 This paper provides an overview on the most important types of botnets in terms of network topology, functional principle as well as a short definition on the subject matter. By exploring the motivation of botnet operators, the reader will gain more insight into business models and course of actions of key players in the field. Furthermore, essential botnet modules, major important roles and infection vectors will be discussed in order to provide an overview. This paper will also treat the hiding, detection, as well as the decommissioning of botnets. Moreover, it will be discussed in what sense botnets may be considered as resilient systems and what estimations about countermeasures can be taken in order to tackle future developments in the field of botnets.
This paper provides an overview on the most important types of botnets in terms of network topology, functional principle as well as a short definition on the subject matter. By exploring the motivation of botnet operators, the reader will gain more insight into business models and course of actions of key players in the field. Furthermore, essential botnet modules, major important roles and infection vectors will be discussed in order to provide an overview. This paper will also treat the hiding, detection, as well as the decommissioning of botnets. Moreover, it will be discussed in what sense botnets may be considered as resilient systems and what estimations about countermeasures can be taken in order to tackle future developments in the field of botnets.
This document has been converted from a LaTeX pdf file to WordPress. Despite a manual review, there may still be conversion errors.
Therefore, the original file can also be downloaded here.
1 Introduction
ENISA, the European Union Agency for Network and Information Security, which publishes a report on the currently emerging threats each year, calls botnets the number two thread, in its most recent issue. (see ENISA Threat Landscape 2015 — ENISA 2016)
 Figure 1.1: ENISA: Emerging threats
Figure 1.1: ENISA: Emerging threats
Terrifying enough, this ranking does not tell the whole story. What is not explicitly mentioned in the list is, that botnets are often the reason for many other threats like malware, that gets delivered by botnets. The same applies for identity theft, which is frequently managed by botnets, web based attacks, being actively spread to other servers by botnets and even phishing sites, which can be hosted and automatically generated by the forementioned.
Thus, to the present day the real impact of botnets is hard to value and meassure correctly. Above all, it is clear that botnets are further growing and will be more difficult to stop over time, as it will be demonstrated in this paper.
With five million computers worldwide belonging to the 10 top botnets in 2010, the number of undiscovered infected machines can only be guessed. (see Kassner n.d.) If taken into account, that the FBI stated in 2014, that each second, 18 computers get infected by botnets, this leads to 500 million compromissed machines a year. (see Khandelwal 2014)
Compiling this information together with the forehand mentioned latest ENISA rankings, the resulting numbers are simply mindboggling.
1.1 Definition
One of the more complete descriptions of what a botnet is, has been given by Stevanovic et. al. in their paper “A Collaborative Approach to Botnet Protection”. He states that “[b]otnets are collections of compromised computers which have come under the control of a malicious person or organisation via malicious software stored on the computers, and which can then be used to interfere with, misuse, or deny access to a wide range of Internet-based services”. (see Stevanovic, Revsbech, Pedersen, Sharp & Jensen 2012)
1.2 Necessary steps to start a botnet
After gaining some knowledge on the general definition of what a botnet is, it is helpful to look into the mechanics of the subject matter. To get a deeper understanding of a botnet’s modus operandi is, we will take a look at the necessary steps, it has to undergo in order to perform its tasks.
A typical bot exhibits three invariant features along its onset:
- The startup of a bot is automatic without requiring any user actions
- A bot must establish a command and control channel with its botmaster
- A bot will perform local or remote attacks sooner or later (see Liu, Chen, Yan & Zhang 2008)
These steps will be mentioned again later, as they are crucial for detection and deception techniques of botnets and in order to understand their overall concept.
2 Purposes of botnets
In order to understand why botnets pose such a huge threat nowadadays, it is important to have a deep knowledge of what the motivation of its operators are.
2.1 Motivations
2.1.1 Money
There exists a vast variety of motivations for people to create botnets, most of them are dealing with the question how to make money over the internet by exploiting others’ peoples ressources, bank accounts etc.
As Yury Namestnikov, with Securelist expresses it, “[i]n the past ten years, botnets have evolved from small networks of a dozen PCs controlled from a single C&C (command and control center) into sophisticated distributed systems comprising millions of computers with decentralized control. Why are these enormous zombie networks created? The answer can be given in a single word: money.” (Namestnikov 2009)
2.1.2 Power
Nevertheless there are also other reasons to use or build a botnet which are not linked to financal interests directly. Besides the latter, various state or non-state actors are using botnets for military matters.
State-actors
As war is described to be “the continuation of politics by other means” (von Clausewitz 1989, p.87) by Carl von Clausewitz, it can be noted that botnets are the continuation of war by means of information technology. In the center of using botnets as a medium of war, state actors play a huge role. As a military technique, botnets have the advantage of being hard to track down (see Greenemeier n.d.) and to be very cost effective (see Nappa, Fattori, Balduzzi, Dell’Amico & Cavallaro 2010). States can attack one another in guerilla warfare style and pretend to be completely clueless.
One of the best known incidents has been the DDoS attack on Estonia (see Florian 2007), which was allegedly commited by Russian hackers, what could indeed not be proven with certainity. (see mba & vbr n.d.) (see Security n.d.) So this may also be subject to someone making wrong accusations.
False flag attacks
Besides these very obvious incitements, it is als very likely that so-called ‘cyber attacks’ are used as a tool for false flag attacks, because many state actors are often eager to give its citizens reasons to impose war on other countries. Whilst this fact is hard to bring to prove, going along the historic timeline, examples like the Gulf of Tonkin incident (see Greenspan n.d.) and the lies about Weapons of Mass Destruction that led to Iraq war (see Chulov & Pidd 2011) are just a few famous and well documented examples of outright lies or false flag attacks, that serve as a proof of concept for this kind of forming the public opinion. So a false flag cyber warfare case like proposed here, is logically almost unavoidable to happen, if it was not already the case.
Non-state actors
Alongside these state-actors there are also other organizations that share a slightly different scope of interests. Among these are associations conducting organized crime for various reasons, terrorist groups that sometimes have monetary, but also ideological reasons for commiting internet crimes.
State actors against non-state actors
In the case of 2014’s botnet XSSer, the Chinese government was accused to have been sending a link via SMS, pointing to a malicious trojan in order to undermine protests in Hongkong. After downloading and automatically executing the software, it could “[g]rab SMS history, call logs, GPS/location info, phone browser and email history, phone’s file listing; send incoming & outgoing phone call recordings and audio recordings; run shell commands received on phone; download, upload or delete files; display a notification” (see Nigam & Grooten (Editor) 2015)
The text sent out via SMS, said
“Check out this Android app designed by Code4HK, group of activist coders, for the coordination of Occupy Central!”. (Bisson 2014)
Nevertheless, this text could also make the impression of looking way too obvious for someone getting this message from an anonymous cell phone number.
So it still is a matter of belief, if the Chinese government would be using techniques like these, instead of more covert ones, as even dictatorial regimes are usually frightened of backfiring. Even the Command and Control servers running under Chinese TLDs (Top Level Domains) and the source code being in Chinese do not prove anything unfortunately. (see Bisson 2014)
2.2 Technological methods and varieties
Whilst the prior section listed the most important actors in the field of cyber crime, it will now be discussed what particular methods and varieties are most often used in botnets. Nevertheless, it is beyond the scope of this paper to take in account all the various forms that botnets may have, which is due to the highly dynamic nature of botnets. These are constantly changing their forms as they are capable of downloading code at runtime and applying patches to the infected machines.
Most botnets are furthermore not only capable of using one technique alone, but use a mix of different methods instead. One and the same botnet can for example send out spam from an infected computer, but also wiretap the victims key strokes using a key logger and run DDoS attacks at the same time. Botmasters have usually a control panel to start certain actions, that are then send as commands to the infected bots, which figure 2.1 shows.
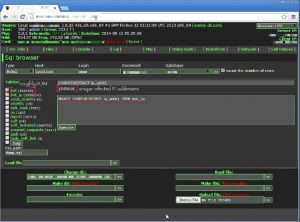 Figure 2.1: Control panel of a botnet Qbot
Figure 2.1: Control panel of a botnet Qbot
2.2.1 Spam
Sending spam is one of the key objectives of many botnets, which can be pointed out well by the example of botnet Grum, that was believed of being responsible of sending out 18% of the world’s spam mails in the year 2012. (see Huge spam botnet Grum is taken out by security researchers – BBC News 2012)
In 2011, another botnet, called Rustock was put out of action by Microsoft (see Editor 2011). To this date, it has been the most active spam botnet responsible for one third of world’s spam e-mails.(see Security 2011)
These examples demonstrate nicely what great of a portion even one botnet can represent. Starting from this point, one can simply approximate the number of spam mails that other botnets should be responsible for.
Rustock was furthermore amongst the 10 botnets, that are responsible for sending out 80 percent of the world’s spam volume, consisting of 135 billion spam emails sent out in one day alone. (see Kassner n.d.) For spammers, botnets are key, because without this technology it would be extremely hard to operate in the way they do at the moment. (see Security 2011)
In this case the simple nature of e-mail protocols like sendmail, which doesn’t even check if the server sending out a message from an email address (e.g. alice@microsoft.de) does really belong to microsoft.de. Therefore it is extremely simple to fake emails by simply logging into an unprotected server offering sendmail access via telnet on port 25. (see How to Send Email Using Telnet n.d.) Every imaginable address can now be faked and sent out by the spammer. But even if there is no such unprotected server around, other infected bots can simply be commanded to download a patch from any Command and Control server and install a mailing software. This makes them automatically servers, which are capable of sending out spam mails now.
It is very unlikely that this situation, concerning the vulnerability in the fundamental structure of e-mail will change, wherefore it can be stated that spam will be a continuing problem, at least in the mid-term.
2.2.2 Bitcoin mining
Bitcoin mining is another branch for cyber criminals in order to make money by using infected computers of innocent victims. The host systems are used to secretly mine bitcoins * on their machine. There are even affiliate programs, that pay “people for the mass installation of programs that turns host machines into bitcoin mining bots”, as botnet “Botcoin” does for example. (see Krebs 2016)
This is an example that demonstrates in an interesting way, how the commercialization of infected PCs gets increasingly more professional, tending towards solutions like “Pay-Per-Install, which will also be discussed in this chapter.
Bitcoin mining is nowadays more of a standard business model for botnets to generate money in a criminal way. Although, there even exist the “Miner Botnet”, indicating it would solely serve this very purpose, it is also a multifaceted piece of software as Plohmann and Gerhards-Padilla point out in their “Case Study of the Miner Botnet”. (see Plohmann & Gerhards-Padilla 2012)
*(Bitcoin is a “peer-to-peer system for online payments that does not require a trusted central authority” (Bitcoin simplified. n.d.) )
2.2.3 Stealing bitcoin wallets
Bitcoins as well as other digital currencies can be stored in so-called bitcoin wallets, which are also one objective of botnets. In case they are not encrypted and secured with a password, botnets like “Pony” try to steal those cryptocurrencies from there. (see Bitcoin-stealing virus infects thousands of PCs 2014) Needless to say, that there are plenty of botnets working in a similar way.
2.2.4 Password stealing
In case there is software on the computer that stores password in themselfes, botnets also try to target this vector. In the case of a version of Kelihos botnet for instance, the malware was able to steal passwords from various applications on the infected host computer. To name just a few famous ones, Kelihos tried to gain access to passwords safed in Internet Explorer, Mozilla Firefox, Chrome as well as various FTP client applications. (see Adamov 2013)
2.2.5 Password cracking (internet privacy / identity theft)
There are also other kinds of attacks involving passwords, but happening solely online. Cracking passwords of online accounts, such as e-mail, online shopping, banking etc., is also a very profitable way of making money, due to the fact that computing power or network bandwidth doesn’t cost the botmaster anything.
Attacks like these are usually plain brute force attacks, which means that even if the e-mail address of a potential victim is known, the password has to be guessed. Simple brute force attacks just try out every character from a to z and 0 to 9 and then add another character to this possible password. That way it evolves from a to aa to aaa and so on, until it will reach zzzzz or similar.
