In May of this year, a cyberattack on the largest pipeline in the United States made global headlines. The supply of various petroleum products came to a standstill for several weeks. Pictures went around the world showing how fuels were filled and transported in a wide variety of containers. Even plastic bags were filled with the highly flammable liquids for fear of not having access to fuels for a longer period of time.
Accelerated by the Corona crisis, digitization in Germany is on the rise. But as digitization increases, so do the potential risks in IT security. As in the USA, critical infrastructures in a wide range of sectors in Germany have long been digitized. For years, there have also been repeated attacks on critical infrastructures in Germany. But is Germany prepared for the growing threat? The question is whether Germany is heading for major problems if critical infrastructure such as the energy and healthcare systems or the water supply are not adequately protected.
This article takes a look at attacks on critical infrastructure in Germany. What has happened so far? Is Germany prepared for attacks? Who helps when being attacked? And what needs to change?
In this Article
Critical infrastructure
For years, there have been repeated attacks on various critical infrastructures in Germany as well. But what are critical infrastructures? The Federal Office of Civil Protection and Disaster Assistance and the Federal Office for Information Security describe critical infrastructures as follows:
Kritische Infrastrukturen (KRITIS) sind Organisationen oder Einrichtungen mit wichtiger Bedeutung für das staatliche Gemeinwesen, bei deren Ausfall oder Beeinträchtigung nachhaltig wirkende Versorgungsengpässe, erhebliche Störungen der öffentlichen Sicherheit oder andere dramatische Folgen eintreten würden.
https://www.kritis.bund.de/SubSites/Kritis/DE/Einfuehrung/einfuehrung_node.html
In English: Critical infrastructures (CRITIS) are organizations or facilities with important significance for the state community, the failure or impairment of which would result in lasting supply bottlenecks, significant disruptions to public safety or other dramatic consequences.

This includes various sectors.The energy sector was attacked in the example in the introduction. Electricity, fuel and district heating are included in this sector. The Corona crisis has also brought the health sector into the public eye. This includes not only inpatient medical care, but also the medical products and medicines needed for this purpose. In addition, laboratories are also part of this sector. IT and TK stands for information technology and telecommunications. This involves the processing, transmission and storage of data. Transport and traffic relates to both people and goods on all transport routes, i.e. air, rail, road and water. Media and culture include broadcasting and the press, but also cultural assets and symbolically important buildings. Water includes both drinking water and wastewater. Finance and insurance refer to various types of payment transactions, securities, derivatives and insurance. Food comprises the production of and trade in foodstuffs. Government and administration refers to government and administration on the one hand, but also to judicial institutions and strutures for emergencies such as disaster control and rescue. There is also a sector for waste management. If one or more of these sectors is attacked or otherwise suffers damage, the consequences for the population will be severe. So surely this infrastructure must be particularly well protected… right?
What happened so far
Infrastructures from the sectors mentioned above have already been attacked in Germany in the past. These are often attacks with ransomware that encrypts important data and thus paralyzes operations. Against payment of a ransom, the blackmailers then (hopefully) hand over the corresponding key. But espionage or simply damaging institutions can also be the goal of such an attack.
As in the USA, infrastructure from the energie sector has already been attacked in Germany. In 2018, various groups, presumably from Russia, attacked German energy providers on a large scale. Some of the attempted attacks were successful, and at times access was gained to the utilities’ systems. In contrast to the pipeline hack in the USA, however, the general public in Germany hardly noticed anything.
During the Corona pandemic, attacks on the medical sector increased noticeably. An unusual case occurred in Düsseldorf in 2020. After the Düsseldorf University Hospital fell victim to a ransomware attack, which even resulted in the death of a woman, the police contacted the perpetrators. The perpetrators had originally intended to attack the university, not the hospital, and subsequently withdrew their extortion.
The German Bundestag has also already been hacked. In 2015, it was also the victim of an attack from Russia. Various computers in the Bundestag had been infected with spy software.
And a short time ago, the first cyber desaster was declared after the administrative system of the city of Anhalt-Bitterfeld was encrypted. This meant that people could no longer be paid alimony or social benefits.
