Welcome to our journey through the blockchain, since the emergence of Bitcoin, one of the most trending topics of the global digital village. After reading this blog post, you’ll have a basic understanding of the technology, a wide overview of future use cases and are able to differentiate between realistic potential and hype.
In the first part we explain the blockchain technology, for everybody who’s not that deep in the topic or needs a quick recap:
What is an transaction?
What’s inside a block?
How does the merkle tree work?
Why do we need a proof of work?
In the second part we take a closer look on the future of the blockchain:
What are Proof-of-Stake, Casper and Algorand?
What are the risks and opportunities of the technology?
Where are the future uses cases of the blockchain?
Is there a blockchain revolution or just another hype?
Content
Blockchain Technology
Transition / Transaction
Blocks
Merkle Tree
Proof-of-Work
Blockchain Future
Consensus Protocols
Risks and Opportunities
Future Use Cases
Summary
Blockchain Technology
Transition / Transaction
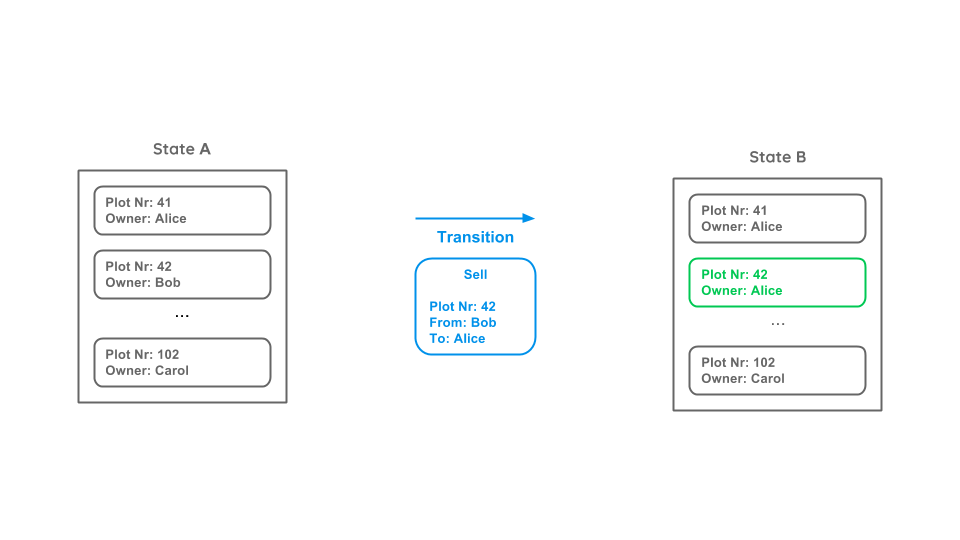
Let’s assume we have a digital marketplace with various plots and owners represented in the current state (State A). Bob wants to sell his plot (42) to Alice and therefore creates a transition (also called transaction). The transition contains the plot number, the seller and the recipient. This transition leads to a new state (State B).
We will not focus on public private key encryption in this blog post, but just as a note: To ensure that only Bob and not Alice can create this transition, the owner is not described by a name but a public key. To create a valid transition, it has to be signed with the corresponding private key, that only the owner knows.
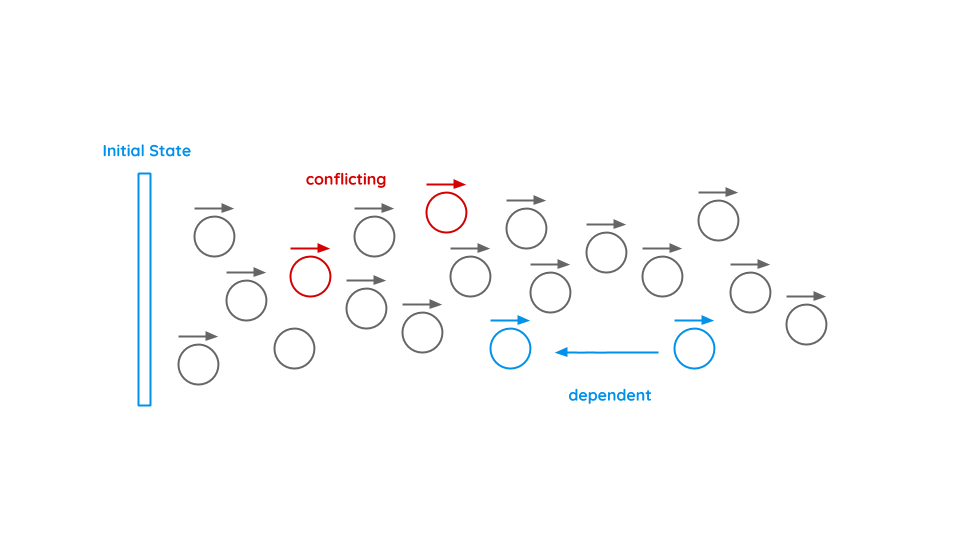
As time goes by, various transactions will be made. Some of them can be dependent, e.g. if Bob sells a plot to Alice and she sells it to Carol. Other may be conflicting, e.g. if Bob sells the same plot to two or more people. In order to define the current state, every transaction must be checked and brought into the right order.