Although these ancient techniques of testing out passwords are still used, it is likely that dictonary attacks and a sorting towards the most used passwords on the internet are also carried out on top of that. In 2013 “password” and “123456” were still the most common ones. (see Gray 2013)
2.2.6 Blackmailing
Offline
While Locky is not an actual botnet, its software is delivered by one instead. The malware got huge media coverage, when it infected up to 60.000 within 24 hours day by day. (see Cimpanu 2016b) Locky’s way to make money is to encrypt a victim’s hard drive as well as all shadow copies found and to blackmail the users afterwards, asking to transfer money in form of bitcoins to the criminals in order to unlock their drive again. (see Harbison 2016)
Online
There is also an online form of a blackmailing using DDoS (Distributed Denial of Service) attacks, where a webpage (usually a web shop) is overload with pointless queries from different computers. The internet shop’s operator now receives an e-mail from the blackmailer, pressurizing him to send a certain amount of money to his bank, paypal or bitcoin account. Unless the money is transferred, the DDoS attack won’t stop and the webshop cannot be used to sell goods, which could lead to a loss of a large amount of money. In 2014 there were also cases of Evernote as well as RSS reader Feedly, being strong-armed by criminals that way. (see Cluley 2014b)
Instead of blackmailing for monetary reasons, this kind of attack can also be politically motivated. One of the most well known politically motivated attacks using DDoS attacks, was the raid on Paypal, Mastercard and others, which was seen as an answer to their behvaviour of freezing Wikileaks’s banking accounts for political reasons. The attack is better known as “Operation Payback” (see Mutton 2010).
2.2.7 Pay-Per-Install
Botmasters also provide an interesting B2B (Business-to-Business) model, where they infect and herd an amount of bots, in order to install software of a third party on them. As security expert Brian Krebs states, “[c]lients submit their malware—a spambot, fake antivirus software, or password-stealing Trojan—to the PPI service, which in turn charges rates from 7to180 per thousand successful installations, depending on the requested geographic location of the desired victims.” (Krebs 2011) In the same article of MIT Technology Review, he also claimed that in 2011, most of the Malware was tied to the PPI market. (see Krebs 2011)
This case of application shows clearly, how professional the botnet scene grew to the present day, as their offers are very similar to amazon’s cloud services. According to Finjan, a security firm, advanced trading platforms like “Golden Cash network” – which is indeed very similar to most recent plattforms -mark “a new milestone in the cybercrime evolution”. (Mills n.d.)
2.2.8 Illegal SEO and click fraud
Webmasters are always eager to push their websites up in the ranking of search engines like Google, because visits to their page mean hard cash for them. So there are understandably attempts of criminals to change page ranking positions in search results. Some years ago, Google used to count the links pointing to a site in order to meassure how important it was and also valued how the link was called (e.g. “buy a computer” or “buy your computer” lead to different rankings) to generate its ranking. (see Namestnikov 2009)
Although it is not clear, what exact algorithm Google uses nowadays, it is still possible to trick it, may it even be by searching and visiting a website with a bot.
Illegal SEO can also be done by posting fake comments in internet forums, linking to a website or just advertising a product directly, which leads to the closely related “Click fraud”. (see Security 2016)
Click fraud
A very similar use of bots is a technique called “Click fraud”, where automated scripts are used in order to fake clicks on pay-per-click (PPC) advertisements. That way, the person getting paid for hosting ads on his webpage, gets paid more, but is also accruing higher costs for the advertiser on the other hand. (see What is Click Fraud? – Defi from Techopedia n.d.)
3 Types of botnets
There exist various types of botnets in the wild nowadays, but there has been a historic evolution of architectures. On this account, we will look deeper into the three main structures, which are Centralized, Peer-to-Peer and Layered Peer-to-Peer.
3.1 Centralized, traditional client-server-botnets
In centralized server architectures, the infected computers, called “bots” are always contacting the C&C (Command and Control) server in order to get new commands. These commands were previously sent out by a “botmaster”, being the operator of the network. A more detailed description on these roles will be found in chapter “Functional principle”.
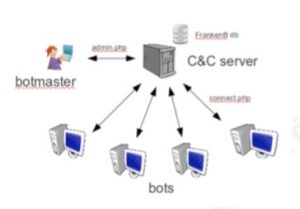 Figure 3.1: Example for a centralized botnet
Figure 3.1: Example for a centralized botnet
A very interesting fact, that resolves a lot of the mystery around botnets, is that – as stated in the introduction – malware and botnets are not clearly separatable. This is due to the fact, that the latter directly stems from the prior one, which Plohmann and Gerhards-Padilla illustrate aptly.
“The concept of botnets originates from the idea of enhancing malware with the ability to connect back to a server upon infection. First known cases of centralised botnets appeared in 1998/1999 and are tied to the so-called “Global Threat Bot” (GTBot), the remote access toolkit SubSeven and the email worm PrettyPark [2].” (Plohmann & Gerhards-Padilla 2012)
The idea of this structure was simply born out of the idea, to make malware infections as well as control etc. more interactive.
3.2 P2P
It is almost obvious, that purely centralized client-server architectures have the inherent disadvantage, to be taken down relatively easily. By just attacking or overtaking the Command and Control server, an individual can put himself into the position of the botmaster and overtake the whole botnet. It was mainly out of this reason, that the Peer-to-Peer botnets evolved.
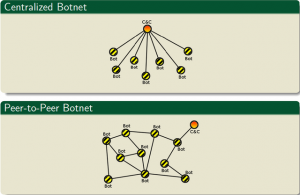 Figure 3.2: Evolution from centralized to Peer-to-Peer botnet
Figure 3.2: Evolution from centralized to Peer-to-Peer botnet
In a P2P botnet topology, usually each peer acts as a client and a server. (see Scanlon & Kechadi 2012) However, concerning botnets this is not exactly the case, as the bots are instead able to communicate with each other now. This means, that a bot can tell another one about a new C&C server or that the former server has moved for instance. This gives the botnet a higher resilience, because single bots cannot be disconnected from the botnet that simple any more.
3.3 Layered Peer-to-Peer
The last step of evolution is an additional layer that is placed inbetween the Command and Control server(s) and the bots.
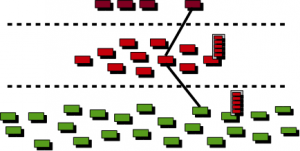 Figure 3.3: Layered P2P botnet. C&C servers on top (dark red), proxy bots inbetween (red) and harvester bots on the bottom (green).
Figure 3.3: Layered P2P botnet. C&C servers on top (dark red), proxy bots inbetween (red) and harvester bots on the bottom (green).
This so-called Proxy layer serves the purpose of providing and extra layer of security for the botmaster. As this layer shields the C&C servers from the bots, there is no possibility of a direct connection between them. Because the last thing a botmaster wants to do is to be tracked down by law enforcement using a direct connection, he can simply hide behind this security wall and send out his commands directly to the C&C servers only.
Resulting from this, law enforcement has a very hard job in taking down a botnet, because every bot may have different C&C servers and in some botnets there are also methods used which enable bots to carry out an information exchange between them.
So when one of the bots is unreachable, or finds out by itself, that somebody tries to shut him down, he sends a signal to another bot. This rings an alarm that informs the C&C server and the other bots. Depending on that, the botmaster can split the botnet up into several portions, change the encryption scheme for the bots, change passwords or simply move the botnet with one click. But there are plenty more actions he can take.
The following figure illustrates the same structure as shown in the prior figure, but a little bit more detailed.
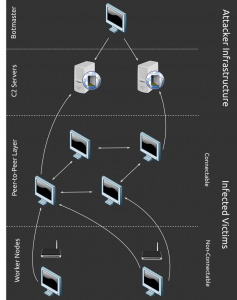 Figure 3.4: Layered P2P botnet. Commands go top down from botmaster, through C&C servers and Proxy (P2P layer) to the Worker Nodes (bots)
Figure 3.4: Layered P2P botnet. Commands go top down from botmaster, through C&C servers and Proxy (P2P layer) to the Worker Nodes (bots)
The C2 Servers in the image have been called C&C servers before, the Peer-to-Peer Layer is alternatively named Proxy Layer and Worker Nodes can also be called bots, harvesters or zombies. Computers in the Proxy Layer and Worker Nodes do not differ in their physical appearance, which means that they can also change their role. One minute an infected machine can be a bot and in the other minute, he serves as a Proxy.
Needless to say, that this renders attempts of getting an overview on the botnet nearly impossible. By gaining this new functionality of flexible response to changes in network availability, the botnet increases its resilience once more.
3.4 Platforms and manifestations
After having gained an overview on the network topologies of botnets, it is interesting to know where they are to find in the physical world, meaning which devices they are able to infect. In simple terms, it can be said that botnets are able to infect virtually every device and operating system we now.
In the paper “A Mobile Botnet Model Based on Android System” of Wang et. al., a mobile botnet model based on the Android operating system is demonstrated. (see Wang, Zhang, Li & Zhang 2013)
Another paper of Lee et. al. shows by the example of their bot “Punobot”, the possibility of building a user-hidden communication channel to a C&C server using Android push notifications. (see Lee, Kang, Lee, Kim & Kim 2013)
Claims and rumours of Apple’s Mac OS X being immune against botnets and malware of all kind, can once again be rejected by a heap of examples. (see 17,000 Macs infected with botnet controlled via Reddit n.d.) (see Cluley 2014a) (see Musil 2012)
The same applies for Linux machines, where there have also botnets been found. (see Cimpanu 2016a)
One of the most pictografic examples in this field may be the case of a large botnet of CCTV devices, who were ordered by their botmaster to attack a jewelry website. (see Goodin 2016) By demonstrating that even the devices to provide security can obviously not be protected, it has furthermore to be noted that IoT (Internet of Things) might not be a good idea at all.
4 Functional principle
4.1 Integral parts of a botnet
4.1.1 Command and Control server
The command and control server sends out commands to the bots he knows. This may be for instance a DDoS attack on a internet site hosting a webshop in order to blackmail it, or just a command to send out spam etc.
In more recent botnets, there is usually more than one Command and Control server, to make the network harder to take down. It is also more complicated to detect all sub parts of the botnets, if each subnet is contacting different C&C servers, which is due to the fact that law enforcement agencies often try to attack C&C servers as a single point of failure. From this point on, they then follow the chain of command in a top-down manner and identify the bots. But if the bots on the other hand are not contacting this C&C server, but another one instead, it is not possible to find the other bots from the second subnet.
These multiple C&C servers also exist due to the fact that there has to be some resilience against DDoS attacks, when an attacker just wants to take down a network using brute force. In this case, a second Command and Control server steps into place where the first one was.
4.1.2 Bot
A bot is the bottommost computer in the chain of command of a botnet. It receives its commands by one or more Command and Control servers, that are enlisted in its peer list *, nowadays also reached over a middlesman, in order to hide the former.
Standard personal computers, in a botnet also called ‘zombies’ were most often the target for a botnet to install its code on. Nevertheless, nowadays botnets increaslingly tend to use web servers for this issue, as they are always online, have more network bandwidth, more computing power and can’t be blacklisted that easy (see Barnett 2010). These were all properties, why botmasters used web servers as Command and Control servers in the past.
- (See section peer list in this chapter)
4.1.3 Botmasters / Herders
A botmaster is an individual that sits on top of the entire botnet structure and sends out his commands to the Command and Control servers. These are then delivering them to the bots, which are executing the commands subsequently.
The figure above shows by the example of botnet QBot, how the control, that a botmaster is operating looks.