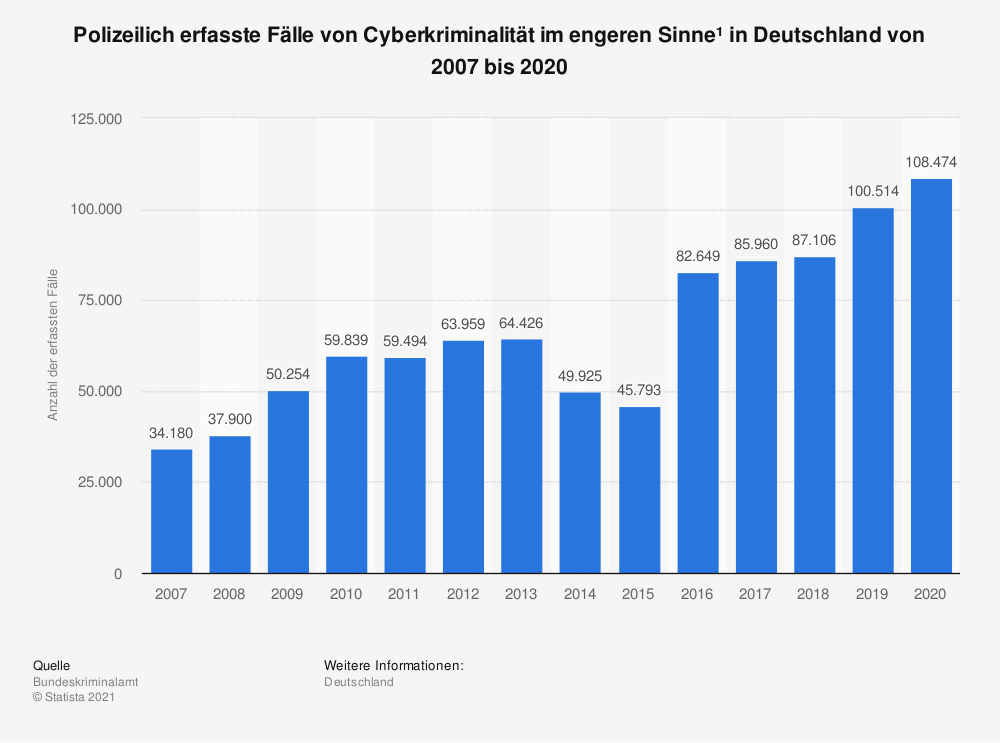
The list of such cases is endless. Each of the critical infrastructure sectors has had to deal with attacks that have had more or less dire consequences. And cybercrime is on the rise! While there were 34,180 recorded cases in 2007, this figure has almost tripled to 108,474 cases by 2020.
The BSI reports a total of 419 cases in Germany in which critical infrastructure was affected by impairments between June 2019 and May 2020. In 2018, there were only 145 such incidents. However, not all of these incidents are hacking attacks, of course. But what is being done to protect critical infrastructure, help in an emergency, and prevent attacks in the future?
The Problem
Attacks on critical infrastructure can have far worse consequences than they have had so far in Germany. In the worst case, instead of one person, many could die in the next attack. But who is responsible for making sure that doesn’t happen? Can each individual take precautions? Or does the responsibility lie with the operators of the critical infrastructure? Can a company be saddled with that much responsibility on its own? What happens if there is still an outage due to an attack?
Let’s take a look at the responsibility of each individual. The Federal Office of Civil Protection and Disaster Assistance offers various information to help in an emergency. It also provides tips on stockpiling, preparation and behavior in the event of a disaster. But the tips given there will only solve problems in some critical infrastructure sectors. And even that is only possible to a limited extent. The list for stockpiling can hardly be completely fulfilled by students with a 10-square-meter room. One already fails at the simple question of where to store all the stuff! And even if the supplies are filled and medicines are available – how long does it take until supplies are needed? Moreover, the responsibility starts with individuals only after infrastructure has already failed. In this case, nothing can be done preventively. The responsibility for prevention must therefore lie with the operators of critical infrastructure.