Blocks
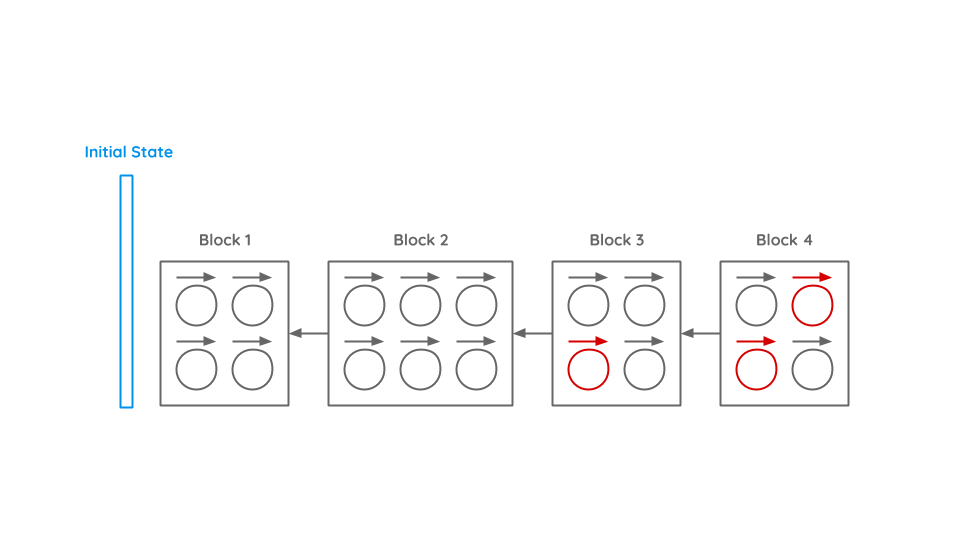
To sort this chaos, transactions are bundled into blocks. Inside a block all transactions must be in the right order to correctly solve dependencies. Also conflicting transactions (inside the block or to previous blocks) are not allowed. A new block will always be build on the last block.
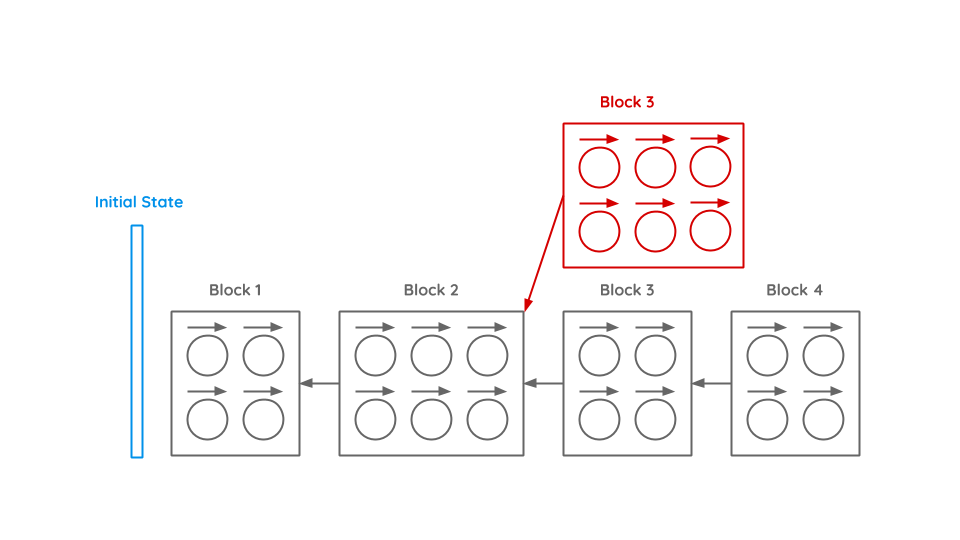
As the blockchain is a distributed peer-to-peer system and it takes some time till every participant is informed about new blocks, there might coexist different chains. To determine which chain is the correct chain, always the longest chain wins. If a block generator is building a block and receives the notification that a new block was created and she is therefore not working on the longest chain, she aborts immediately and starts working on the new chain.
