
Nowadays, the usage of mobile devices has become a part of our everyday life. A lot of sensitive and personal data is stored on these devices, which makes them more attractive targets for attackers. Also, many companies offer the possibility to work remotely, which results in storing confidential business information on private phones and therefore increases the organizations’ vulnerability. The following content shows what kind of attacks the mobile platform is facing and how secure we really are.
Introduction
Latest statistics show three different kind of types, which are mainly used by cybercriminals to infiltrate mobile devices.
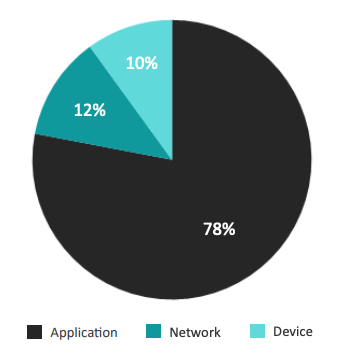
The most common and probably easiest way for attacker to access the phone’s data is via custom applications. Therefore their biggest challenge is to bypass the official App Stores, as most of the malicious apps are not able to pass through their security mechanisms.
Network attacks, for example a Man-In-The-Middle attempt, seem to be less successful, as well as attacks on the devices themselves, like using a security hole in the phone’s operating system.
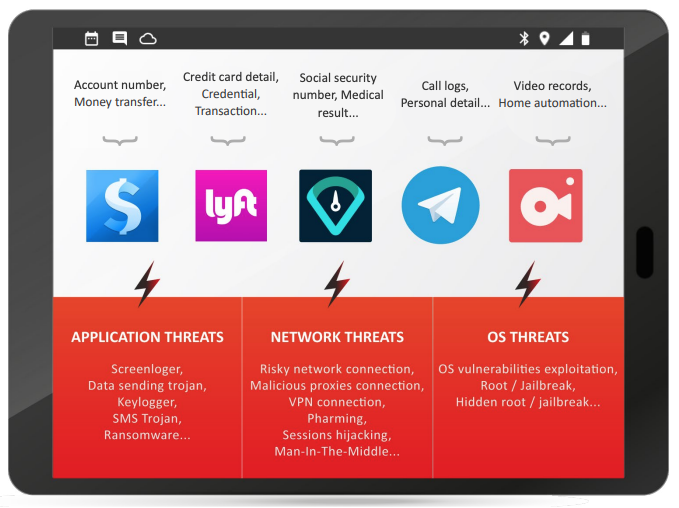
Before we take a more detailed look at the different types, let’s first consider various goals the attackers might have. As previously mentioned, confidential company data seems to be a very profitable reason. In general, most of the cybercriminal activity is driven by money [2], which is why account numbers, credit card details and banking credentials will always stay at the top of the attackers’ lists. However, some hackers might also seek for personal data, like social security numbers or even call logs.
Application Threats
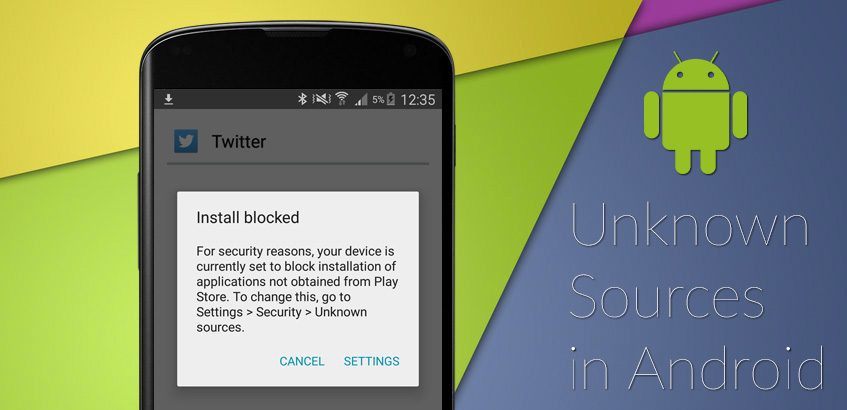
The amount of different application threats is massive: data sending trojans, ransomware and even mobile cryptomining are only a few examples of malicious applications. In average, there are about 60 to 90 apps installed mobile devices [3]. The most critical part is the origin of the apps. As the official App Stores from Google and Apple provide a high protection against malicious applications, more and more people start downloading apps from unknown sources, like third-party App Stores (Reasons for that will be discussed later). Both operating Systems – iOS and Android – include security mechanisms against such applications, which can be turned off by the user in the phone’s settings. Once turned off, there is no further check when installing and running an application. Therefore it’s important to keep in mind that this option should only be checked if the provider can be trusted.