That’s what the BSI Law is for. This regulates how critical infrastructures must be protected. It determines which facilities belong to the critical infrastructure and which security precautions must be taken. Upon request, the Federal Office for Information Security can assist the states in securing their information technology. For the purposes of the law, however, only infrastructures serving 500,000 or more people are considered critical. The BSI is allowed to recommend certain security products and set minimum standards. If these are not complied with, fines of up to 50,000 euros may be imposed.
But the work of the BSI is criticized by experts. There is little to no oversight of the BSI’s minimum standards and liability regimes. The supervisory structures are not independent. This means that there is no quality control of the BSI’s recommendations and no guarantee that security vulnerabilities will not be passed on to other federal agencies to exploit. The deficit is evident in incidents such as the security hole in the Citrix remote access software, which led to numerous attacks and was only closed by the manufacturer after some time. Among others, rescue control centers were threatened. The IT Security Act lacked any legal basis for holding the manufacturer responsible. There was neither an obligation to report nor an obligation to update.
In addition, the quantitative increase in attacks has increasingly limited the coping capacity in large-scale damage situations. The BSI has only 15 staff members who must take care of nearly 2000 critical infrastructures. Civilian helpers are not available because they were not scheduled.
For some years now, independent experts have therefore been calling for a rethink. The threats must be taken more seriously and changes must be made.
What must happen
Anyone who deals with the topic of IT security of critical infrastructure quickly comes to the conclusion that Germany is in a high-risk situation. For this reason, the AG KRITIS was founded in 2018. AG KRITIS is a working group of experts that is independent of government and industry. It was founded in 2018 from the CCC’s 34th Chaos Communication Congress. Its goal is to expand the resources of the Federal Republic to reduce the impact of large-scale damage caused by cyber incidents to critical infrastructure and to manage crises and disasters caused by them. The AG KRITIS plays an important role in Germany by providing independent advice to the Bundestag. Moreover, it is not linked to economic or political interests and can therefore provide neutral support. As a result, the AG KRITIS was consulted at various points in an advisory capacity.
The experts of the AG KRITIS have published a catalog of several political demands, which will be discussed below.
Independence of the BSI
As already mentioned, the BSI’s dependence on other ministries, in particular the Federal Ministry of the Interior, Building and Home Affairs, means that there is a risk that security vulnerabilities will not be closed but will be passed on to other authorities for exploitation. The legal basis for this even exists. This can happen in the case of suspected terrorist threats or espionage activities. There is no clear dependency on instructions to prevent this. If the BSI were to work exclusively independently and defensively, this would create trust, which would lead to an increased willingness to report security gaps. Security gaps must be closed and must not be deliberately kept open in order to assert one’s own interests. This puts private individuals and companies at risk. Instead, the BSI must proactively close security gaps and thus prevent cases like the Citrix security gap mentioned above. Patching must become mandatory and be enforced with laws. Those affected must be informed and supported.
Staffing of relevant authorities
The incredible shortage of personnel has also already been mentioned. The AG KRITIS is also calling for more specialist expertise for the BSI, BBK and THW with regard to IT components in critical infrastructures. Of course, this makes sense in view of the ongoing digitization of all areas of life and institutions. Accordingly, budgets would also have to be adjusted and continuous training would have to take place. Staff competition between authorities must be prevented. But above all, public authorities must become competitive with the free economy on the labor market. Every computer scientist knows that the public tariffs do not allow for anything like the same as in the free economy.
The Cyberhilfswerk (CHW)
In the event of major emergencies, it can of course still happen that not enough qualified personnel can be on site.
The KRITIS WG therefore proposes the establishment of a cyber aid organization named Cyberhilfswerk similar to the German Federal Agency for Technical Relief.
In the event of an emergency, it should be possible for the federal government or the states to send out an alert. Under no circumstances should the organization be used for offensive purposes or be called upon by the military or the armaments industry. This could lead to more insecurity than security.
Participation in the cyber aid organization should be voluntary.