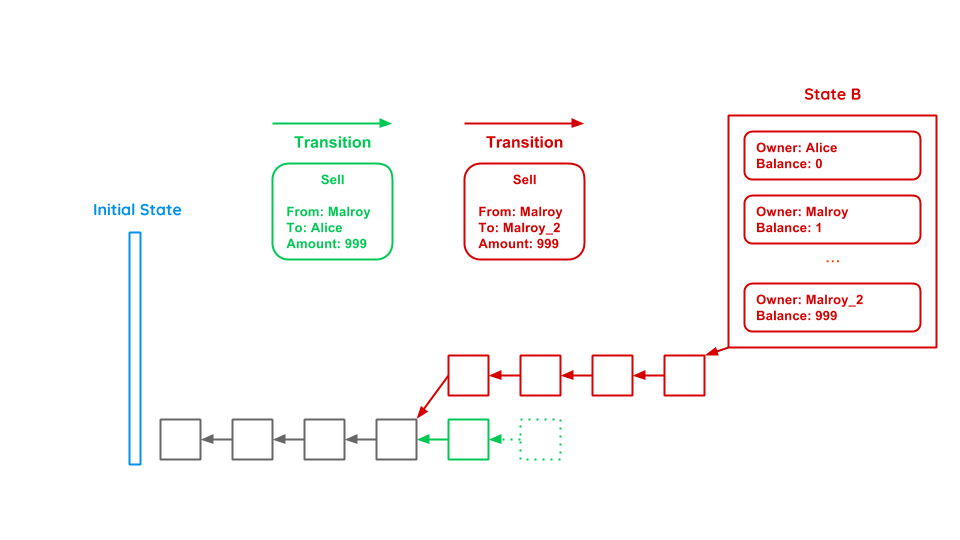
Let’s assume we have an evil participant Malroy. He wants to buy a notebook from Alice for 999€. He triggers a transaction and waits until the block with this transaction is built. Alice sees the new block and gives Malroy the notebook. Afterwards Malroy builds new blocks based on the block where he still owns the money until the network thinks that Malroys’ chain is the correct one, as it is the longest. To solve this problem we have to look on the content of a block (Merkle Tree) and the Proof-of-Work.
Merkle Tree
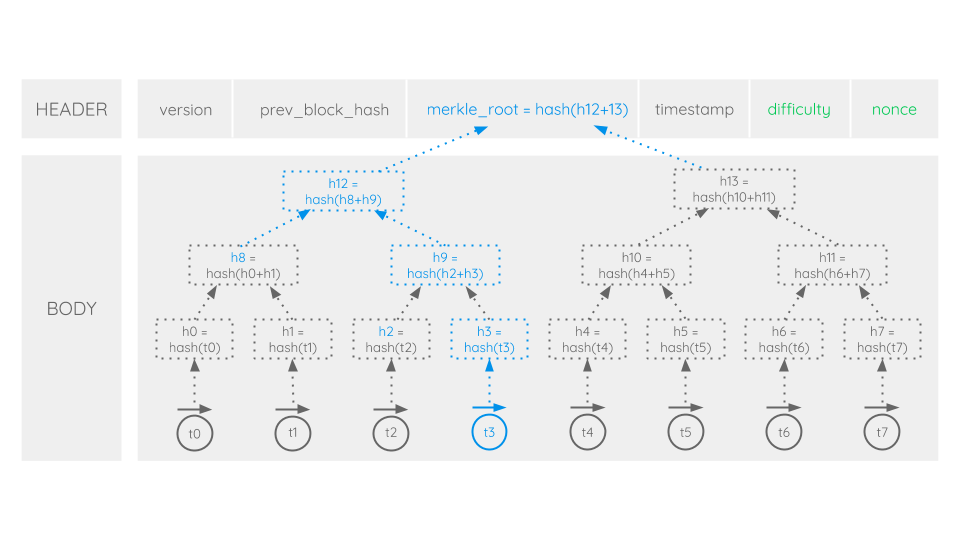
In order to ensure data integrity of blocks and efficient data verification, the concept of merkle trees is applied. To understand this concept, we need to take a closer look at blocks, their transactions and how they are organized.
As computer scientists tend to organize data in headers and bodies, the same is applied to blocks. The body contains all transactions of a block. In preprocessing of block generation, conflicting transactions are either resolved or rejected and depended ones are arranged in their sequential order. The very first transaction in a block is generally a so called coinbase transaction (t0). It is used to reward a miner (see Proof-of-Work) with the block reward for their work and all transaction fees of a block. Except for its special purpose, it’s just like any other transaction on the network and followed by all the other block’s transactions.
In the merkle tree we would like to build up, every transaction of a block can be regarded as a leaf of the tree. Each leaf consists of the hash of its transaction. For example in the picture shown above, hash 0 (h0) represents the hash of transaction 0 (t0). Now in order to construct the whole tree, leaves are paired and their paired data is hashed again. In our example hash 0 (h0) and hash 1 (h1) are paired and hashed to the new hash(h0+h1). Then, the results are paired and hashed again and this procedure is repeated until a single hash remains: the merkle root. Among with other data, the merkle root is kept in the header of a block (see Proof-of-Work).