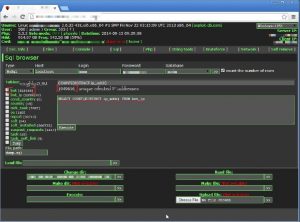 Figure 4.1: Administration Panel
Figure 4.1: Administration Panel
4.1.4 Optional: Intermediate P2P layer / Proxy layer
In the last section about botmasters, we used the simplest of approaches to describe a botnet. However, more up-to-date botnets tend to use an intermediate Peer-to-Peer layer in order to conceal the connections between bots and the Command and Control servers. Acting that way, the command recieving machines never have to contact the botmaster’s servers directly, which adds an extra layer of security to the system, working in the sense of criminals. (see Andriesse, Rossow, Stone-gross, Plohmann & Bos n.d., p.2)
Figure 4.2 shows, how bots, also called zombies or harvesters in the P2P Layer, communicate with the C&C servers in C2 Layer by routing through C2 Proxy Layer. This happens in order to ensure that there is no direct connection between bots and C&C servers as well as the botmaster.
4.1.5 Sniffing and scanning module
Sniffing and scanning traffic in the surrounding network is one of the core objectives of a botnet. François Bégin reconstructs that communication pattern in his paper “BYOB:
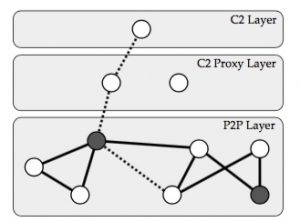 Figure 4.2: Topology of P2P Zeus
Figure 4.2: Topology of P2P Zeus
Build Your Own Botnet and learn how to mitigate the threat posed by botnets” how bots discover the net around them in a practical manner. By building his own botnet, he notes that “[w]ith bots now reporting in to the FrankenB C&C, the true purpose of a botnet can start to reveal itself: compromising data and exploiting hosts. “ (see Bégin 2011, p.18)
Right after the step of scanning and discovering new machines in the surrounding network, the bot starts looking for vulnerabilities within the computers he found. It does so in passively sniffing the network traffic, that is automatically sent to all machines in the network.
4.1.6 Infection module
Based upon the scanning and sniffing process, the botnet starts its next step of infiltration. So called exploits are used, which are vulnerabilities that can be used in a programmatic and repeatable way. For instance, there can be a vulnerabiliy of a FTP program that stops working correctly when a “/0” command is sent on port 21. In an exploit this bug is now utilized as an implementation of a piece of source code. Using this, the bot is now able to use the vulnerability, meaning that he can contact the FTP server on that given port and send out the “/0” signal, when the command of a botmaster reaches the bot. When we now assume that it is possible for logged in users to gain root privileges, because of the FTP program’s bug, this behaviour can consequently triggered by firing the exploit, just pushing a button on the botmaster’s control panel.
More simple infection
In the beginning of 2014, the most common delivery methods for infections were:
- Hosting of malicious binaries on filehosters like com, copy.com, while the download links were send by email.
- Malicious Microsoft Word or Excel files being sent in spam emails as attachments, containing a macro that directly downloads the
- Links to a website containing JJEncoded JavaScript, that starts the download of a malicious binary, were sent by
(see Singh, Meng Ong, Sa, Chong & Honjo 2015)
Of course, this techniques are well known for a long period of time and were widely used to deploy viruses, trojan horses and worms, which is why in chapter “Botnet Hiding”, there will be a list of techniques that are a little more complex. Nevertheless, this demonstrates nicely how quickly botnets adapt to novel approaches in malware detection, but have in 2014 on the other hand still been in a very early stage of evolution.
It has to be noted that there can also be other ways of getting a victim of botnets, like “drive-by downloading”, where internet users just have to visit a website that uses their browser’s or operating system’s vulnerabilies to infect them, for instance. (see Lemos 2009)
In earlier days, it was a well known principle, that visiting solely legal webpages, was enough to ensure yourself a decent layer of security while browsing. But “[…] staying away from the seedy places on the Internet is no longer an assurance of staying safe.” (Lemos 2009) as Giovanni Vigna (see Vigna n.d.), director of the Center for CyberSecurity at UCSB, mentions.
4.1.7 Downloading
After a computer is infiltrated, the code for making this machine a bot and connecting it to the botnet is retrieved from a download server. This usually works by using simple HTTP GET or HTTP POST requests. The code is then executed and the computer is from now on a part of the botnet.
4.1.8 Update module
Botnets use their update module to download code from dedicated Download Servers that are listed in their peer lists besides the C&C servers. Code they retrieve may be more recent peer lists, a newer version of their own code in general (which may also consist of code for its various sub modules or a new, more covert ways of contacting the C&C server etc.).
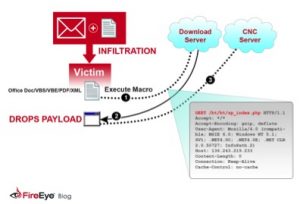 Figure 4.3: Concept of an infection
Figure 4.3: Concept of an infection
As explained in section “infection module” the bot is also capable of downloading exploits in order to adapt to the most recent vulnerabilities and their patches. Thus much like the signatures in a virus scanner, the bot can update his own code, achieving the exact opposite as a virus scanner.
4.1.9 Peer list
A peer list can be seen as the address book of a bot, where he can find the Command and Control servers, the proxies or other bots for the bot network. In early versions of botnets, these lists were static and did only contain the address number of the C&C server, then the concept evolved into using several C&C servers, then a Peer-to-Peer architecture came into place and now they use an interlayer with proxies to cover up the C&C servers. Most recent implementations even use subnets to conceal portions of the botnet from each other, in order to hide the overerall structure of the network.
4.1.10 Distribution module
The exploits used in the infection module, serve the main purpose of a botnet, which is to distribute its own code, much like a biologic virus does with human cells in order to make it serve its own purpose. Botnets sometimes also send out their own spam e-mails containing a link to malicious files or the files itself. This part depends on what kind of spam emails the botmaster wants to be sent out, which can usually be customized very easily in the botmaster’s administration panel.
5 Botnet detection
5.1 Difficulties in detecting P2P networks
“Early tools in the late 1990s were heavily centralized. A server (or handler) would coordinate the commands of the attacker and relay them to the individual DDoS agents.” (see Dittrich & Dietrich 2008, p.2) Apparently, the situation has changed dramatically as botnets are nowadays higly flexible, resilient and dynamic structures that are extremely hard to take down.
In contrast to monolithic systems that contain of one centralized server, it is not that easy to take down a bonet that consists of various P2P computers. The reason for this is, that there is no single target that can be attacked or decommisioned, but instead a bulk of other computers stepping into its place. As Shirley et. al. state correctly in their paper “NETWORKING 2008 Ad Hoc and Sensor Networks, Wireless Networks, Next Generation Internet”, “[i]t is very difficult to ascertain the characteristics of a P2P botnet because it is not possible to monitor a centralized location where all infected bots connect as such a location does not exist.”(Shirley & Mano 2008) Even if the structure “allows for some clustering, […] there still is no central authority other than the botmaster or botherder.” (see Dittrich & Dietrich 2008, p.4)
Based on this key insight, it is obvious that novel approaches have to be considered in order to cope with the threat of botnets.
5.2 Detection using network signatures
One way to find botnets in the clutter flowing through a network is, to look for certain network signatures. This means, for example to observe the normal IRC and HTTP Web traffic over a long period, to watch the IRC botnet traffic collected on a honeypot, as well as the IRC/Web botnet traffic collected on a testbed network. When now comparing them statistically, they show significant differences and can be clustered based upon this work, which is shown by Lu et. al. in their paper “Automatic Discovery of Botnet Communities on Large-Scale Communication Networks”. They also carry out a “payload signature based classification”(Lu, Tavallaee & Ghorbani 2009, p.3) in order to distinguish network traffic further. (see Lu, Tavallaee & Ghorbani 2009)
5.3 P2P Botnet Detection using Behavior Clustering & Statistical Tests
Su and Daniels choose a similar approach, that still differs much in detail. The following list shows their overall approach. *
- Capturing normal traffic using node behavior C&C traffic will be detected by additional behavior, that adds up to existing normal behavior clusters.
- Execute two anomaly detection schemes using statistical tests on popular behavior clusters
- Validate the assumptions using real traces from enterprise networks
- Evaluate the detection schemes in both simple and realistic (see Chang & Daniels 2009)
- (List has been reformulated for better readability)
5.4 Network traffic (data) mining approach
Because botnets have recently begun to use common protocols such as HTTP, it is nowadays even harder to distinguish their communication patterns. (see Venkatesh & Nadarajan 2012)
For that reason, artificial intelligence is used in order to detect botnets, or in particular their members talking to each other. Venkatesh et. al. for instance, achieve this by using a bold driver back propagation within a multi-layer feed forward neural network. This approach has the advantage of dynamically adapting the learning rate parameter while its weight updation process. (see Venkatesh & Nadarajan 2012)
The disadvantage of using data mining and network traffic analysis by means of machine learning in general, is that it needs a lot of data to be analyzed over a certain amount of time. Time, in which the botnet may go on infecting other computers and posing a threat by being able to perform commands like sending spam, running DDoS attacks, sniffing on passwords etc.
(see Masud, Gao, Khan, Han & Thuraisingham 2008)
5.5 Network behaviour characterisation using Semi-Markov models (HsMM)
Venkatesh et. al. also emanate from the problem that web-based C&C bots try to blend into normal HTTP traffic and it is therefore hard to identify HTTP botnets. On these grounds, they also use a machine learning approach, by utilizing hidden semi-Markov models (HsMM) to characterise the normal network behaviour. (see Venkatesh, Srihari, Veeramani, Karthikeyan & Anitha 2013)
As this is a 2013 approach, it would be intersting to see, how an approach like this would perform using more recent methods like RNNs (Recurrent Neural Networks) with LTSMs (Long Term Short Term Memory), because they usually tend to perform better than HMMs (Hidden Markov Models) for similar terms like sequential data. (see Klapper-Rybicka, Schraudolph & Schmidhuber 2001) (see Hochreiter & Schmidhuber 1997)
5.6 Network behaviour characteristics detection by comparison
When looking at the behaviour of a network, there are two main methods of discovering botnets:
- Find the distinction between P2P traffic and normal network traffic
- Find the distinction between P2P botnet traffic and legal P2P traffic (because they change the address of the C&C server they contact to retrieve commands)
So the detection of botnets through the analysis of their network traffic is in this case essentially a A-B comparisson.
In a series of experiments, Li et. al. found out, that botnet traffic can be characterized by a high connection failure rate, a high outbound network degree, irregular phased- similarity and irregularities. In their paper “Research on P2P Botnet Network Behaviors and Modeling”, they state that their model works, because it is based on the idea that Peer-to-Peer botnets show patterns that are inevitable. Acording to them, these features can then be used to create a more general form of a detection. (see Li, Hu & Yang 2012)
5.7 Honeynets
As shown in the taxonomy overview, there are also honeynets as a technique of discovering botnets. They are very similar to using honepot servers, which are mostly badly secured or unprotected computers, that should attract attackers deliberately. These would then try to infect a honeypot and a security system, like an IDS (Intrusion Detection System) would register this and raise an alarm. The machines intended for work, are kept safely behind a firewall, that works in collaboration with the honeynet.
The following picture shows an exemplary structure of a honeynet, here with two gateways, each for one of the two networks.
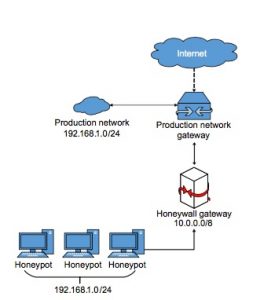 Figure 5.1: Example of a network including a honeynet
Figure 5.1: Example of a network including a honeynet
5.7.1 Detection technique taxonomy
Additionally to those main classes of signature based, anomaly based, there are also DNS based Intrusion Detection Systems. Due to the similarity between these approaches, the latter one will not be discussed in more detail, but in order to get an overview, the relations between these methods have been worked out by Karim et. al. quite nicely. (see Karim, Salleh, Shiraz, Shah, Awan & Anuar 2014)
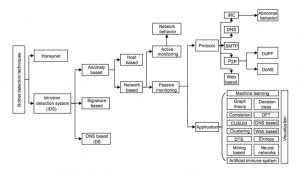 Figure 5.2: Taxonomy of botnet detection techniques
Figure 5.2: Taxonomy of botnet detection techniques
5.8 Active and passive detection
It is important to mention, that most of the detection mechanisms are of a passive nature, but as shown in the taxonomy tree, there are also active components that can track down botnets.