Such a relief organization would of course be a great help in crisis situations. However, even then it is important to check the qualification and neutrality of the members.
The importance of cyber aid has also been recognized by politicians. The CDU, for example, included the demand in its government program for the coming years.
Open source deployment in the KRITIS environment
So far, it has not been addressed how dependent critical infrastructures in Germany are on various software vendors. In addition, the trustworthiness of some software companies is questionable.
A political demand for more security is therefore the use of open source software, as far as this is possible, and reliable software that can guarantee patches and security.
In addition, software for which the BSI issues recommendations should be freely available. This is important for secure operation on the one hand, and for the economic independence of security on the other.
National and International Defensive Cybersecurity Strategy
As mentioned above, the use of offensive weapons in cyberspace leads to increasing insecurity for critical infrastructure. A clear commitment and legal regulations in Germany and other countries would be necessary to reduce the risk. The KRITIS WG goes so far as to call for an international digital non-proliferation treaty, similar to the ABC non-proliferation treaty.
However, even without an agreement with other countries, Germany must fulfill its moral obligations and protect the civilian population of its own country and other countries by not using offensive weapons in cyberspace.
A common European defensive strategy could help prevent attacks on a large scale. A joint IT security situation center of European states, industry and research institutes could help and improve the exchange of information.
Ensure Accountability and Oversight
Let us now turn to the question of how to ensure that critical infrastructure operators adhere to the BSI’s specifications and do not save financial resources in the wrong places. According to § 8a BSIG operators of critical infrastructure are obliged to implement state-of-the-art security measures.To this end, critical infrastructure could be placed partly under government supervision and not left entirely in private hands. However, this is not possible in all areas of critical infrastructure.
It would therefore make sense to develop a control mechanism for each of the sectors. It is also important to ensure that the expansion of critical infrastructures in the future focuses on security and not on maximizing profits. Independent monitoring bodies must be set up to check this.
Patch Management and Responsible Disclosure
As already mentioned, the current law is missing a part which requires developers to release patches for security vulnerabilities. When such a gap affects critical infrastructure, it is fatal.
It is also necessary to create a legal obligation to make operators of critical infrastructure check updates and software distribution for integrity and trustworthiness. Patches must be able to be applied securely to ensure lasting protection.
Security agencies must treat known vulnerabilities responsibly and not withhold or use them for offensive attacks. The protection of critical infrastructure must be paramount. Responsible disclosure and remediation of vulnerabilities are necessary. But for this to occur, it must first be ensured that reporting vulnerabilities cannot bring civil or criminal penalties to individuals. Then, qualified individuals can be required to share security vulnerabilities with the BSI when they become known.
Companies that become aware of security vulnerabilities in critical infrastructures must then report them to the BSI as quickly as possible.
Does Germany have a problem?
After reading this article, it should be clear to everyone that things cannot go on like this. So far, it is more down to luck that no major IT-related incidents have occurred in the area of critical infrastructures, because the BSI’s recommendations, the minimum standards and their implementation are not checked by independent bodies. The BSI would hardly be able to cope with such a major incident with 15 employees. Civilian helpers are not available.
The threat is increasing. The number of attacks is increasing and examples abroad show how far-reaching the consequences of such attacks can be. It is not only in the economic interest of companies that critical infrastructure is well protected, but also in the interest of every individual to know that this circumstance will change in order to protect their own safety and, in case of doubt, their own life.
Politicians must act now. An independent BSI, sufficiently trained personnel resources and structures for crisis management must be put in place. Awareness of the relevance of open source and the importance of defensive and international security must be raised. Companies must be held responsible for making their products secure. It is not acceptable that risks are deliberately left open for consumers in order to maximize their own profits. Finally, operators of critical infrastructure must be supported but also supervised. They must be able to employ sufficiently qualified personnel and use the latest technology in terms of security. There are experts who are ready to support the policy in its implementation. You just have to recognize their relevance and listen. In any case, no one can now say they didn’t know the risk the next time a critical infrastructure is affected by hacking attacks.


Leave a Reply
You must be logged in to post a comment.