Having built the merkle tree up to its merkle root allows us to make data verification very efficient. Now, hashes can be used instead of full files. For example, in order to verify the integrity of a specific transaction, say transaction 3 (t3), a verifier will only need to download the corresponding merkle branch (marked blue). Afterwards transaction 3 (t3) will be hashed (h3) and the merkle branch recalculated up to the merkle root. When the calculated merkle root exactly matches the merkle root of the block header, the verifier can be sure that the transaction has not been altered or manipulated in any way. So when this concept is applied to the whole block body, the merkle tree with its merkle root in the block’s header ensures that neither the body’s transactions, their number and order nor a single transaction’s data was altered in any manner.
Proof-of-Work
With the rise of Bitcoin as the most popular blockchain technology so far, the so called Proof-of-Work (PoW) consensus algorithm became famous. Bitcoin is based on a public and permissionless blockchain. So basically all participants of the network can contribute to the generation of blocks. But with anybody being able to add another block to the chain’s end, whose and which chain should become the network-wide accepted one? Satoshi Nakamoto, the creator of Bitcoin, came up with a solution to this problem: the Proof-of-Work algorithm. According to his idea, in order to generate a new block, a contributor should PROOF that he had invested a certain amount OF WORK. The work should be relatively hard to deliver whereas the proof should be easy to verify.
To understand the PoW, we need to take a closer look at the header of a block (see Figure 6). We already know the merkle root from the previous paragraphs. So what are the other parts and which are relevant when it comes to PoW?
The first part of the header contains the version. This is simply the blockchain’s protocol version number. The prev_block_hash stores the hash of the previous block’s header. This is a crucial part of blockchain technology. By referencing the previous block, it’s integrity is ensured. Neither the header nor the body data of the previous block can be altered or manipulated in any way after being chained to the blockchain. Otherwise it’s hash would be different and therefore the block not valid anymore. And since each block references its predecessor the integrity and immutability of the whole blockchain is ensured.
The third part of the header is a timestamp. It contains simply a unix timestamp that represents the block’s creation time. So let’s take a closer look at the two remaining parts of the header: difficulty and nonce. Spoiler alert: these are the parts relevant for Proof-of-Work creation. So how does it actually work to proof that you invested enough work to be allowed to chain your new created block to the end of the blockchain and therefore make it become the network-wide accepted state? Difficulty determines the number of leading zeros the hash of the header must contain. Because chances are very low to match difficulty when just hashing the header once, there must be a possibility to manipulate the header data marginally. This is what nonce is for. If the hash of the header does not correspond with difficulty one simply will increment nonce and try to hash again. If incrementation of nonce was not sufficient at all, there is also the possibility of changing the coinbase transaction (see Merkle Tree) marginally. This will change the merkle root and subsequently the header data. After coinbase manipulation, nonce incrementation can restart from the beginning. This whole procedure is repeated until someone in the network finally manages to find a constellation where the header’s hash matches the predetermined number of leading zeros. If this is the case, the corresponding block will get propagated to the network as the last valid block at the end of the collective chain and PoW calculation will begin with the succeeding block.
But with moore’s law and constantly increasing computing power, calculating the PoW of a block should become easier over time, shouldn’t it? Well, because of that, difficulty can dynamically be adjusted to the network’s computing power. Take the Bitcoin network for example: here, difficulty adjusts every 2016 blocks and therefore the average block generation can be maintained constant at about 10 minutes per block.
So PoW can help to keep the network in consensus about what is the longest chain and therefore the network’s current accepted state. But calculating does need computing power and therefore costs electricity and then again money. That’s why network participants need to be incentivised to contribute their computing power to the network. This is done by offering a reward to the one who manages to successfully calculate PoW. As we mentioned in the paragraphs about Merkle Tree, the very first transaction of a block is a special one, called coinbase transaction. Within this transaction a block generator can transfer the block calculation reward and all transaction fees of the block to herself. The reward is newly generated shortly after the new block was chained to the blockchain. This is why the process of contributing to the network is also referred to as mining and the block generators as miners.