As Rahim and Muhaya point out in their paper “Discovering the Botnet Detection Techniques” (see Rahim & bin Muhaya 2010), there are techniques like “SLINGBot” that take a pro-active approach and claim to even be able to simulate future next generation botnets that way. (see Jackson, Lapsley, Jones, Zatko, Golubitsky & Strayer 2009, p.1) This is only one example of a more creative approach and it is needless to say that there are more.
That said, there are also three different approaches, that should be mentioned, but are not or not directly covered by the taxonomy shown above. These are needed for later detection mechanisms, like an IDS, but are not immediately used. They are rather required prerequisites for detection, which makes them nevertheless not less important to mention.
- Testbeds running real botnet software
- Databases that maintain traffic traces from operational data
- Reverse Engineering of captured botnet binaries
(see Jackson, Lapsley, Jones, Zatko, Golubitsky & Strayer 2009, p.1) (see Liu, Xiao, Ghaboosi, Deng & Zhang 2009)
5.9 Novel approaches
A new and very interesting approach is to start characterizing botnets from their e-mail spam records. This approach, which starts from the end, when an attack has already happend, tries to gather information by sent out spam emails, which contain IP addresses in their email headers etc.
The following steps show, how such a system works.
- Cluster email messages into spam
- Assess IP
- Merge spam campaigns into
(see Zhuang, Dunagan, Simon & Wang 2008)
5.10 Combined approaches
There are also more holistic solutions, like “ContraBot”, a collaborative botnet detection framework which combines approaches that can analyse network traffic to identify patterns of botnet activity with approaches that analyse software to detect items which are capable of behaving maliciously. (see Stevanovic, Revsbech, Pedersen, Sharp & Jensen 2012) So in difference to the other efforts, here not just one technique is used, but a combination of several solutions instead.
6 Botnet hiding
Strategies and Technology of hiding botnets are evolving continuously, because the interests of botmasters and law enforcement are contradictory. While the former wants to hide his network and especially its most valuable part – the Command and Control servers, the latter wants to discover it. As Liu et. al. state it in their paper “BotTracer: Execution-Based Bot-Like Malware Detection”, “Bot detection is still a challenging task since bot developers are continuously adopting advanced techniques to make bots more stealthy.” (see Liu, Chen, Yan & Zhang 2008)
6.1 Hiding the C&C server
As C&C servers work as a possible single point of failure when they get taken down by law enforcement agencies, it is of special interest to hide them. In his paper “BYOB – Build your own botnet”, François Bégin describes how a Command and Control server can be hidden in such a way that it will not be discovered easily. For this approach, he shows how fake “404 File not Found” HTTP status message responses can be utilized to mislead users into thinking the folder containg the botnet administration files would not exist. In his case, he hid the files connect.php, which takes care of holding connection to the bots, contacting the C&C server as well as an admin.php file that holds the code to administrate and manage the botnet. (see Bégin 2011, p.6)
6.2 Hiding in IRC traffic
After the first time period of botnets, where they were run by a more centralized and simple structure, there has been a significant change in the architecture the most botnets. Botmasters moved their bots to IRC (Internet Relay Chat) (see IRC.org – Home of IRC 2005) which had two notable advantages over the previous approach. First, the bots could vanish within the high volume of IRC chat traffic, and secondly, they were able to make use of its existing infrastructure, which served them with its advanced functionality such as channel encryption. (see Dittrich & Dietrich 2008, p.2)
6.3 Encryption
A technique we already know from various other fields, is to use encryption in order to conceal the subject matter of communication. Nevertheless, it is kind of remarkable, that encryption, which is usually thought to serve the users in protecting their their data, now helps criminals to smuggle out the same users’ contents from their own computers. Botnets normally use the same protocols as normal / legal software does. This means they take advantage of techniques like SSL / TLS, certificates and also of TOR (The Onion Router) network, which serves its users with encrypted, tap-proof access to the internet and is especially important for dissidents that need to hide from a regime. It is a well known problem that criminals also utilize TOR’s service in order to hide their own communication. According to Hopper et. al. it poses a great challenge to protect Tor hidden services from botnet abuse. (see Hopper 2014)
Luchian Kang’s paper “Efficient botnet herding within the Tor network” goes a little bit more into detail on that topic and stresses the point of using the Tor network to acquire machines in order to build a herding layer between C&C servers and underling bots. (see Kang 2014).
6.4 Tunneling
In order to counteract crypto services being misused by internet criminals, IDS (Intrusion Detection Systems) like Snort (see Snort – Network Intrusion Detection & Prevention System n.d.) force open encrypted channels like HTTPS. This means that encrypted communication is only possible if the subject matter of it, is known to the IDS. After checking the communication’s content, it then usually encryptes the data again, in a way that secure connections to the outside world are ensured (Transparent proxy) (see Gibb 2015).
As nicely as this concept works in normal cases, it fails to detect messages that are sent out through covert channels. This means for instance, when using a protocol necessary for normal system-operating, like DNS (Domain Name Service) (see Beal n.d.) that is used to resolve domain names into IP addresses, attackers encapsulate their content into DNS packages. This content is obviously not about resolving domain names, but instead used for executing malicous tasks like sending out the users passwords, records of a keylogger etc.
The tunneling process that is shown here by the example of the DNS protocol, can also be carried out using other procotols.
6.5 Steganography
Security companies alike blackhat hackers also react to the challenges, novel techniques pose to the internet. This means, that they also use methods like deep packet inspection to look into the contents of a data stream in order to find out, if ill-natured communication flows appear threrein.
As a way of dealing with this, criminals tend to more sophisticated methods like steganography, which means – in an IT sense of the word – to replace “[…] unneeded bits in image and sound files with secret data. Instead of protecting data the way encryption does, steganography hides the very existence of the data. And it’s undetectable under traditional traffic-pattern analysis”. (see Radcliff 2002) In an even more sophisticated approach, it is also possible to hide information in unused data of VOIP (Voice over IP) calls (see Greene 2009) to show just one of the possibilities using audio files.
As Tim Greene puts it, it is tough to fight steganography, because “[…] traditional security devices such as firewalls and application firewalls don’t detect this type of illicit transfer; a file containing a secret message looks just like a legitimate file.” (see Greene 2009)
To show how steganography works in a very practical manner, the following example demonstrates how a internet criminals could utilize harmless pictures to sending out sensitive data.
As shown in the first of the two figures, there is a number for each of the three colours RGB (Red, green and blue) that lies between 0 and 255. This number determines, what portion of the resulting mix, this single color (for instance red) accounts for. A higher number means, more of the colour gets mixed in.
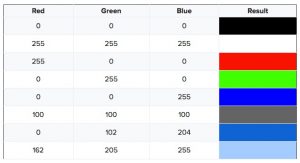 Figure 6.1: Example of different values showing different colours
Figure 6.1: Example of different values showing different colours
Looking at the upper colour table, it seems like there can only exist one colour combination, which results in a unique shade of blue.
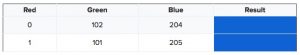 Figure 6.2: Example of different values showing “visibly” the same colours
Figure 6.2: Example of different values showing “visibly” the same colours
The bottom table in contrast shows, that two different colour mixes indeed can result in two optical indiscernible colours. Of course, the colours only appear that similar to the human eye. To computers they are distinguishable, which is however not important in most cases, when the original picture is not known to the machine.
Reconstructing the hidden information is namely only possible, by comparing the original image to the manipulated image or a special pattern mask. (see Al-Turfi 2009) It is therefore very hard for computers to automatically detect manipulated pictures if they don’t know the original ones of and impossible to the human eye.
Nevertheless, there still exist ways to detect the manipulation of images e.g. by looking for unnatural distribution of colour values over the whole picture or similar methods.
6.6 Constant changes of signature
6.6.1 HTTP signature
In order not to be discovered by signature detection algorithms, bots contacting the C&C server, try to change the signature they show when making a HTTP GET or HTTP POST query in order to retrieve commands from their botmaster.
Botnets are known for constantly and quickly changing their signature as the example of Agobot shows. Sophos, the vendor of Antivirus enlisted more than 1500 different Agobot versions some years ago, and the number was steadily increasing. (see Provos & Holz 2008, p.362 )
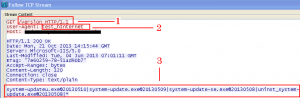 Figure 6.3: First HTTP request to C&C server: test-internet used as a User-Agent
Figure 6.3: First HTTP request to C&C server: test-internet used as a User-Agent
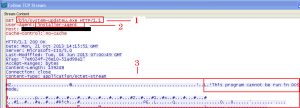 Figure 6.4: Second HTTP request to C&C server: installer-agent used as a User-Agent
Figure 6.4: Second HTTP request to C&C server: installer-agent used as a User-Agent
6.6.2 Bot signature
The same method that was used to change the signature of HTTP requests and not be detected by IDS and antivirus software, is also used with the malware itself. By constantly changing its program code, the signature it generates looks very different as Mathew J. Schwartz mentions, “[i]nterestingly, PPI providers repack–as in, recompile– their downloaders on average every 11 days, although one service did it twice per day. Repacking generates a new piece of software, which helps the downloader software evade signature-based security defenses, at least until the security vendor spots the new malware and creates a new MD5 hash signature for its detection engine. “ (see Schwartz n.d.)
6.7 Covert communication in private subnets
Another way for botnets to hide is to use special techniques in order to ensure covert communication in a private subnet. This is shown very nicely by Shirley and Mano in their paper “A Model for Covert Botnet Communication in a Private Subnet”. In their case they claim that most IDS cannot see their hidden bots, because they do not communicate directly with the outerworld. (see Shirley & Mano 2008)
Nevertheless, they say it “enables a group of systems within a switched subnet to participate in a global botnet infrastructure without generating communication patterns that would allow an external monitoring system to identify the compromised hosts.” (Shirley & Mano 2008, p.631) Luckily they plan on implementing countermeasures for this very case in the future, to make the IDS BotHunter cope with those sort of problems.
6.7.1 Covering up payload downloads
The technique of simply downloading files containing the bot’s payload gets obviously less promising as networks get secured better over the decades. Antivirus software, firewalls and encryption are widely known by most users, even if most people don’t understand their operation principle. Anyhow, this is an obstacle malware developers have to consider more and more. (see Singh, Meng Ong, Sa, Chong & Honjo 2015)
In order to achieve this, there have been several new approaches been implemented and used in botnet Dridex in 2014/2015.
For instance, instead of directly downloading the payload as an executable file, it gets requested as a Base64 encoded text file. This file then decodes to a VBScript and Batch container. (see Singh, Meng Ong, Sa, Chong & Honjo 2015)
The following figures show the process in practice. Figure 6.5 shows how the HTTP downloaded code looks in base64 *.
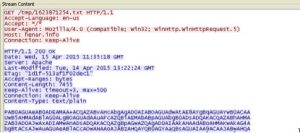 Figure 6.5: Base64 download via HTTP
Figure 6.5: Base64 download via HTTP
In figure 6.6, it is demonstrated how another HTTP GET request gets sent out, which downloads an executable file.
Figure 6.6: HTTP GET request
*(Base 64 is a transport encoding, that ensures that the text transferred, doesn’t cause problems while sending it and can be reconstructed after receiving it. (see Base64 Decode and Encode – Online n.d.)).
Figure 6.7 shows how the downloaded base64 code gets executed and constructs Visual Basic and batch code out of itself, using markers.