Backdoors
A good example of malicious applications are the so called “backdoors”. Once installed, the app launches a background service, which runs constantly and redirects all network traffic through an encrypted tunnel to a third-party server. This service will stay active, even if the app is closed. Lately, several backdoor applications were noticed, on which the icon was removed after first open, which makes it very hard to uninstall the application [5].
But how do the attackers bypass the App Stores and get the users to install their app?
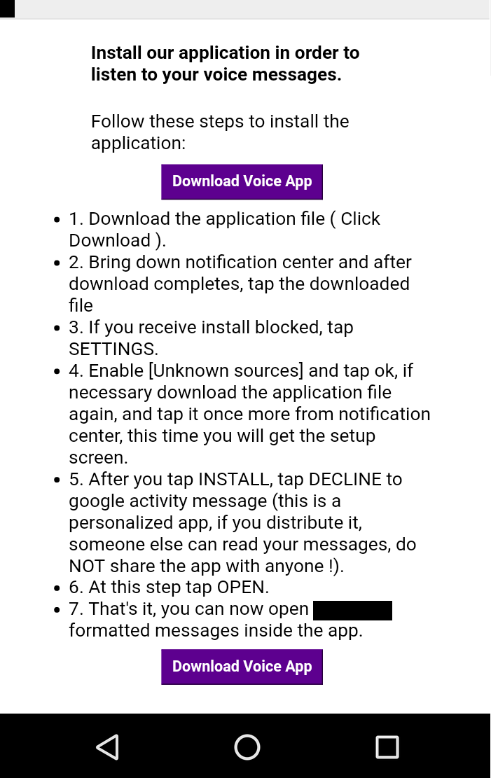
A good example is the Android TimpDoor Attack 2018: With a phishing campaign via SMS, the cybercriminals prompted users to download and install a “new voice app”. Within the message, there was a link with a description of how to download the file from a browser and thereby bypassing the App Store by allowing installation from unknown sources.
The application is completely fake, which means there is no working functionality inside. If the app is not directly uninstalled, it seems likely for the users to forget about it and never remove it from the phone, which then leads to an ongoing security issue.
Fakeapps
Another type of mobile malware is a Fakeapp. These are apps pretending to be original versions of popular apps like games, generating revenue through ad clicks or redirecting to other downloads. In order to be convincing, fake apps use original images, sounds and screens to pretend to be correct. Especially for fast growing and very popular games, fakeapps seem to be pretty profitable. In August 2018 for example, when the multi-player game Fortnite became popular and offered an invitation-only beta version of their mobile app, an extremely high rate of fakeapps was detected, as the users were eager to get access to that game. [LINK]
In the McAffee Security Report 2019 they say that “Fake Apps are and will be one of the most effective methods to trick users into installing suspicious and malicious applications in Android” [2].
More examples
This were only a few examples of mobile application threats. Mobile banking trojans are on the rise trying to steal credentials from banking apps. Also, while the digital currencies became popular, the number of mobile cryptomining apps has grown massively. Another example is the 33% increase of mobile ransomware infections within last year. Statistics show, that one in 36 mobile devices have high risk apps installed. While every day about 10.000 apps get blocked from the official App Stores, the attackers keep going to find new ways to bypass this security mechanism in order to spread their malicious applications on mobile devices. [6], [7]
Operating System Threats
Security holes in the code of an operating system are discovered from time to time. These holes can lead to a huge security risk and offer cybercriminals the ability to access the affected device. That’s why the companies need to act fast to provide proper security patches in order to get rid of these known vulnerabilities.