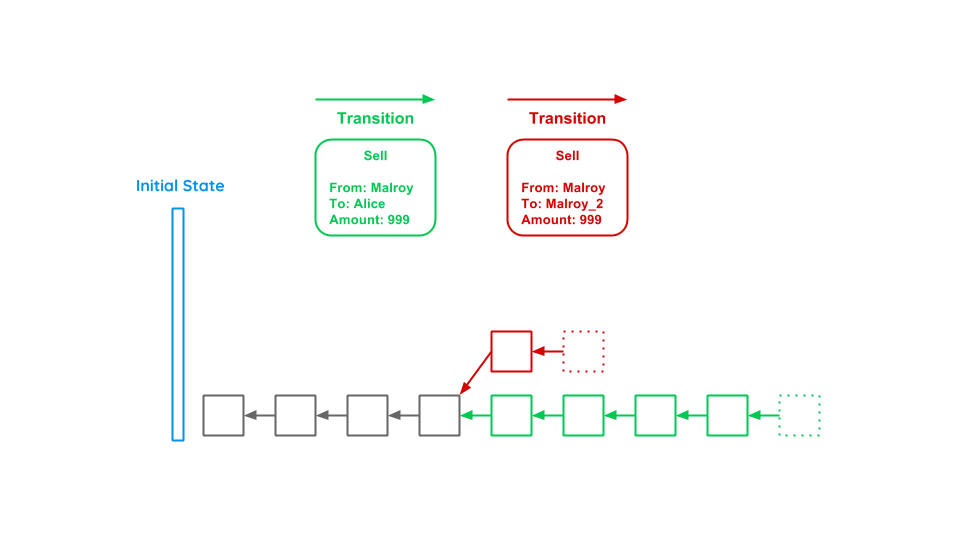
So let’s go back to Malroy’s double spending attack described earlier. In this scenario, Malroy first transmitted the money to Alice and after having received the notebook, he started forking the chain (red) where he still owns the money and building new blocks onto it in order to make the fork the longest chain. This is where PoW kicks in preventing Malroy from doing so. As the network possesses much more computing power as Malroy, it will always outperform him on the long run solving the computational puzzle and thereby generating the Proof-of-Work. Malroy could start forking and mining new blocks to his fork, but as the network will continue working on the green chain, he could stochastically only be successful if he owned more than 50% of the computing power (which is referred to as the 51% attack). The attack gets even more expensive and unlikely to succeed, the more blocks Alice waits before handing her notebook over to Malroy. So the PoW algorithm creates a significant opportunity cost: potentially bad miners as Malroy could have earned block rewards during the time of an attack instead of wasting resources on probably failing attacks. With this in mind, Malroy will rather concentrate on mining on the network’s longest chain in order to gain block rewards instead of waisting his resources and therefore contribute to the system’s stability as whole.
Let’s take another quick look at Bitcoin, the current largest blockchain network relying on PoW. Here, the computational mining power increased enormously over the last years due to increased public interest and therefore skyrocketing prices. Miners organize themselves professionally in so called mining pools and use special hardware to increase their chances to gain block rewards. With about 4 billion GH/s in total, the Bitcoin network is estimated to consume about the same amount of energy as Ireland does. In recent years criticism grew about the PoW’s poor ecological balance. That’s why alternative blockchain consensus protocols increasingly gained popularity. One of which is the so called Proof-of-Stake consensus that tries to solve PoW’s ecological downsides. So let’s have a closer look if it can do so whilst keeping the same high standard of security in the following paragraphs.
Blockchain Future
Consensus Protocols
Despite many attacks on the Proof-of-Work protocol, it has shown to be a stable mechanism to incentivize miners to contribute to the digital ledger’s integrity. Nevertheless, the protocol is subject to more and more criticism for its poor ecological balance. There are no exact numbers about its energy consumption, thus one has to rely on estimates. So let’s have a quick look at Bitcoin as the world’s largest running blockchain system and its energy consumption. Estimates assume, that a single Bitcoin transaction – and there may be up to 7 per second – consumes about 1 to 3 times as much energy as an average American household in 24 hours. Or in terms of whole bitcoins: each new mined bitcoin is assumed to require about 5500kW electricity. And there are further drawdowns. As the process of mining became a lucrative business, the computational power is more and more centralized into bigger but less groups called mining pools. Such centralization opposes the idea of a decentralized network. Furthermore it does not make good economic sense anymore to mine with one’s general purpose hardware like CPUs or GPUs. When it comes to mining hardware, ASICs (application-specific integrated circuits) just created for the purpose of mining took over the field entirely. So Satoshi Nakamoto’s idea of one CPU one vote is already obsolete. With these drawdowns in mind, many people started thinking about better consensus protocols. Let’s have a closer look at one of the most promising ones, the Proof-of-Stake (PoS), and how it tries to overcome the PoW’s problems discussed.