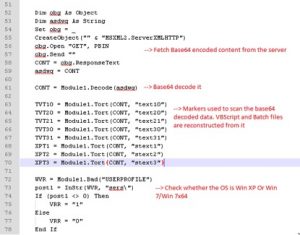 Figure 6.7: Visual Basic source code
Figure 6.7: Visual Basic source code
Once these Visual Basic and batch files are created, the downloaded code from step 2 gets executed.
This multistage approach makes it way harder for security software to inspect the downloads and files and to guess their actual purpose. The fact that attackers use trustworthy and everyday sources as dropbox.com and pastebin.com, makes the attack even more covert. (see Singh, Meng Ong, Sa, Chong & Honjo 2015)
6.8 Fake file formats
A well known trick from spammers is to send file formats as an attachment in emails which seem to be harmless and benign, but are dangerous and powerful executables instead. So instead of, for instance, opening an audio file as the user might have thought, he opens a file called “soundfile.wav.exe”, where the “.exe” extension is hidden in the e-mail client application.
On a little bit more advanced way, botnet operators are still using the same technique in a 2015 version of botnet Dridex, when they offer Visual Basic Script and Microsoft Word files as attachments. (see Singh, Meng Ong, Sa, Chong & Honjo 2015)
The fact that this very basic approach of users opening files with fake extensions, is still working is quite astounding, because even some of the older, but still very famous viruses have spread by using this method over a decade ago, as the example of “I love you” virus shows. (see Kleinbard & Richtmyer 2000)
7 Botnets: Highly resilient secure systems
The peer-to-peer architecture implemented by botnet Hlux has the advantage of being very robust against takedown attempts. ”Just like its brothers, Kelihos.B relies on a self-organizing, dynamic peer-to-peer topology to make its infrastructure more resilient against takedown attempts” (Tillmann 2012), as Tilman, security expert with Crowd-Strike explains.
The dynamic structure allows for fast reactions if irregularities are observed. When a bot wants to request jobs, it never connects directly to a controller, no matter if it is running in worker or router mode. A job request is always sent through another router node. So, even if all controller nodes go off-line, the peer-to-peer layer remains alive and provides a means to announce and propagate a new set of controllers. (see Tillmann 2012)
7.1 Simple approach: Using domains
The simplest of approaches is to use domain names in order not to be taken down too easily. Most botnets nowadays use this approach to contact their C&C servers. This serves the purpose not to rely on one IP address that could be changed easily by criminal prosecutors. Therefore a domain name that can point to several IP addresses is used to serve as a dynamic indirection. (see Bégin 2011, p.6)
Botmasters usually also choose ISPs (Internet Service Providers), registrars and DNS/- DynDNS (Domain Name Service) providers for hosting their botnet’s C&C servers, who are known for not being very cooperative in the case of law enforcement requests. Sometimes, this can be even more extreme, when providers, like “3FN Service”, who also hosted “Spam-Spewing Botnets, Phishing Web sites, Child Pornography, and Other Illegal, Malicious Web Content” (FTC Shuts Down Notorious Rogue Internet Service Provider, 3FN Service Specializes in Hosting Spam-Spewing Botnets, Phishing Web sites, Child Pornography, and Other Illegal, Malicious Web Content | Federal Trade Commission 2009). Luckily 3FN has been taken down by the FTC (Federal Trade Commision). (see Bégin 2011, p.12) So this puts a layer between the ‘virtual’ world of the internet and the ‘real’ world of persons running botnets whose connection is not easy to resolve.
7.2 Domain Flux
Based on using domains as a method of resilience, botnets often also use a technique called Domain Flux, that has an inbuilt domain generation algorithm which is used to switch to different domain names depending on a given timeframe. For instance can the bots in a net try to query their commands from www.Alice.com in week one and switch to www.Bob.com in week two, while the Command and Control server also nows the domain they are choosing at a certain time. (see Bégin 2011, p.12)
Botnets of course are usually using subdomains, which can be obtained automatically and most importantly, for free.
7.3 Dynamic C&C contact publishing algorithm
One of the most recent evolutions in the field of botnets is to move and switch the Command and Control servers even more dynamically, and to use public plattforms for this. One of the examples of them is to use the well known website Reddit.com, in order to return a list of IPs for C&C servers, camouflaged as a Minecraft server list. (see 17,000 Macs infected with botnet controlled via Reddit n.d.)
7.3.1 Integrating current search ranks of public web portals
Bots find these lists, by using public services’ search engines. In the last-mentioned case, “the first 8 bytes of the MD5 hash of the current date” have been used in order to give the current server list a name and, of course, to make the bots able to find the servers. (see 17,000 Macs infected with botnet controlled via Reddit n.d.)
7.4 Dynamic peer list
In the early days of botnets, structures have been very simple compared to the current ones. Botnets were strongly centralized structures with a sole Command and Control server, which made it clear who was in charge. (see Vania, Meniya & Jethva 2013, p.25) The bots only had to contact a certain IP address to retrieve their commands. However, with more flexible designs, bots have to hold a list of peers containing all the C&C computers that are also changing IP addresses and varying in number. With the emerging of P2P techniques, this peer list had also to have to hold the IP addresses of the bots around it. In the most recent step of botnet evolution, they also have to distinguish between normal harvesting bots and proxies.
However, despite the challenge, this system makes them highly resistent to changing situations. Even when many bots are disconnected, the system can still run as nothing would have happened. Dynamic peer lists make bots so resistent, to make them even cope with network partitions on a large scale. When a botnet gets separated and cut into two or three pieces, the groups can still operate on their own.
It has been quite understandable that botnets using P2P technologies are also utilizing techniques implemented in commercial or file sharing software. One of them is DHT (Dynamic Hash Tables) as Holz et. al. show by the example of Storm Worm. (Holz, Steiner, Dahl, Biersack & Freiling 2008, p.3)
Systems with flexible pose a great threat to internet security, as researchers had to realize, when they tried to take down a botnet called “Grum”. Arif Mushtaq with Fire-Eye stated that “after seeing that the Panamanian server had been shut down, the bot herders moved quickly and started pointing the rest of the CnCs to new secondary servers in Ukraine.” (see Huge spam botnet Grum is taken out by security researchers – BBC News 2012)
7.5 Patching mechanism
Using its patching mechanism, a bot can download exploits later, which makes it a very flexible piece of software. Even if a vulnerability is patched by the system operator of the infected computer, it is still possible for the bot to use another weakness of the operating system or software that is installed on it.
Even if there are all patches installed on the machine and it is as safe as possible, there are almost always so called Zero-day exploits* available. These vulnerabilities, can easily be bought on the black market and can sometimes cost 90.000$ a piece (Khandelwal n.d.) as a Microsoft related case shows. So the hacker can buy a new exploit, patch it into his next version of the botnet and simply roll it out. When the bots check their C&C servers the next time, they will then download and install the code.
7.6 Strong resilience: Proxy layer
The so called proxy layer, which was already explained roughly in chapter “Functional principle”, plays an important role in keeping the botmasters safe. It works like a wall they can hide behind, because no bot contacts the C&C server directly, but uses a middlesman instead. As Tillmann with CrowdStrike inc. puts it, “[w]hen a bot wants to request jobs, it never connects directly to a controller, no matter if it is running in worker or router mode. A job request is always sent through another router node. So, even if all controller nodes go off-line, the peer-to-peer layer remains alive and provides a means to announce and propagate a new set of controllers.” (see Tillmann 2012)
So by creating such a flexible and responsible system, botnets keep an extremely high availability. There is simply no direct way to contact the botmaster and no simple way to out the network, because it is highly self-organizing. This indeed, takes P2P technologies to a whole new level, as the involved machines only have been serving a single purpose (bot, proxy or C&C server) in the past.
*(“A Zero Day is both an unpatched software hole previously unknown to the software vendor and the code attackers use to take advantage of said hole.” (Zetter 2014) )
7.7 Dramatic change in structure: Real P2P
As mentioned before, P2P network structures where the bots can change their profession and are able to transform into proxies and vice versa, are a big problem for law enforcement.
The situation that was not playing in favor of security experts but criminals, got still worse. In most recent version of botnets emerging in the wild, bots can tranfsorm themselves even more extremely. Instead of being restricted to be bot and proxy, they can now also work as a Command and Control server.
A variant of the Zeus botnet that was isolated by Symantec, didn’t use any C&C, but every peer in the botnet could act as a C&C server instead, while none of them really were one, as the researchers mentioned. ”Bots are now capable of downloading commands, configuration files, and executable from other bots – every compromised computer is capable of providing data to the other bots[…]”. (see Botnets and cybercrime – Introduction – InfoSec Resources n.d.)
This step clearly marks a new era of botnets (Bu, Bueno, Kashyap & Wosotowsky 2010, p.1) which makes the former “P2P” botnets look comparatively harmless, as this kind of malware will be far more difficult to take down.
8 Taking down botnets
But besides this evolution of botnets, there are also successes in the fight against botnets. Concrete examples of taken down botnets will be demonstrated in this chapter under section “Success Stories”. Besides to those positive examples, there are also set-backs which will be a matter of discussion.
8.0.1 Decommissioning P2P botnets by sinkholing
As discussed before, botnets can have different Comand and Control servers, which is generally the case nowadays. Therefore it is not as simple as in a monolithic system with only one C&C server, to take down the machines that are distributing commands to the botnet.
One way to decommission infected computers from a botnet is to sinkhole them. For this maneuver, the peer lists of the affected machines have to be altered. In the early days of botnets and other malicous software, peer lists have been static and were pointing to a list of known C&C servers where the bots could query their commands from. However, this is not the case nowadays, because criminals have quickly reacted to law enforcement agents taking down whole networks by just changing the peer lists of the machines. For that reason, botmasters are now controlling bots that contain dynamic peer lists. As mentioned in the chapter prior to this, dynamic peer lists can point to other bots, to various Command and Control servers or to a layer inbetween the bots and the C&C servers (This intermediate layer is shown in figure 8.1).
Figure 8.1: Structure of botnet with proxy layer by the example of gamover botnet
With the sinkholing technique, the dynamic peer lists get changed in a way that they are now pointing to useless sinkholes to the contrary of pointing to other machines that are able to serve them with the instructions from the botmaster, like they did before. In that way, bots are now disrupted from the botnet.
In their paper “Sok: P2pwned-modeling and evaluating the resilience of peer-to-peer botnets” Rossow et. al. point out, that there are three general steps that have to be taken in order to take down a botnet or at least a portion of it:
- Sinkhole announcement: In this step, as many peers as possible get the artificially created sinkhole as a fake Command and Control server.
- Node isolation: All connections that don’t point to the fake C&C server(s) should be interrupted and deleted from the bots source code in order to isolate the bot from the malicious network. As a result they are not able to communicate with each other any more and can’t retrieve commands from C&C servers.
- Fallback prevention: It is well known to botmasters or botnet designers / programmers, that law enforcement agencies have huge interest in taking down b Therefore botnets tend to increasingly have fallback mechanisms implemented that come into place in certain kinds of situations. For instance it may be the case that a bot does not receive commands for a certain amount of time. In this situation, a bot may change the address of the Command and Control servers in its peer list and switch to another one.
In general, there are two well known strategies to circumvent this problem.
- Disabling the backup channel
- Preventing the bots to enter into fallback mode (where they would g. change the address of the C&C server they contact to retrieve commands)
(see Rossow, Andriesse, Werner, Stone-Gross, Plohmann, Dietrich & Bos 2013)
8.1 Success Stories
In 2009, there was also a massive shutdown of Mariposa botnets, executed by law enforcement and Panda Security. (see Security 2010) The malware had gained control over “12.7 million compromised personal, corporate, government and university IP addresses in more than 190 countries.” (Security 2010)
A huge success carried out by Microsoft, was also the decommissioning of ZeuS and SpyEye botnets, which were powerful banking trojans that have “helped thieves steal more than $100 million from small to mid-sized businesses in the United States and abroad.” (see Krebs 2012)
The Rustock botnet, was another system disrupted from the net by Microsoft in 2011. (see Blogs 2011)
In 2012, Kaspersky Lab had also disabled the second version of Hlux/Kelihos Botnet (see Werner 2011), which is “a peer-to-peer botnet with an architecture similar to the one used for the Waledac botnet.” (Tillmann 2012) as Tillmann with CrowdStrike mentions. Fortunately, Kaspersky even explaines how they actually managed to take the botnet down. (see How Kaspersky Lab and CrowdStrike Dismantled the Second Hlux/Kelihos Botnet: Success Story 2012)
Microsoft furthermore took down “almost 90 percent of Citadel botnets in the world” (Constantin 2013)see in June 2013, which was a huge success. (see Constantin 2013)
In 2015, “Trend Micro, INTERPOL, Microsoft, Kaspersky Lab, and the Cyber Defense Institute” (SIMDA: A Botnet Takedown 2015) furthermore disrupted the Simda botnet, which was another great success.