Unfortunately, nowadays these patches take too much time and a lot of devices with an outdated operating system version still exist, leaving them open for attacks. Here a clear difference between the Android and iOS Operating System is shown. Due to the fact that Android is distributed from many different manufacturers, these security patches take much more time than on iOS. Also because of that, new operating system updates need a lot of time to roll out for all the different devices on Android. A big majority of Android devices don’t run on the latest version which may include important security fixes.
Pradeo Lab [1]
The exploitation of an unpatched vulnerability can lead to system takeover and major data breaches
Statistics point out that one of the biggest Android problems is, that 76% of the devices run on an old version of its operating system. On top of that, the code of the Android OS is open source, which means the source code is visible to anyone. Cybercriminals can use that to gain access through security holes much more easier than on iOS, which is a closed system and therefore more complicated for hackers to find vulnerabilities in the operating system.
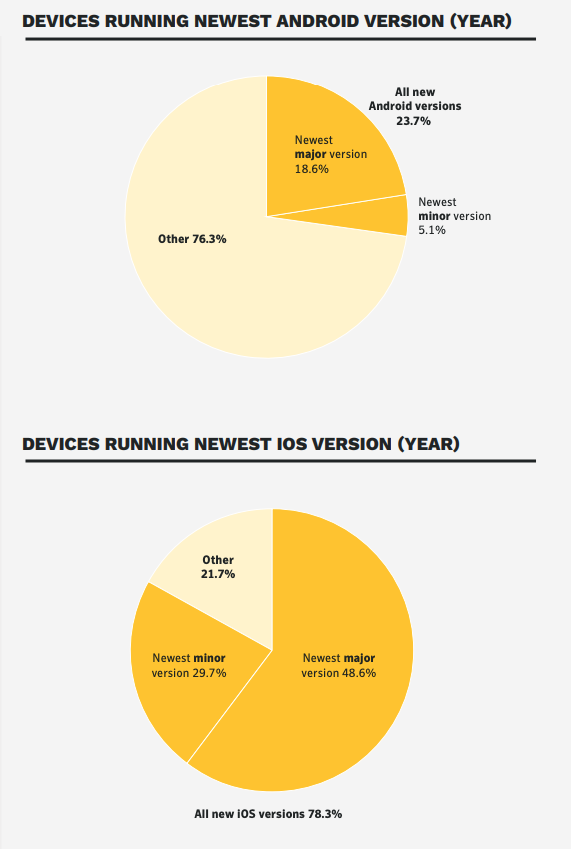
Source: [7], p.43
Network Threats
Network threats occur less frequently than application threats, but the numbers are growing. Security reports keep warning from unsecure Wifi Hotspots, which could be easily used for criminals to steal information, for example by Man-In-The-Middle attacks.
Latest statistics show an increase of three times the usage of public hotspots since 2016 and they predict even higher numbers for the next years [1]. Lately, there have also been attacks, where hackers used the wifi connection to distribute malware [8]. Although this sounds intimidating, protection is guaranteed by turning off file-sharing across the network.
