryption and identifying potential security problems it is helpful to sketch out all the components in the system. The best way to do that is a piece of paper or a whiteboard, as you can see on the left.
Trying to understand the rough concept behind end-to-end encryption and identifying potential security problems it is helpful to sketch out all the components in the system. The best way to do that is a piece of paper or a whiteboard, as you can see on the left.
The following picture is similar to Fig. 1 and shows the elements of the system. We want to keep the format of asking questions to identify areas important for security.
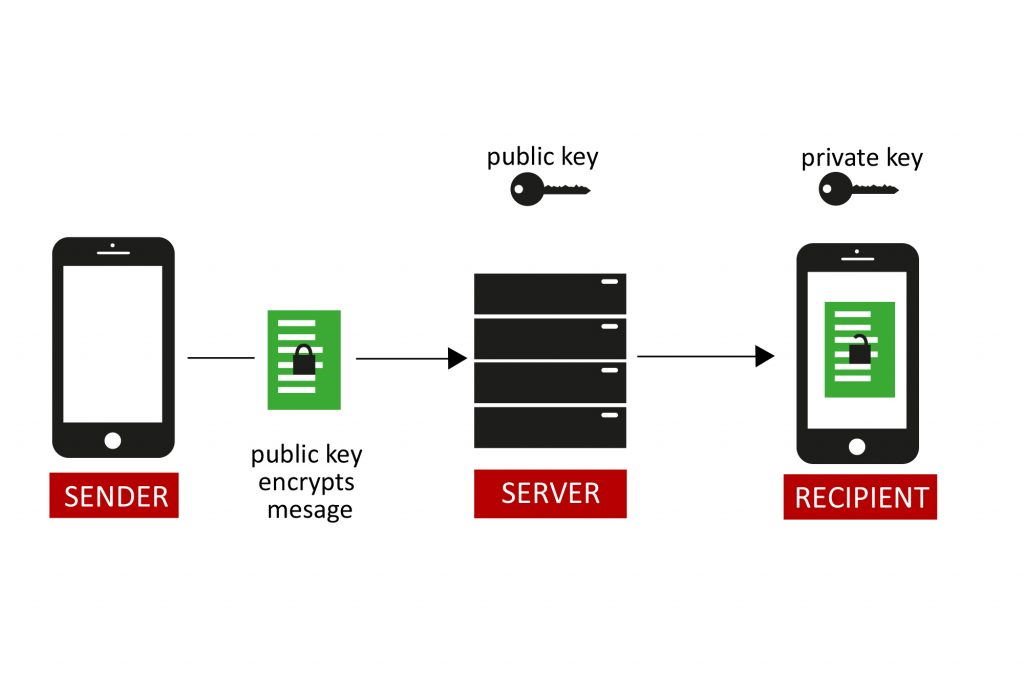 1. Are the keys safe on the servers of whatsapp and what happens if they would be compromised?
1. Are the keys safe on the servers of whatsapp and what happens if they would be compromised?
On the server data is saved encrypted as well, so that from the data itself no clear text information can be extracted. Another way to get hold of information would be the man in the middle attack where somebody would pose as a whatsapp server and record all the information. Still the keys are encrypted because the private keys are not saved on the servers.
2. What happens if somebody gets hold of one of the long running session keys?
The encryption protocol uses forward secrecy. Forward secrecy uses long-term keys to generate new keys for every new session. If the communication is recorded and the long-term keys compromised it is not possible to extract the used session keys. Therefore a encrypted communication cannot be encrypted even if the long-term keys are in the possession of an attacker.
3. Is it possible to extract plain text out of a message somebody stole?
The same principle is applied to messages. For every message a new message key is generated from a chain key with a hash algorithm. Meaning the message key cannot be derived after transmission and receiving. With every round trip a new chain key is generated from a root key using Diffie-Hellman procedure. So there are two security mechanisms to secure messages. In the whitepaper they are called an immediate “hash ratchet” and a round trip “DH ratchet”.
After looking at these three questions we want to see where the weak spot is right now. The security of the server and the transport of messages are ensured by the encryption protocol. A practical examination done by heise security has shown, that the encryption works as it should. After looking at the server and the communication we take a look at the sender and recipient, the user, and realize that there is the weak spot right now. The private keys are generated at install time on the user’s phone. In case somebody is able to extract the keys he can pose as the user and send messages back and forth. If the phone is physically stolen and not secured the messages and all the information is fully accessible.
Questions
Now, that we got a small overview over the end-to-end encryption used by whatsapp we sum up our questions we had and add some more questions which remain open because they would go beyond the scope of a short blog post.
- Does WhatsApp save the data on the server encrypted as well?
- Is the encryption working as described in the white paper by whatsapp ?
- How are the initial key pairs generated on the user’s phone?
- Is the cryptographic quality of the keys sufficient?
- How is the app itself secured on the phone?
- Are old messages encrypted as well?
Still there are questions remaining open, which address the topic in a broader manner. For communication still some data is needed to ensure correct delivery. Out of metadata a lot of personal information can be extracted. So the next question is:
- Is it possible to hide private contact information (metadata)?
Another question regarding the security awareness of the user opens the space for discussion.
- Who is responsible for the data, the user or whatsapp?
- What are the main reasons for using a messenger, security, functionality or who else does it use?
Conclusion
After conducting a small security analysis it is fair to say that whatsapp’s encryption satisfies current security standards. Nevertheless, as a user you should always be aware that metadata is still a great source to extract personal user information. As a user you should know that it is unclear what the service provider is actually doing in the background with your data. Using the service requires trust to the service provider. Another point is the shift of security risks to the devices of the users. Oftentimes users lack security awareness and do not guard their phones or computers sufficiently.
Blogpost by Martin Kopp and Jonas Häfele
References:
https://www.whatsapp.com/security/
https://blog.whatsapp.com/10000618/end-to-end-encryption?
http://www.computerworld.ch/typo3temp/pics/7d5758ae0c.jpg

Leave a Reply
You must be logged in to post a comment.