8.1.1 A botnet delivering anti virus software
One of the most recent examples is a Dridex takedown in 2016, while it is still a matter of discussion who actually took down the famous botnet. This case was especially remarkable, because they managed to destroy the system from within. After getting access to the C&C servers, they managed to roll out a version of Avira’s anti virus software that was then delievered to all the bots in the network instead of harvesting bots retrieving another patch of malicious exploit code. (see Frink 2016)
It is worth noting, that this list of examples, although showing some of the remarkable results of botnet takedowns, does not claim to be complete.
8.2 Set-backs
It is quite noteworthy that it often happens, that a botnet is thought to be stopped, but recovers very quickly, as the case of Dridex shows examplarily. The botnet was brought to a halt in August 2015, but this was retrospectively just a temporary pause, because Dridex is still operating, as a wave of attacks from September 2015 showed. Sabrina Berkenkopf therefore calls Dridex even the “Comeback King”. (see Berkenkopf 2016)
And there have been plenty of examples, that this happens far more often than desired. Worth mentioning is also that in Webroot’s Threat Blog, Andrew Brandt desribes “Botnet Takedown Mistakes to Avoid” (Brandt 2011), which may be interesting to read in order to learn from past mistakes and avoid them in the future.
8.2.1 Countermeasures
Despite all the set-backs in this field, there are also countermeassures that can be taken in order to stop botnets from spreading.
Above all, the best protection obviously is to prevent systems from getting infected at all. (see Young & Barth 2014) Compared to stopping a highly resillient structure like a botnet to up front security meassures are, the latter are far easier to fulfill and also way more time and cost efficient.
Most importantly, users have to be kept well informed about current infection vectors and sometimes even be pushed into the direction of a more safe behaviour. Antivirus software as well as a firewall and IDS should be the standard for everybody wanting to use the internet. In reality, dealing with “End users are IT’s biggest security challenge” (Harding 2015), as experience shows.
Worth mentioning is also that Liu et. al. describe several steps that can be taken in order to tackle botnet threats, in their paper “Botnet: Classification, Attacks, Detection, Tracing, and Preventive Measures”. (see Liu, Xiao, Ghaboosi, Deng & Zhang 2009)
Adding up to this, users should also check if they are part of a botnet. Kaspersky, Sonicwall and others provide such services. Looking at the whole structure of the internet, it should be discussed if a service like that shouldn’t be implemented as a standard protocol or service, so that users can keep themselfes informed if they are part of a botnet.
Some of the services available are:
- https://checkaspersky.com/
- http://botnet.sonicwall.com/view
- https://campaigns.f-secure.com/router-checker/de_DE/
- https://www.botfde/botnetcheck/
The downside of this method is, that botnets could prevent users from reaching this site, or more elegantly, send users a fake website, stating that everything is alright. To prevent this, the websites can actually be accessed from another computer. Knowing the IP address of the machine a user wants to check, he can simply insert the IP and test it using another PC.
On the long run, and regarding the global threat botnets pose to the internet, it would be of great interest to implement a standardized protocol informing the users when they got part of a botnet. Otherwise there is no feedback channel at all, where infected machines could be reached.
As mentioned in the foregoing chapters, botnets are extremely powerful and resilient structures, but nevertheless there are ways to combat them. One of the existing examples is mentioned in the presentation (as well as the book chapter) “How to Steal a Botnet and What Can Happen When You Do” by the example of the Torpig botnet. (see Kemmerer 2009)
In “Beheading Hydras: Performing Effective Botnet Takedowns”, it is also shown what can be learned from previous efforts by performing a “postmortem analysis of the recent Kelihos, Zeus and 3322.org takedowns” (Nadji, Antonakakis, Perdisci, Dagon & Lee 2013, p.1) *. They also give the recommendation, that most botnets can be disrupted by using a “DNS-based takedown strategy only” (Nadji, Antonakakis, Perdisci, Dagon & Lee 2013, p.1).
8.3 Sybil attack
In “Measurements and Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm”, Holz et. al. show how the takedown of a botnet using Sybil attacks can be carried out. As they put it, it is the main idea of a Sybil attack “[…] to introduce malicious peers, the sybils, which are all controlled by one entity.” (Holz, Steiner, Dahl, Biersack & Freiling 2008, p.5) in order to overtake the whole network. (see Holz, Steiner, Dahl, Biersack & Freiling 2008)
Stankovic and Simic compare different defense strategies against botnets on a practical everyday level in their paper “Defense Strategies Against Modern Botnets”. (see Stankovic & Simic 2009)
These examples show that fighting botnets is not just a tilting against windmills. It is nevertheless to the present day still a problem that botnets are very robust against attempts to take them down.
(“Postmortem Analysis” in (Nadji, Antonakakis, Perdisci, Dagon & Lee 2013, p.7)
9 Conclusion
9.1 Ancient infection vectors
The mere fact, that Dridex as well as Locky still use such an old fashioned infection vector like fake mail attachments, makes many security-interested computer scientist consecutively ask themselves, why it still is so easy for home users to open an email containing a .vbs and a .bat file? As long as a person is not a computer expert, there should be no good reason for downloading and opening such a combination of files. Preventing users from opening file combinations like these would by all means be much more cost efficient and target-aimed, than trying to take down botnets, which is obviously a very complex task.
9.2 Novel threats
As bad as the latest development towards the direction of “real” P2P botnets may seem, it could also be a chance for law enforcement, security firms and researchers.
Machines in a P2P network are usually not secured as good as dedicated C&C servers in an overseas location and behind bulletproof hosting services. So it has to be noted that the most recent progress in the field of botnets can also offer an opportunity.
The progress from Peer-to-Peer toward a “real” P2P approach, was not done without any reason, as it can be assumed. Changes on the internet criminal’s side usually proceed from the fear of getting caught. Hence the efforts of taking down botnets as well as the pressure from international law enforcement could turn out to make a change in the end.
List of figures
0.1 Cover image
https://de.fotolia.com/id/67526425 (Standard license)
1.1 ENISA: Emerging threats
2.1 Control panel of a botnet Qbot
http://sensorstechforum.com/wp-content/uploads/2014/10/Qbot-Botnet.jpg
3.1 Example for a centralized botnet
3.2 Evolution from centralized to Peer-to-Peer botnet
3.3 Layered P2P C&C servers on top (dark red), proxy bots inbetween (red) and harvester bots on the bottom (green)
https://cdn.securelist.com/files/2011/09/208193138.png
3.4 Layered P2P Commands go top down from botmaster, through C&C servers and Proxy (P2P layer) to the Worker Nodes (bots).
4.1 Administration Panel
http://sensorstechforum.com/wp-content/uploads/2014/10/Qbot-Botnet.jpg
4.2 Topology of P2P Zeus
http://www.syssec-project.eu/m/page-media/3/zeus_malware13.pdf
4.3 Concept of an infection
5.1 Example of a network including a honeynet
http://link.springer.com/article/10.1631/jzus.C1300242
5.2 Taxonomy of botnet detection techniques
http://link.springer.com/article/10.1631/jzus.C1300242
5.3 Example of different values showing different colours
https://sdgblue.com/basic-steganography-explained/
6.1 Example of different values showing “visibly” the same colours
https://sdgblue.com/basic-steganography-explained/
6.2 First HTTP request to C&C server: test-internet used as a User-Agent
6.3 Second HTTP request to C&C server: installer-agent used as a User-Agent34
6.4 Base64 download via HTTP
https://www.fireeye.com/content/dam/fireeye-www/blog/images/Dridex/fig1.jpg
6.5 HTTP GET request
https://www.fireeye.com/content/dam/fireeye-www/blog/images/Dridex/fig2.jpg
6.6 Visual Basic source code
https://www.fireeye.com/content/dam/fireeye-www/blog/images/Dridex/fig3.jpg
8.1 Structure of botnet with proxy layer by the example of gamover botnet
http://krebsonsecurity.com/wp-content/uploads/2014/06/gameovergraph.png / Original Source: FBI
Bibliography
- 17,000 Macs infected with botnet controlled via Reddit (n.d.).
URL: https:://www.rt.com/news/193032-mac-infected-hackers-reddit/
- Adamov, Alexander (2013), ‘A Modification of Kelihos Looks for Passwords Stored in Internet Browsers | Lavasoft’.
URL: http://www.lavasoft.com/mylavasoft/malware-descriptions/blog/a-modification-of-kelihos-looks-for-passwords-stored-in-internet-browsers
- Al-Turfi, Mohammed Nasser (2009), ‘Difference Realization in Image Steganography’, Contemporary Engineering Sciences 4(7), 341–352.
URL: http://www.m-hikari.com/ces/ces2011/ces5-8-2011/alturfiCES5-8- 2011.pdf
- Andriesse, Dennis, Christian Rossow, Brett Stone-gross, Daniel Plohmann & Herbert Bos (n.d.), Highly resilient peer-to-peer botnets are here: An analysis of gameover zeus, in ‘in Malicious and Unwanted Software:” The Americas”(MALWARE), 2013 8th International Conference on. IEEE, 2013’, pp. 116–123.
- Barnett, Ryan (2010), ‘Tactical Web Application Security: Botnet Herders Targeting Web Servers’.
URL: http://tacticalwebappsec.blogspot.com/2010/05/botnet-herders-targeting-web-servers.html
- Base64 Decode and Encode – Online (n.d.).
URL: https://www.base64decode.org/
- Basic steganography explained (2011-03-02T13:17:32+00:00).
URL: https://sdgblue.com/basic-steganography-explained/
- Beal, Vangie (n.d.), ‘What is Domain Name System (DNS)? Webopedia Definition’.
URL: http://www.webopedia.com/TERM/D/DNS.html
- Bégin, François (2011), BYOB: Build Your Own Botnet, SANS Institute InfoSec Reading Room.
URL: https://www.sans.org/reading-room/whitepapers/covert/byob-build-botnet-33729
- Berkenkopf, Sabrina (2016), ‘DRIDEX – THE COMEBACK KING’.
URL: https://blog.gdatasoftware.com/2015/12/24315-dridex-the-comeback-king
- Bisson, David (2014), ‘Introducing Xsser mRat: The First Advanced Chinese iOS Trojan’.
URL: http://www.tripwire.com/state-of-security/latest-security-news/introducing-xsser-mrat-the-first-advanced-chinese-ios-trojan/
- Bitcoin simplified. (n.d.).
URL: http://bitcoinsimplified.org/
- Bitcoin-stealing virus infects thousands of PCs (2014).
URL: http://www.cnbc.com/2014/02/24/pony-botnet-steals-bitcoins- digital-currencies–trustwave.html
- Blogs, Microsoft Corporate (2011), ‘Taking Down Botnets: Microsoft and the Rustock Botnet’.
URL: http://blogs.microsoft.com/on-the-issues/2011/03/17/taking-down-botnets-microsoft-and-the-rustock-botnet/
- Botnets and cybercrime – Introduction – InfoSec Resources (n.d.).
URL: http://resources.infosecinstitute.com/botnets-and-cybercrime- introduction/
- Brandt, Andrew (2011), ‘Black Hat Redux: Botnet Takedown Mistakes to Avoid’.
