In the first part of this series you learned which behavioral patterns are usually used to influence humans. Those patterns are the basis of a Social Engineering attack and can usually be detected by a trained person. In the second part we will examine much more sophisticated influencing techniques. Those techniques are very tricky to detect and form a higher threat for your brain’s internal firewall.
Advanced Influencing Techniques
Framing
The Framing-technique is based on current studies conducted by the University of California, Berkeley. Researchers from the International Science Institute discovered with the help of brain scans and experiments that language (to be precise words) automatically creates frames in our brains. Those frames are used to put physical experiences and stored knowledge in relation. The last sentence sounds very abstract, we will try to fetch the concept with the help of two examples:

Experiment 1: After reading all words on the left side, probands did walk slower than their counterparts that read the right side. Words belonging to the domain of “aging”, trigger frames in brain areas responsible for physical experiences.
Experiment 2: After reading both sentences, all probands were one day later asked if they could recount the content of the first sentence. Most of them answered that John used a hammer to hit the nail. Based on the stored knowledge, “in 99% we use a hammer to hit a nail”, an association of John using a hammer was trigged by reading the words “hitting” and “nail”.
Use Case: Donald Trump is using framing frequently to manipulate the public opinion. In his 2016 presidential campaign for example, Trump used frames that stimulate brain areas responsible for disgust while talking about his fellow campaigners or opponents. In contrast he used frames that describe him as very clean (clean == trust worthy/good character) when talking about himself.
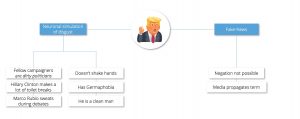
Also he introduced the word fake-news to English speaking countries. Fake-news is a metaphorical mapping that links an idea (news) to an adjective (to fake). Such a mapping is an incredible strong frame, its usage restricts the influence of the media and can’t be negated. When you read the sentence “don’t think of a pink cow”, you will automatically activate the frame in your brain. The same happens when the media is trying to say that they are not fake-news; They propagate the term and enhance its effect through hebbian learning.
Micro-Expressions
Micro-Expressions can also be used very well for manipulation. In 1972 Dr. Paul Ekman identified six expressions connected to universal feelings. Those expressions are deeply anchored in the human brain, their simple imitation will arise the connected feeling. Try to imitate the micro-expressions linked to anger (press your lips together and make a raging look with your eyes) and you will automatically feel anger growing in your stomach.

Researchers also discovered that humans are subconsciously mirroring the micro-expressions of other humans for the fraction of a second. In Social Engineering this finding can be utilized to trigger feelings in your victim by employing micro-expressions. After seeing a tv-fundraiser for kids in Africa, you probably feel some kind of grief because your brain is automatically mirroring the micro-expressions of the (sad) kids shown in the video.

Use Case: By reading the micro-expressions of your victim, you can identify their state of mind, e.g. fear. Depending on the situation, this can be used to enhance (or to weaken) your victims feelings by triggering more fear with your words or body language.
Quick Rapport
The goal of every Social Engineer is to build rapport quickly. Rapport is a relationship with mutual interaction and can be seen as an excellent entry point for further attacks. One of the leading experts on rapport, Dr. Milton Erickson, had fallen ill with polio as a child. As a result of his illness he had to spent years in bed and could often only observe people. He recognized that people who like it each other start to mirror themselves after time. For example they adjust their body language of breathing pattern to match their partner.
The following figure illustrates recommended tactics by Dr. Erickson to build quick rapport:

Use Case: To build rapport quickly a Social Engineering tries to mimic discreetly his victim in a personal conversation. In advance he could also have found out the needs of his victim which he will try to target.
NLP
Embedded commands are a technique from NLP (Neuro-linguistic Programming), comparable to a SQL-injection via language. In NLP you try to conceal commands by constructing sentences with a special syntax or by emphasizing words particularly. A lot of experts see NLP as a pseudoscience, but in advertising NLP is often employed with success – you have to decide on your own.
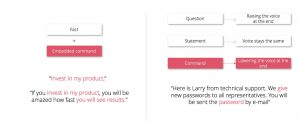
Use Case: In the figure above on the right side, NLP is used to extract a password from a victim via vishing. When you express a command in the German language you lower your voice at the end of the command. An attacker with enough practice will try to accommodate his speech pattern to inject the command “give password” in your subconscious by lower his voice at the red words.
Final thoughts
In a nutshell, Social Engineering is a powerful weapon to attack secure systems. Employees have to be educated about the topic – pointedly said they need to get their brain’s firewall up and running with the right set of drop- and reject-rules. This blog post can be seen as a basic entry into Social Engineering, but in practice you need experience to identify a sophisticated Social Engineering attack. In a corporate environment you additionally need predefined guidelines that handle certain potential Social Engineering situations, like only opening e-mail-attachments in a sandboxed offline environment. Employees have to stick to those guidelines and must be aware of potential risks.

Leave a Reply
You must be logged in to post a comment.