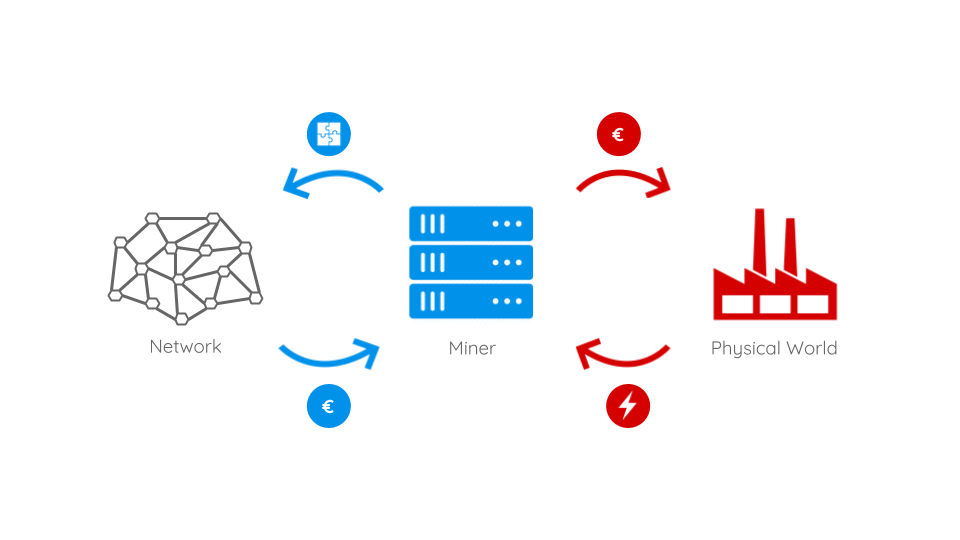
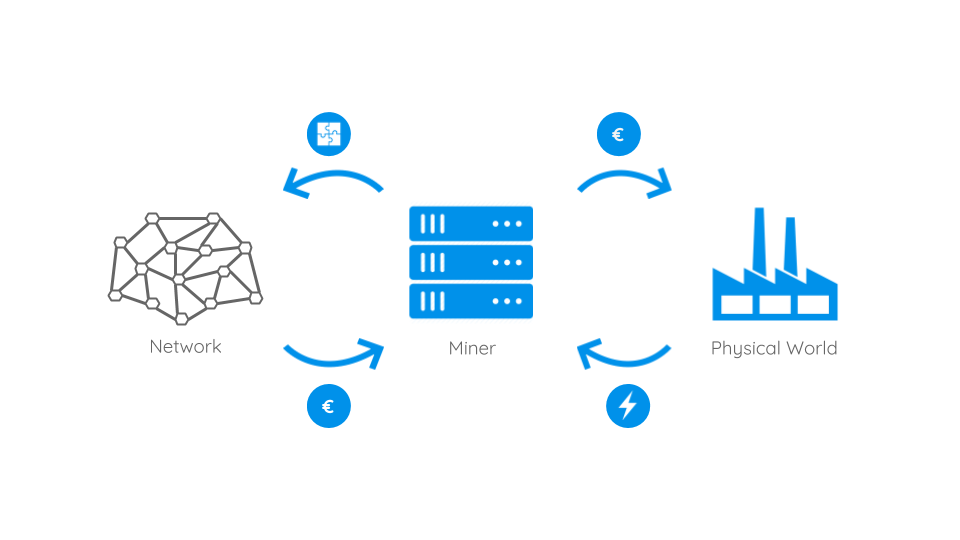
To understand PoS we first have to understand how the flow of money and gain of mining power works in PoW systems. The above image shows that miners will buy real world hardware and electricity. With these, they try to solve PoW puzzles and gain the linked rewards. These rewards are, to a certain proportion, reinvested in new hardware and electricity. Condensed one could observe, that the more a miner invests the more rewards she will earn. At this point, the idea of PoS kicks in: so what if we skipped the real world part of hardware and electricity consumption and implemented a kind of virtual mining instead? In such a scenario, miners with a certain share – or better: stake – of coins will be able to mine new blocks and gain rewards with the probability being proportional to their amount of stake. Let’s make it more clear with an example: In the PoW world someone with 5% of the computational mining power will probably earn about 5% of the mining rewards (on the long run). So wouldn’t it be great if someone with a stake of 5% of all coins would earn 5% of the mining rewards but without having to burn real world energy and raw materials? Your answer is ‘yes’? – then welcome to the idea of PoS: here the chance of a participant to create the next block depends on her wealth – her stake. That’s why new blocks are usually said to be minted or forged instead of minded. In a PoS cryptocurrency there would be no need to create new coins as block rewards since the block creators can easily be rewarded with transaction fees. And these fees can even be much lower than the ones of PoW systems because block creation will only consume a fractional amount of energy and therefore money. Besides lower energy consumption and transaction fees another advantage is that a 51% attack on a blockchain system will be much more expensive. Let’s make it clear with a simple example: in the largest PoW blockchain Bitcoin the investments in hardware account to about 10% of the total value. This means with about 5% of the total value 50% of the mining power can be gained. Whereas in PoS systems an attacker would really need to own 50% of all coins which leads us to another important argument for PoS systems: the basic assumption is that someone with a big stake in a blockchain system (e.g. a cryptocurrency) is inherently interested in its stability. With increasing stake the interest in the system’s stability rises equally. So stakeholders with a lot of influence on a blockchain – more precisely with a lot of stake – are very much incentivized to benefit the system as a whole and therefore increase their stakes value than to behave maliciously.