URL: http://dl.acm.org/citation.cfm?doid=2508859.2516749
- Bu, Zheng, Pedro Bueno, Rahul Kashyap & Adam Wosotowsky (2010), ‘The new era of botnets’, White paper from McAfee .
URL: http://www.partner.securecomputing.com/au/resources/white-papers/wp-new-era-of-botnets.pdf
- Chang, Su & Thomas E. Daniels (2009), P2P botnet detection using behavior clustering & statistical tests, in ‘Proceedings of the 2nd ACM Workshop on Security and Artificial Intelligence’, ACM, pp. 23–30.
URL: http://dl.acm.org/citation.cfm?id=1654996
- Chulov, Martin & Helen Pidd (2011), ‘Defector admits to WMD lies that triggered Iraq war’, The Guardian .
URL: https://www.theguardian.com/world/2011/feb/15/defector-admits-wmd-lies-iraq-war
- Cimpanu, Catalin (2016a), ‘Authorities Shut Down Botnet of 4,000 Linux Servers Used to Send Spam’.
URL: http://news.softpedia.com/news/authorities-shut-down-botnet-of-4-000-linux-servers-used-to-send-spam-502690.shtml
- Cimpanu, Catalin (2016b), ‘There Is a Connection Between the Lurk Arrests, Angler, and the Necurs Botnet’.
URL: http://news.softpedia.com/news/there-is-a-connection-between-the-lurk-arrests-angler-and-the-necurs-botnet-506164.shtml
- Cluley, Graham (2014a), ‘17,000 Macs hit by malware botnet, with help from Reddit’.
URL: https://www.grahamcluley.com/2014/10/mac-malware-botnet-reddit/
- Cluley, Graham (2014b), ‘Feedly refuses to give in to blackmail, gets hit by DDoS attack’.
URL: https://www.grahamcluley.com/2014/06/feedly-blackmail-ddos/
- Constantin, Lucian (2013), ‘Microsoft: Almost 90 percent of Citadel botnets in the world disrupted in June’.
URL: http://www.pcworld.com/article/2045282/microsoft-almost-90-percent-of-citadel-botnets-in-the-world-disrupted-in-june.html
- Dittrich, David & Sven Dietrich (2008), ‘Discovery techniques for P2P botnets’, Stevens Institute of Technology CS Technical Report 2008 4, 1–14.
URL: https://staff.washington.edu/dittrich/papers/dd2008tr4/ dd2008tr4-20091024.pdf
- Editor, Zeljka Zorz-Managing (2011), ‘Rustock botnet downed by Microsoft’.
URL: https://www.helpnetsecurity.com/2011/03/18/rustock-botnet- downed-by-microsoft/
- ENISA Threat Landscape 2015 — ENISA (2016).
URL: https://www.enisa.europa.eu/publications/etl2015
- Florian, Rötzer (2007), ‘Estland beschuldigt Russland des Cyberterrorismus’.
URL: http://www.heise.de/newsticker/meldung/Estland-beschuldigt- Russland-des-Cyberterrorismus-179288.html
- Frink, Lyle (2016), ‘Dridex botnet distributor now serves Avira’.
URL: https://blog.avira.com/dridex_serves_avira/
- FTC Shuts Down Notorious Rogue Internet Service Provider, 3FN Service Specializes in Hosting Spam-Spewing Botnets, Phishing Web sites, Child Pornography, and Other Illegal, Malicious Web Content | Federal Trade Commission (2009).
URL: https://www.ftc.gov/news-events/press-releases/2009/06/ftc-shuts-down-notorious-rogue-internet-service-provider-3fn
- Gibb, Robert (2015), ‘What is a Transparent Proxy?’.
URL: https://www.maxcdn.com/one/visual-glossary/transparent-proxy/?
- Global Botnet Threat Map – Botnet Network Security Activity – Trend Micro USA (n.d.).
URL: http://www.trendmicro.com/us/security-intelligence/current- threat-activity/global-botnet-map/index.html
- Goodin, Dan (2016), ‘Large botnet of CCTV devices knock the snot out of jewelry website’.
URL: http://arstechnica.com/security/2016/06/large-botnet-of-cctv-devices-knock-the-snot-out-of-jewelry-website/
- Gray, Richard (2013), ‘Most common and hackable passwords on the internet’.
URL: http://www.telegraph.co.uk/technology/internet-security/10303159/Most-common-and-hackable-passwords-on-the-internet.html
- Greene, Tim (2009), ‘Steganography meets VoIP in hacker world’.
URL: http://www.computerworld.com/article/2527381/security0/steganography-meets-voip-in-hacker-world.html
- Greenemeier, Larry (n.d.), ‘Seeking Address: Why Cyber Attacks Are So Difficult to Trace Back to Hackers’.
URL: http://www.scientificamerican.com/article/tracking-cyber- hackers/
- Greenspan, Jesse (n.d.), ‘The Gulf of Tonkin Incident, 50 Years Ago – History in the Headlines’.
URL: http://www.history.com/news/the-gulf-of-tonkin-incident-50-years-ago
- Harbison, Cammy (2016), ‘New ‘Locky’ Ransomware Virus Spreading At Alarming Rate: Can The Malware Be Removed And Files Decrypted?’.
URL: http://www.idigitaltimes.com/new-locky-ransomware-virus-spreading-alarming-rate-can-malware-be-removed-and-files-512956
- Harding, Sharon (2015), ‘Spiceworks: End users are IT’s biggest security challenge’.
URL: http://www.channelnomics.com/channelnomics-us/news/2439236/ spiceworks-end-users-are-its-biggest-security-challenge
- Hochreiter, Sepp & Jürgen Schmidhuber (1997), ‘Long Short-Term Memory’, Neural Comput. 9(8), 1735–1780.
URL: http://dx.doi.org/10.1162/neco.1997.9.8.1735
- Holz, Thorsten, Moritz Steiner, Frederic Dahl, Ernst Biersack & Felix C. Freiling (2008), ‘Measurements and Mitigation of Peer-to-Peer-based Botnets: A Case Study on Storm Worm.’, LEET 8(1), 1–9.
URL: https://www.usenix.org/event/leet08/tech/full_papers/holz/holz_html/
- Hopper, Nicholas (2014), Challenges in Protecting Tor Hidden Services from Botnet Abuse, in N.Christin & R.Safavi-Naini, eds, ‘Financial Cryptography and Data Security’, number 8437 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 316–325.
URL: http://link.springer.com/chapter/10.1007/978-3-662-45472-5_21
- How Kaspersky Lab and CrowdStrike Dismantled the Second Hlux/Kelihos Botnet: Success Story (2012).
URL: http://www.kaspersky.com/about/news/virus/2012/How_Kaspersky_Lab_and_CrowdStrike_Dismantled_the_Second_Hlux_Kelihos_Botnet_ Success_Story
- How to Send Email Using Telnet (n.d.).
URL: http://www.wikihow.com/Send-Email-Using-Telnet
- Huge spam botnet Grum is taken out by security researchers – BBC News (2012).
URL: http://www.bbc.com/news/technology-18898971
- IRC.org – Home of IRC (2005).
URL: http://www.irc.org/
- Jackson, Alden W., David Lapsley, Christine Jones, Mudge Zatko, Chaos Golubitsky & W. Timothy Strayer (2009), SLINGbot: A system for live investigation of next generation botnets, in ‘Conference For Homeland Security, 2009. CATCH’09. Cy- bersecurity Applications & Technology’, IEEE, pp. 313–318.
URL: http://ieeexplore.ieee.org/xpls/abs_all.jsp?arnumber=4804461
- Kang, Lachlan (2014), ‘Efficient botnet herding within the Tor network’, Journal of Computer Virology and Hacking Techniques 11(1), 19–26.
URL: http://link.springer.com/article/10.1007/s11416-014-0229-4
- Karim, Ahmad, Rosli Bin Salleh, Muhammad Shiraz, Syed Adeel Ali Shah, Irfan Awan & Nor Badrul Anuar (2014), ‘Botnet detection techniques: review, future trends, and issues’, Journal of Zhejiang University SCIENCE C 15(11), 943–983.
URL: http://link.springer.com/article/10.1631/jzus.C1300242
- Kassner, Michael (n.d.), ‘The top 10 spam botnets: New and improved’.
URL: http://www.techrepublic.com/blog/10-things/the-top-10-spam- botnets-new-and-improved/
- Kemmerer, Richard A. (2009), How to Steal a Botnet and What Can Happen When You Do, in S.Qing, C. J.Mitchell & G.Wang, eds, ‘Information and Communications Security’, number 5927 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 1–1.
URL: http://link.springer.com/chapter/10.1007/978-3-642-11145-7_1
- Khandelwal, Swati (2014), ‘FBI — Botnets Infecting 18 Computers per Second. But How Many of Them NSA Holds?’.
URL: http://thehackernews.com/2014/07/fbi-botnets-infecting-18-computers-per.html
- Khandelwal, Swati (n.d.), ‘Hackers Selling Unpatched Microsoft Windows Zero-Day Ex- ploit for $90,000’.
URL: http://thehackernews.com/2016/06/windows-zero-day-exploit.html
- Klapper-Rybicka, Magdalena, Nicol N. Schraudolph & Jürgen Schmidhuber (2001), Un- supervised Learning in LSTM Recurrent Neural Networks, in G.Dorffner, H.Bischof & K.Hornik, eds, ‘Artificial Neural Networks — ICANN 2001’, number 2130 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 684–691.
URL: http://link.springer.com/chapter/10.1007/3-540-44668-0_95
- Kleinbard, David & Richard Richtmyer (2000), ‘’I Love You’ virus sweeps the U.S. – May 5, 2000’.
URL: http://money.cnn.com/2000/05/05/technology/loveyou/
- Krebs, Brian (2011), ‘Most Malware Tied to ’Pay-Per-Install’ Market’.
URL: https://www.technologyreview.com/s/424241/most-malware-tied-to- pay-per-install-market/
- Krebs, Brian (2012), ‘Microsoft Takes Down Dozens of Zeus, SpyEye Botnets — Krebs on Security’.
URL: http://krebsonsecurity.com/2012/03/microsoft-takes-down-dozens-of-zeus-spyeye-botnets/
- Krebs, Brian (2016), ‘Botcoin: Bitcoin Mining by Botnet — Krebs on Security’.
URL: https://krebsonsecurity.com/2013/07/botcoin-bitcoin-mining-by- botnet/
- Lee, Hayoung, Taeho Kang, Sangho Lee, Jong Kim & Yoonho Kim (2013), Punobot: Mobile Botnet Using Push Notification Service in Android, in Y.Kim, H.Lee & A.Perrig, eds, ‘Information Security Applications’, number 8267 in ‘Lecture Notes in Computer Science’, Springer International Publishing, pp. 124–137.
URL: http://link.springer.com/chapter/10.1007/978-3-319-05149-9_8
- Lemos, Robert (2009), ‘Researchers Hijack a Drive-By Botnet’.
URL: https://www.technologyreview.com/s/415545/researchers-hijack-a- drive-by-botnet/
- Li, Huabo, Guyu Hu & Yun Yang (2012), Research on P2P Botnet Network Behaviors and Modeling, in C.Liu, L.Wang & A.Yang, eds, ‘Information Computing and Ap- plications’, number 307 in ‘Communications in Computer and Information Science’, Springer Berlin Heidelberg, pp. 82–89.
URL: http://link.springer.com/chapter/10.1007/978-3-642-34038-3_12
- Liu, Jing, Yang Xiao, Kaveh Ghaboosi, Hongmei Deng & Jingyuan Zhang (2009), ‘Botnet: Classification, Attacks, Detection, Tracing, and Preventive Measures’, EURASIP Journal on Wireless Communications and Networking 2009(1), 692654.