Another fast growing network threat is phishing, which is known for a long time, happening mostly via email traffic. This area has also shifted to the mobile sector, targeting people via SMS (smishing). These phishing attacks attempt to steal ones’ personal data by tricking users to download malware or leading them to fake sites, on which they will be asked for personal information.[9]
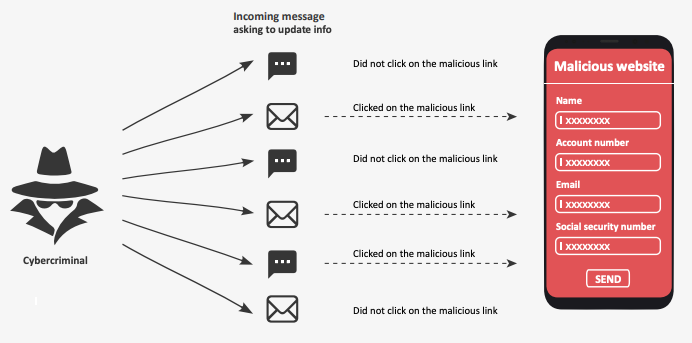
The best protection against phishing is to always double check the messages. Does it come from a number I know or is this a suspicious number? No institution would send a SMS with a link to enter confidential information. If not sure, best rule is to better not respond to the message and not click on any links inside it.
What can we do?
There are several providers for mobile security software, which can be downloaded in the App Stores. Unfortunately, most of them are related to costs and less people are willing to pay for that. On top of that, you can never be completely sure, that all kind of attacks will be prevented by such software. Although this might be interesting for companies who offer their employees business phones to secure their business data.
As a rule of thumb you should always keep in mind to only use the official App Store for downloading apps. If, for some reason, you get requested to download an app outside the official App Store, always question yourself whether this is really necessary.
An obvious point is to regularly update your operating system, if you receive new updates. Here, an improvement is needed, as the manufacturers should provide security patches and system updates much faster, especially for Android.
One last point to mention are runtime permissions: Every application has to request permission access in order to use certain functionality of a device, for example camera or microphone. You do not always have to grant permissions, ask yourself why the app needs access to the requested functionality and get suspicious if you do not see any reason.
Conclusion
Mobile security is a topic which requires a continuous work, as malware increases and cybercriminals find new ways to attack devices. Especially these days, with Internet of Things (IOT) and an increase of networking between all different kind of gadgets, the smartphone we use everyday represents a huge target, as it has the ability to control them all.
Upcoming topics like mobile payment or medical data on the phone will result in an even bigger interest for hackers.
After all it’s sometimes enough to raise the users’ awareness of the threat against smartphones, so that less people get tricked by phishing attacks or malicious app downloads.
References
[1] Pradeo Lab, Mobile Security Report, February 2019
https://www.pradeo.com/media/Pradeo_mobile_threat_report_S12019.pdf
[Accessed 02 August 2019]
[2] McAfee Mobile Threat Report Q1, 2019
https://www.mcafee.com/enterprise/en-us/assets/reports/rp-mobile-threat-report-2019.pdf
[Accessed 02 August 2019]
[3] 9To5Mac, The average smartphone user spends 2h 15m a day using apps – how about you?
https://9to5mac.com/2017/05/05/average-app-user-per-day/
[Accessed 02 August 2019]
[4] Applivery, Allowing app installs from Unknown Sources in Android
https://www.applivery.com/docs/troubleshooting/android-unknown-sources/
[Accessed 02 August 2019]
[5] McAffee, Android/TimpDoor Turns Mobile Devices Into Hidden Proxies
https://securingtomorrow.mcafee.com/other-blogs/mcafee-labs/android-timpdoor-turns-mobile-devices-into-hidden-proxies/
[Accessed 02 August 2019]
[6] Kaspersky, IT threat evolution Q1 2019. Statistics
https://securelist.com/it-threat-evolution-q1-2019-statistics/90916/
[Accessed 02 August 2019]
[7] Symantec, Internet Security Threat Report, Volume 24
https://www.symantec.com/content/dam/symantec/docs/reports/istr-24-2019-en.pdf
[Accessed 02 August 2019]
[8] Kaspersky, How to Avoid Public Wifi Security Risk
https://www.kaspersky.com/resource-center/preemptive-safety/public-wifi-risks
[Accessed 02 August 2019]
[9] Kaspersky, What is Smishing and How to Defend Against it?
https://www.kaspersky.com/resource-center/threats/what-is-smishing-and-how-to-defend-against-it
[Accessed 02 August 2019]

Leave a Reply
You must be logged in to post a comment.