Humans can be regarded as one of the biggest weaknesses for secure systems. Their interaction with technology and awareness for information security makes them usually the “weak link” for gaining access to enterprise networks and private information. From an attackers point of view the investment of using a human to hack a system is much cheaper than searching for 0-day exploits or unpatched vulnerabilities. That’s why the art of human hacking, called Social Engineering, has become an important threat factor for secure systems.
Social Engineering is the effort to get a victim to do something beneficial to the attacker such as getting victims to divulge passwords or credit card information. But how is this primarily accomplished? The answer to this question is through manipulation of the human element. To get a basic understanding on how Social Engineering works (at least from a theatrical view-point), we will have a look at the following YouTube clip from the movie Red Dragon and analyze it with the help of Barnlund’s communication model.
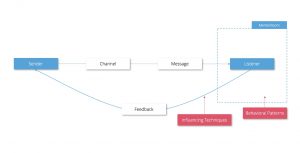
What happened there in detail? A vicious sender (Dr. Hannibal Lecter) transmitted a message (“give me Will Grahams private address”) via a specific channel (phone) to a listener (Dr. Bloom’s secretary). Usually every person has a communication filter active while listening to another person, called mental room. This filter prevents us from accepting messages blindly and forces us to question the intention of a sender. To work around the secretary’s mental room, Hannibal Lecter exploited human behavioral patterns (e.g. lack of time which forces a hasty decision) and influencing techniques (such as threatening that Will Graham’s assistant will be in trouble, if she doesn’t help). Once Hannibal had invaded her room, the secretary gave Hannibal his desired feedback.
After reading this series you will know how to avoid such an attack, you will learn:
- Which behavioral patterns a trained Social Engineering uses to get in your mental room? (part1)
- What advanced influencing techniques are available to control your communication feedback (part 2)
Behavioral patterns
In this section, we are going to examine evolutionary and socially learned behavioral patterns that a social engineer can use to influence and to break into the mental room of his victims. Those patterns can be seen as fuel that makes a Social Engineering attack possible. Knowing them is the first important step to get your brain’s firewall up and running.
Reciprocity
Reciprocity is an important principle of everyday human interaction. It refers to an intrinsic expectation that a positive action should be rewarded with another positive action (“something for something”). If you receive something of value from another person, e.g. a useful information or a tangible gift, you will subconsciously feel the urge to give something back.
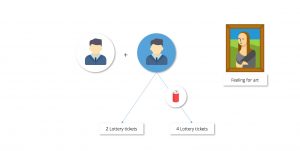
The power of reciprocity was scientifically demonstrated by Dennis Regan in 1971. Regan matched two probands and told them to rate artwork together, because he wanted to study their “feeling for art”. In fact one of the probands in every research pair was a scientific assistant of Regan, who should test the effect of reciprocity by giving a can of cola to the other person. After the art experiment was finished the scientific assistant asked if the other person wanted to buy some lottery tickets from him. In average all probands that received a cola bought twice as much tickets (even if they didn’t like the assistant, because he contradicted with their opinion on art).
Use Case: While trying to get physical access to a secured location, reciprocity can be accomplished by hanging out in the smoker’s area and offering to light someone’s cigarette. This small gesture will increase the chance of someone holding an entrance door open for you.
Authority
From a young age, people are taught to respect parents, teachers, police and other persons of authority. This principle is instilled in all of us from early childhood and follows us through adulthood. Leveraging authority in social engineering is an effective tactic, because humans lean to accept instructions from authorities without questioning them at length (especially if the authority holds power over the target, like a CTO).
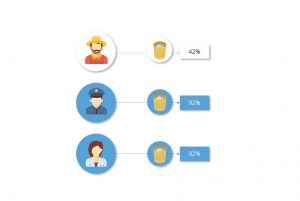
In an experiment by Leonard Bickman, pedestrians on a public street were requested to pick up trash that didn’t belong to them. Around 92% pedestrians followed the instruction without hesitating, if the command came from a person of authority.
Use Case: Organizational authority can be used to persuade less senior staff into compliance by making them belief the attacker maintains some level of power over them.
Obligation
There are actions that make you feel you have to do them based on social, ethical and legal requirements, contracts and promises. This feeling is closely linked to reciprocity. For example calls for donations typically get a higher return rate if the recipient is personally addressed in the call. A personal address will create a social obligation.
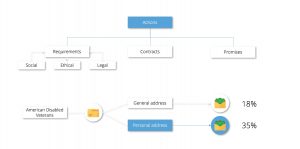
Use Case: An example of an obligation tactic might be sending an employee of a company you want to attack a modified USB-mouse with malware on it, e.g. as a prize for wining at a competition. The employee will usually feel the social obligation to at least test the mouse once.
Scarcity
Scarcity is a pattern often used in advertising like sales or special offers. Scarcity can be used to manipulate a person’s thoughtfulness by creating feelings of urgency and forcing the person to make quick and rash decisions. Also combining scarcity with patterns like authority can strengthen the Social Engineering attack.

Use Case: Every scenario with the word “urgent” in it.
Concession
Concession has its historical origin in trading. When two persons are bargaining for an assets, usually both persons propose a potential price until an equilibrium is reached. This behavior of wanting to concede can also be used to manipulate people.
Use Case: In the context of social engineering, a concession might be used in a phishing attack over phone (vishing). At first the attacker asks for the social security number of the victim. If the victim gets suspicious and doesn’t want to give this information over the phone, the attacker then lowers his expectation (cost) by saying the victim could instead visit a website and enter it by himself. Because the attacker conceded by lowering the “cost”, the victim feels compelled to oblige and meet halfway.
Likability
In a study about “tips and advice” researcher found out that humans prefer to take a bad advice from somebody they like, e.g. a friend, instead of a good advice from somebody unappealing. This pattern can be found in everyday life or as social engineer Christopher Hadnagy puts it: “People like to be liked and like people who like them”.
Use Case: The goal is to establish a rapport with the target. This can be accomplished through tactful compliment, a positive demeanor and a confident aura.
Continue to read in Part 2

Leave a Reply
You must be logged in to post a comment.