With all these advantages in mind, why don’t we entirely switch to PoS blockchains instead? Well, the consensus protocol comes with some serious downsides as well. One of which is concentration of power as rich participants will constantly become richer. Another one is incentivized coin hoarding which in case of cryptocurrencies diametrically opposes the idea of constant circulation. But maybe the most significant drawdown comes along with its allegedly biggest advantage: virtual mining. With no real world investment there is also no real punishment for miners/minters that do work on multiple chains. In PoW mining attacks have a significant opportunity cost, since miners could have earned block rewards during the time of an attack instead of wasting resources on probably failing attacks. Even without possessing the majority of stake, a PoS minter could chase his luck, fork the longest chain, simultaneously work on it and try to make it become the blockchain’s new valid state and therefore enable double spending attacks. Although chances are low, there are no means for keeping minters from doing so as there is no real world investment. If an attack fails no record of it will be kept on the eventual longest chain. Thus, rational miners may tend to constantly attempt to fork the chain. This problem is also referred to as the nothing-at-stake problem.
Various attempts have been made to address the PoS’s nothing-at-stake issue and many different approaches exist. Ethereum, the largest smart contract enabled blockchain, for example plans to switch from PoW to a new PoS-based protocol called Casper. Casper implements punishments for unnecessary forks of the chain. Minters will need to sign new minted blocks with their corresponding stake’s private key. If a minter ever uses the same stake to sign two inconsistent chains other minters who prove so will be allowed to collect a portion of the stake as bounty in a so called Proof-of-Misbehavior.
Another attempt to address the nothing-at-stake problem is MIT professor Silvio Micali’s proposal of the so called Algorand consensus. As other so called Delegated PoS protocols suggest, only a certain group of minters is selected to mint a new block. Algorand selects them by using cryptographic sortition. The so called verifiers are derived by hashing the last created block’s header. As an advantage, the network does not have to agree on the verifiers as they are mathematically determined. Another one is that the determination can only take place when the last block was successfully created and therefore no one will know the new verifiers beforehand. Furthermore all network participants can check if a verifier was validly selected. For additional protection, every new created block contains random transactions to randomize block headers. Moreover to prevent sybil attacks, verifiers can only be selected if they own a certain amount of stake.
After having selected the verifiers, one of them will be defined as secret leader. She will create the block, hand it over to the verifiers and no longer participate in the process. The verifiers then do verify the leader’s block (if valid) and will try to agree with the other ones using a byzantine algorithm. After three rounds there will either be a two thirds majority or the block is declared invalid and given to the network as empty block (but with a new header). In both cases the whole process will restart from the beginning with a new group of verifiers being selected.
Both, Casper and Algorand, sound promising but still are solely theoretical approaches and yet have to prove stability and robustness in the field. But they are not the only alternative consensus protocols being suggested or used. The debate about PoW’s disadvantages has led to many different approaches like Proof-of-Deposit, Proof-of-Use, Proof-of-Authority, Proof-of-Activity, Proof-of-Stake-Time, Proof-of-Storage, Proof-of-Publication and many more. Discussing all of them in detail is certainly beyond the scope of this article. It needs to be noted that Satoshi Nakamoto’s PoW algorithm came after decades of failed attempts of creating a cryptocurrency and managed to hit the sweet spot between robustness and practical trade-offs. PoW supporters argue that security fundamentally requires burning real resources, real computational hardware and electrical power. Following this drift, the PoW’s apparent waste can be interpreted as the cost of security. But as this argument has not been proven and many alternative blockchain systems emerged in recent years, time will tell which protocols will turn out to be the most secure, robust and stable ones while suiting large scale requirements.
