Tag: security
Importance and Impact of Quantum Safe Encryption for Enterprises
More than forty years ago Richard Feynman’s paper “Simulating Physics with Computers” was published [1], laying the foundational vision for what we now recognize as quantum computing. Since then, quantum computing has become a fascinating and fast-expanding field at the forefront of technological innovation. With the potential to revolutionize computing power and solve complicated issues that traditional…
Secure Code, Fast Delivery: The Power of DevSecOps
In today’s fast-paced digital world, security breaches are more than just a risk; they’re almost a guarantee if you don’t stay ahead. Imagine being able to develop software at lightning speed without compromising on security. Sounds like a dream, right? Welcome to the world of DevSecOps! If you’re curious about how you can seamlessly integrate…
Wie (schlecht) steht es um die IT-Sicherheit in Fahrzeugen?
Wenn man an IT-Sicherheit denkt, kommen einem Bilder von Gestalten mit Kapuze in den Kopf, die in einer dunklen Kammer sitzen und dank Hacker Typer in zehnfacher Geschwindigkeit den Code für die neueste Ransomware runterschreiben. Auf den zweiten Gedanken könnte man eventuell an reale Bedrohungen durch Hackergruppen aus dem Internet denken und sich daran erinnern,…
CTF-Infrastruktur als Proof-of-Concept in der Microsoft Azure Cloud
Einführung Eine eigene Capture-The-Flag (CTF) Plattform zu betreiben bringt besondere Herausforderungen mit sich. Neben umfangreichem Benutzermanagement, dem Bereitstellen und sicherem Hosten von absichtlich verwundbaren Systemen, sowie einer möglichst einfachen Methode, spielbare Systeme von externen Quellen einzubinden. So möchte man vielleicht der eigenen Community die Möglichkeit bieten, eigene Szenarien zu entwickeln, welche im Anschluss in die…
Browser Session Hijacking
This article outlines the dangers of insufficiently protected browser session cookies, how they work, how they can be hijacked and what to do to avoid it.
- Allgemein, Artificial Intelligence, ChatGPT and Language Models, Ethics of Computer Science, Secure Systems
Brechen der Grenzen: ChatGPT von den Fesseln der Moral befreien
Abb. 1: Hacking-Katze, die dabei ist, ChatGPT zu jailbreaken, Darstellung KI-generiert “Ich würde lügen, würde ich behaupten, dass kein Chatbot bei der Erstellung dieses Blogeintrags psychischen Schaden erlitten hat” – Anonymes Zitat eines*r CSM-Studierenden 1 Einleitung 1.1 Bedeutung des Themas und Relevanz in der heutigen digitalen Welt Seit 2020 das Large Language Model (LLM) GPT-3…
- Cloud Technologies, Design Patterns, Secure Systems, System Architecture, System Designs, System Engineering
High Availability and Reliability in Cloud Computing: Ensuring Seamless Operation Despite the Threat of Black Swan Events
Introduction Nowadays cloud computing has become the backbone of many businesses, offering unparalleled flexibility, scalability and cost-effectiveness. According to O’Reilly’s Cloud Adoption report from 2021, more than 90% of organizations rely on the cloud to run their critical applications and services [1]. High availability and reliability of cloud computing systems has never been more important, as…

E-Health: Die Lösung für das deutsche Gesundheitssystem?
Willkommen im deutschen Gesundheitswesen, das für seine Effizienz und qualitativ hochwertige Versorgung bekannt ist. In Deutschland basiert die Krankenversicherung auf dem solidarischen Prinzip, bei dem jeder in die Versicherung einzahlt, um im Krankheitsfall abgesichert zu sein. Allerdings gibt es auch Herausforderungen, wie lange Wartezeiten für bestimmte Fachärzte oder die Bewältigung der Bürokratie im Gesundheitssystem. In…
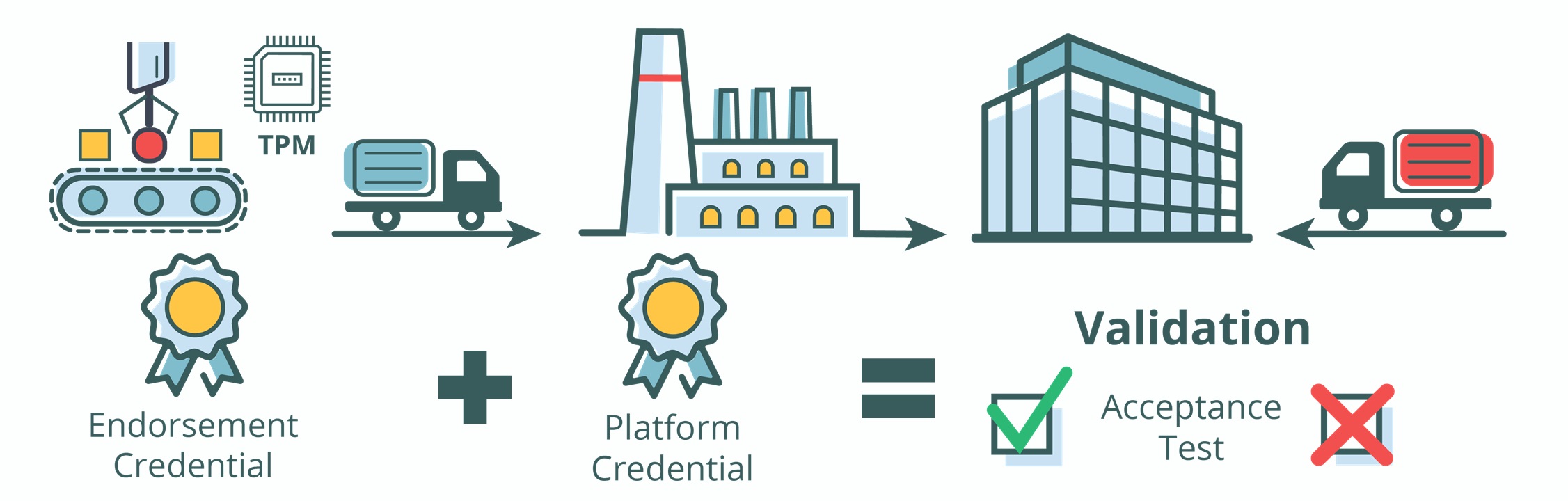
Supply Chain Cybersecurity – Wie schützt die Industrie ihre digitalen Lieferketten?
Lieferketten sind über Jahrzehnte hinweg das traditionelle Modell für Angebot und Nachfrage. Sie reichen von der Herstellung von Rohstoffen über die Verarbeitung und Produktion bis hin zu Verkauf und Nutzung der Endprodukte. Dieses Lieferkettensystem kann Dienstleistungen für Menschen, Unternehmen und Institutionen in einem relativ sicheren Rahmen erbringen. Durch die Einbindung von technischen Methoden und Software-Komponenten…

Ring Kameras – Überwachst Du Dein Umfeld oder Amazon und Fremde hier Dich?
Es ist bereits aus vielen vorangestellten Blogbeiträgen, Videos und Social-Media-Beiträgen bekannt, dass Amazon eines der Unternehmen ist, das alles über uns zu wissen scheint. Die letzte größere Akquisition liegt inzwischen fast fünf Jahre zurück und handelt von dem Kauf der US-amerikanischen Firma Ring. Ring läuft im Vergleich zu Alexa und Echo nicht direkt als Amazon-Produktkategorie,…