URL: http://jwcn.eurasipjournals.com/content/2009/1/692654
- Liu, Lei, Songqing Chen, Guanhua Yan & Zhao Zhang (2008), BotTracer: Execution- Based Bot-Like Malware Detection, in T.-C.Wu, C.-L.Lei, V.Rijmen & D.-T.Lee, eds, ‘Information Security’, number 5222 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 97–113.
URL: http://link.springer.com/chapter/10.1007/978-3-540-85886-7_7
- Lu, Wei, Mahbod Tavallaee & Ali A. Ghorbani (2009), Automatic discovery of botnet communities on large-scale communication networks, ACM Press, p. 1.
URL: http://portal.acm.org/citation.cfm?doid=1533057.1533062
- Masud, Mohammad M., Jing Gao, Latifur Khan, Jiawei Han & Bhavani Thuraisingham (2008), Peer to peer botnet detection for cyber-security: a data mining approach, ACM Press, p. 1.
URL: http://portal.acm.org/citation.cfm?doid=1413140.1413185
- mba & vbr (n.d.), ‘DDoS-Angriffe auf estnische Server waren kein “Cyberwar”’.
URL: http://www.heise.de/newsticker/meldung/DDoS-Angriffe-auf- estnische-Server-waren-kein-Cyberwar-138918.html
- Mills, Elinor (n.d.), ‘’Golden Cash’ botnet-leasing network uncovered’.
URL: http://www.cnet.com/news/golden-cash-botnet-leasing-network- uncovered/
- Musil, Steven (2012), ‘More than 600,000 Macs infected with Flashback botnet’.
URL: http://www.cnet.com/news/more-than-600000-macs-infected-with- flashback-botnet/
- Mutton, Paul (2010), ‘MasterCard attacked by voluntary botnet after WikiLeaks decision | Netcraft’.
URL: http://news.netcraft.com/archives/2010/12/08/mastercard-attacked-by-voluntary-botnet-after-wikileaks-decision.html
- Nadji, Yacin, Manos Antonakakis, Roberto Perdisci, David Dagon & Wenke Lee (2013), Beheading Hydras: Performing Effective Botnet Takedowns, in ‘Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security’, CCS ’13, ACM, New York, NY, USA, pp. 121–132.
URL: http://doi.acm.org/10.1145/2508859.2516749
- Namestnikov, Yury (2009), ‘The economics of Botnets – Securelist’.
URL: https://securelist.com/large-slider/36257/the-economics-of- botnets/
- Nappa, Antonio, Aristide Fattori, Marco Balduzzi, Matteo Dell’Amico & Lorenzo Cav- allaro (2010), Take a Deep Breath: A Stealthy, Resilient and Cost-Effective Botnet Using Skype, in C.Kreibich & M.Jahnke, eds, ‘Detection of Intrusions and Malware, and Vulnerability Assessment’, number 6201 in ‘Lecture Notes in Computer Sci- ence’, Springer Berlin Heidelberg, pp. 81–100.
URL: http://link.springer.com/chapter/10.1007/978-3-642-14215-4_5
- Nigam, Ruchna & Martijn Grooten (Editor) (2015), Virus Bulletin :: A timeline of mobile botnets, Vol. 2015, Virus Bulletin Ltd, The Pentagon, Abingdon Science Park, Abingdon, Oxfordshire OX14 3YP, England.
URL: https://www.virusbulletin.com/virusbulletin/2015/03/timeline-mobile-botnets
- Plohmann, Daniel & Elmar Gerhards-Padilla (2012), Case study of the Miner Botnet. Provos, Niels & Thorsten Holz (2008), Virtual Honeypots: From Botnet Tracking to Intrusion Detection, Addison-Wesley.
- Radcliff, Deborah (2002), ‘Steganography: Hidden Data’.
URL: http://www.computerworld.com/article/2576708/security0/ steganography–hidden-data.html
- Rahim, Aneel & Fahad T. bin Muhaya (2010), Discovering the Botnet Detection Tech- niques, in T.-h.Kim, W.-c.Fang, M. K.Khan, K. P.Arnett, H.-j.Kang & D.Ślęzak, eds, ‘Security Technology, Disaster Recovery and Business Continuity’, number 122 in ‘Communications in Computer and Information Science’, Springer Berlin Heidel- berg, pp. 231–235.
URL: http://link.springer.com/chapter/10.1007/978-3-642-17610-4_26
- Raza, Ali (2014), ‘Xsser iOS Trojan Spying on Hong Kong Protesters — Security Gladiators’.
URL: https://securitygladiators.com/2014/10/09/xsser-ios-trojan-spying-hong-kong-protesters/
- Rossow, Christian, Dennis Andriesse, Tillmann Werner, Brett Stone-Gross, Daniel Plohmann, Christian J. Dietrich & Herbert Bos (2013), Sok: P2pwned-modeling and evaluating the resilience of peer-to-peer botnets, in ‘Security and Privacy (SP), 2013 IEEE Symposium on’, IEEE, pp. 97–111.
URL: http://ieeexplore.ieee.org/xpls/abs_all.jsp?arnumber=6547104
- Scanlon, Mark & Tahar Kechadi (2012), Peer-to-Peer Botnet Investigation: A Review, in J. J. J. H.Park, V. C. M.Leung, C.-L.Wang & T.Shon, eds, ‘Future Information Technology, Application, and Service’, number 179 in ‘Lecture Notes in Electrical Engineering’, Springer Netherlands, pp. 231–238.
URL: http://link.springer.com/chapter/10.1007/978-94-007-5064-7_33
- Schwartz, Mathew J. (n.d.), ‘Inside The Booming Botnet Industry’.
URL: http://www.informationweek.com/security/vulnerabilities/inside- the-booming-botnet-industry/231600904
- Security, heise (n.d.), ‘DDoS-Attacke auf Estland: Keine Verbindung nach Moskau’.
URL: http://www.heise.de/security/meldung/DDoS-Attacke-auf-Estland- Keine-Verbindung-nach-Moskau-134693.html
- Security, Help Net (2010), ‘Massive Mariposa botnet shut down’.
URL: https://www.helpnetsecurity.com/2010/03/03/massive-mariposa-botnet-shut-down/
- Security, Help Net (2011), ‘Global spam drops by a third as Rustock botnet is disman- tled’.
URL: https://www.helpnetsecurity.com/2011/03/29/global-spam-drops-by-a-third-as-rustock-botnet-is-dismantled/
- Security, Help Net (2016), ‘Thousands of websites exploited for illegal SEO tactics’.
URL: https://www.helpnetsecurity.com/2016/06/13/websites-exploited- illegal-seo-tactics/
- Shirley, Brandon & Chad D. Mano (2008), A Model for Covert Botnet Communication in a Private Subnet, in A.Das, H. K.Pung, F. B. S.Lee & L. W. C.Wong, eds, ‘NET- WORKING 2008 Ad Hoc and Sensor Networks, Wireless Networks, Next Generation Internet’, number 4982 in ‘Lecture Notes in Computer Science’, Springer Berlin Hei- delberg, pp. 624–632.
URL: http://link.springer.com/chapter/10.1007/978-3-540-79549-0_54
- SIMDA: A Botnet Takedown (2015).
URL: https://blog.trendmicro.com/trendlabs-security-intelligence/ simda-a-botnet-takedown/
- Singh, Sundeep, Geok Meng Ong, Joonho Sa, Ronghwa Chong & Shinsuke Honjo (2015), ‘Evolution of Dridex « Threat Research Blog | FireEye Inc’.
URL: https://www.fireeye.com/blog/threat-research/2015/06/evolution_of_dridex.html
- Snort – Network Intrusion Detection & Prevention System (n.d.).
URL: https://www.snort.org/
- Stankovic, Srdjan & Dejan Simic (2009), ‘Defense strategies against modern botnets’, arXiv preprint arXiv:0906.3768 .
URL: http://arxiv.org/abs/0906.3768
- Stevanovic, Matija, Kasper Revsbech, Jens Myrup Pedersen, Robin Sharp & Chris- tian Damsgaard Jensen (2012), A Collaborative Approach to Botnet Protection, in G.Quirchmayr, J.Basl, I.You, L.Xu & E.Weippl, eds, ‘Multidisciplinary Research and Practice for Information Systems’, number 7465 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 624–638.
URL: http://link.springer.com/chapter/10.1007/978-3-642-32498-7_47
- Stewart, Amanda (2015), ‘Macros Galore « Threat Research Blog’.
URL: https://www.fireeye.com/blog/threat-research/2015/10/macros_galore.html
- Tillmann (2012), ‘P2P Botnet Kelihos.B with 100.000 Nodes Sinkholed’.
URL: https://www.crowdstrike.com/blog/p2p-botnet-kelihosb-100000-nodes-sinkholed/
- Vania, Jignesh, Arvind Meniya & H. B. Jethva (2013), ‘A review on botnet and detection technique’, Int J Comput Trends Technol 4(1), 23–29.
URL: http://ijcttjournal.org/Volume4/issue-1/IJCTT-V4I1P104.pdf
- Venkatesh, G. Kirubavathi & R. Anitha Nadarajan (2012), HTTP Botnet Detec- tion Using Adaptive Learning Rate Multilayer Feed-Forward Neural Network, in I.Askoxylakis, H. C.Pöhls & J.Posegga, eds, ‘Information Security Theory and Prac- tice. Security, Privacy and Trust in Computing Systems and Ambient Intelligent Ecosystems’, number 7322 in ‘Lecture Notes in Computer Science’, Springer Berlin Heidelberg, pp. 38–48.
URL: http://link.springer.com/chapter/10.1007/978-3-642-30955-7_5
- Venkatesh, G. Kirubavathi, V. Srihari, R. Veeramani, R.m. Karthikeyan & R. Anitha (2013), ‘HTTP botnet detection using hidden semi-Markov model with SNMP MIB variables’, International Journal of Electronic Security and Digital Forensics 5(3-4), 188–200.
URL: http://www.inderscienceonline.com/doi/abs/10.1504/IJESDF.2013.058653
- Vigna, Giovanni (n.d.), ‘Giovanni Vigna’.
URL: http://www.cs.ucsb.edu/~vigna/
- von Clausewitz, Carl (1989), On War, Indexed Edition, reprint edition edn, Princeton University Press, Princeton, N.J.
- Wang, Peng, Chengwei Zhang, Xuanya Li & Can Zhang (2013), A Mobile Botnet Model Based on Android System, in Y.Yuan, X.Wu & Y.Lu, eds, ‘Trustworthy Computing and Services’, number 426 in ‘Communications in Computer and Information Sci- ence’, Springer Berlin Heidelberg, pp. 54–61.
URL: http://link.springer.com/chapter/10.1007/978-3-662-43908-1_7
- Werner, Tillman (2011), ‘Botnet Shutdown Success Story: How Kaspersky Lab Disabled the Hlux/Kelihos Botnet – Securelist’.
URL: https://securelist.com/blog/research/31058/botnet-shutdown-success-story-how-kaspersky-lab-disabled-the-hluxkelihos-botnet-15/
- What is Click Fraud? – Definition from Techopedia (n.d.).
URL: https://www.techopedia.com/definition/5157/click-fraud
- Young, Jeff & Tom Barth (2014), ‘iOS and Android OS Targeted by Man-in-the-Middle Attacks’.
URL: https://www.akamai.com/de/de/about/news/press/2014-press/ios-and-android-os-targeted-by-man-in-the-middle-attacks.jspand-android-os-targeted-by-man-in-the-middle-attacks.jsp
- Zetter, Kim (2014), ‘Hacker Lexicon: What Is a Zero Day?’.
URL: https://www.wired.com/2014/11/what-is-a-zero-day/
- Zhuang, Li, John Dunagan, Daniel R. Simon & HelenJ. Wang (2008), ‘Characterizing Botnets from Email Spam Records’.
URL: https://www.usenix.org/legacy/event/leet08/tech/full_papers/zhuang/zhuang_html/

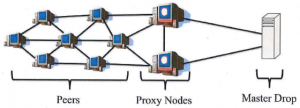
Leave a Reply
You must be logged in to post a comment.