Risks and Opportunities
Before thinking about future use cases of the blockchain, let’s summarize the pros and cons of this technology.
| Pros | Cons |
|---|---|
| Transparency (no trust) | Surveillance |
| Data integrity | Irreversibility (code is law) |
| Process integrity | High energy consumption |
| Pseudonymity | No anonymity |
| High reliability | Securing private keys |
| Fast transactions | Attacks (DDoS, spam) |
| Smart contracts | Scalability |
Future Use Cases
The revolution of the blockchain technology started with the emergence of Bitcoin as the first reliable distributed cryptocurrency. But there are many other use cases besides currencies. The Euro Banking Association classifies three different stages: cryptocurrencies, asset registration and application stack. Basically, asset registration takes the idea of cryptocurrencies and puts it further from digital coins to all kinds of assets being managed on a blockchain. These assets could be any kind of real world estates from electronic devices to cars or even real estate titles. Application stack as the last stage of blockchain evolution is the idea of assigning executable source code to a blockchain address. A transaction made to such an address will trigger code execution on each network node of the blockchain and save the computed state onto the chain. So in this final stage the whole blockchain network and its computing power can be used as a worldwide distributed incorruptible supercomputer. So let’s take a closer look at possible future use cases in all three stages of blockchain evolution.
With the increasing success of cryptocurrencies the banking sector started to adapt the technology. By handling transactions between different banks with a blockchain rather than conventional systems like SEPA, the process gets faster and cheaper. In contrast to cryptocurrencies, they target a so called private or permission based blockchain and not a public one, as the banks still want to keep their middleman position between customers. In addition to finance, other businesses can use the blockchain as well, e.g. logistics or accounting. Dependent on the use case private, shared and public systems are possible.
Smart Contracts are the classic example use case of the application stack stage. Having code being deployed to and managed by a blockchain system that is executed by the network offers many interesting future use cases. For example car sharing or apartment leasing (think of AirBnB’s business model) can be made very easily. In such a scenario, a user would for example simply send a transaction including the fee and a security deposit to the blockchain address the apartment is managed on. The smart contract would be triggered, the transaction validated, the deposit hold in escrow and the user granted access to the apartment for example by sending her the corresponding log in credentials of a smart lock. At the end of leasing time the user would return the apartment by sending another transaction to the smart contract. The contract would then order a cleaning service and if this service confirmed that everything was OK, the security deposit would be refunded to the user.
The concept of smart contracts can furthermore be applied to the ruleset of organizations. So called DAOs (Decentralized Autonomous Organizations) or DACs (Decentralized Autonomous Corporations) have all its rules stored to, maintained and executed by a blockchain. Their code is law. Therefore the application of rules are incorruptible by humans and this kind of organizations can be constructed to run completely autonomously. For example, a group of Berlin design students created the DAO project Terra0 which is a forest that belongs to itself and is fully self-administered. And since the appearance of Ethereum many DAOs/DACs emerged and even more will probably do in the future.
There are also considerations to represent judicial contracts with smart contracts. That might reduce the need of a trial in court. In terms of public administration many scenarios and all kind of asset registrations, e.g. real estates or addresses, are imaginable to speed up processes and ease local authorities. Also eVoting is associated with the blockchain to benefit from its transparency and pseudonymity.
But the technology offers also new possibilities for computer science. E.g. BigchainDB is a database build on top of the blockchain that acts like common databases but with the benefit of immutability. Another use case might be to use the decentralized peer-to-peer blockchain network for cloud computing. An example is to replace DNS servers and store DNS information with the blockchain (e.g. Namecoin). With the rapidly growing amount of connected devices (Internet Of Things) these data could be transferred by a peer-to-peer system and stored within a blockchain network.
Summary
Now that we talked about the technology itself and many possible use cases, we want to finish by sharing our own thoughts about where the blockchain might be revolutionizing and where it seems overrated.
Cryptocurrencies have already shown that they provide a reasonable alternative, as they are not government-controlled and self-regulating. The technology may also help to make public administration more efficient, transparent and automated. With the declining trust in democracy, as the 2016 US presidential elections show, blockchain based eVoting may offer a transparent system that modernizes democratic decisions.
On the other hand when it comes to smart contracts, law is not a matter of black and white decisions and it seems very complicated to apply them to the judicial sector. The concept of code is law might also be problematic, as everyone who develops software knows that there is no bug free code. In terms of ecology the Proof-of-Work with it’s high energy consumption does not offer a reasonable solution, but might be solved with previously mentioned or future consensus protocols. We see another risk in the occupation of the transparent technology into hidden private blockchains, as the financial complex is already up to.
In summary the blockchain technology offers many opportunities and completely new business models. However sometimes blockchain enthusiasts tend to mix them up with the possibilities of digitization and automation. Especially in the area of smart contracts, conventional IT solutions can be a better choice depending on the use case. Although blockchain already proved its strength and reliability in terms of cryptocurrencies, it is a very young technology. With blockchain riding on top of Gartner’s Hype Cycle, the next years will bring exciting developments and more clearance which areas it will really revolutionize.
Kuhn, Korbinian [kk129@hdm-stuttgart.de]
Mauser, Steffen [sm182@hdm-stuttgart.de]

Leave a Reply
You must be logged in to post a comment.