
It isn’t always necessary to attack by technical means to collect information or to penetrate a system. In many cases, it’s more effective to exploit the human risk factor. To successfully protect yourself and your company from social engineering, you’ve to understand how a social engineer works. And the best way to do this is by listening to the world’s most wanted hacker Kevin David Mitnick. Nowadays, the former social engineering hacker uses his expert knowledge to advise companies on how to protect themselves against such attacks. This blog entry is based on his bestseller “The Art of Deception: Controlling the Human Element of Security”. It sheds light on the various techniques of social engineering and enumerates several ways in which you can arm yourself against them.
Who’s This World’s Most Wanted Hacker?
Childhood and Adolescence
In 1963, the most wanted hacker, Kevin David Mitnick, was born in Los Angeles [1]. He grew up with his single mother who worked a lot as a consequence he spent a huge amount of time by himself. But he enjoyed his resulting freedoms.
At the age of 12, Kevin Mitnick found out how to use the Los Angeles bus network for free. For this, he had to elicit internal company secrets from the bus drivers, such as where to buy the right punch to validate empty tickets. He realized for the first time how useful his outstanding talent in manipulation could be.
In his high school years, Kevin Mitnick met a classmate who introduced him to the art of phone phreaking. This is a type of hacking where the attacker explores the telephone network by exploiting telephone systems and employees of telephone companies. The two of them spent a lot of time using the telephone network for their amusement and making free calls.
After graduating from high school, Kevin Mitnick studied computer science at the Computer Learning Center in Los Angeles. After only a few months and a hacked computer system, they made him a special offer. He had the choice either to run a project to improve computer security at the Computer Learning Center, or they would kick him out for hacking their system. He took the opportunity and run the project. In the end, he graduated cum laude.

Hard Times
Over the following years, Kevin Mitnick hacked into 40 major corporations [2]. He never damaged the systems or sold stolen information. He loved the intellectual challenge of breaking into systems and networks to find out how the technology works. And being always one step ahead was a big part of his satisfaction.

In 1992, Kevin Mitnick was on the FBI Most Wanted List for penetrating some of the best-secured computer systems in the USA. After a few years of fatiguing escape, he was arrested on February 15, 1995 [3]. He spent five years in prison followed by three years of supervised release during which time he was not allowed to use any computer system at all [1].

Kevin Mitnick Today
Kevin Mitnick is one of the global bestselling authors and wrote four books [2]. His first bestseller “The Art of Deception: Controlling the Human Element of Security” was published in 2002. The blog entry focuses on this work. Three years later his second book “The Art of Intrusion: The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers” was published. By the condition of the court, he wasn’t allowed to report on his experiences as a hacker for several years. Therefore, his work “Ghost in the Wires: My Adventures as the World’s Most Wanted Hacker” was released for the first time in 2011. His last book is from the year 2017 and bears the title “The Art of Invisibility: The World’s Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data”.
Furthermore, he’s the CEO of Mitnick Security [2]. Kevin Mitnick and his team analyze security risks and vulnerabilities of their clients using sophisticated technology and in-depth knowledge [4]. Some of their clients are for example Dell, Hewlett Packard, IBM, NASA, Oracle, Visa and MasterCard [5].
Besides, he’s the Chief Hacking Officer of KnowBe4 which is a security awareness training company [3]. And all around the world Kevin Mitnick gives presentations and talks about the latest hacking techniques [2].

What is a Social Engineer?
Social engineering uses influence and persuasion to deceive people by convincing them that the social engineer is someone he is not, or by manipulation. As a result, the social engineer is able to take advantage of people to obtain information with or without the use of technology.
Kevin Mitnick [6]
In simple words, social engineering is an activity in which people are made to do things for strangers that they wouldn’t normally do. It works primarily because employees have no idea of basic safety practices. And the social engineer also takes advantage of human credulity as well as the need to help other people.
To be a successful social engineer, he or she usually possesses very good social skills. It’s someone who is charming, polite and has sympathetic character traits. All these qualities lead people to immediately build a relationship with that person. Which is above all characterized by trust. An experienced social engineer can acquire practically all desired information with the help of the tactics and strategies of his trade.
The Cycle of Social Engineering
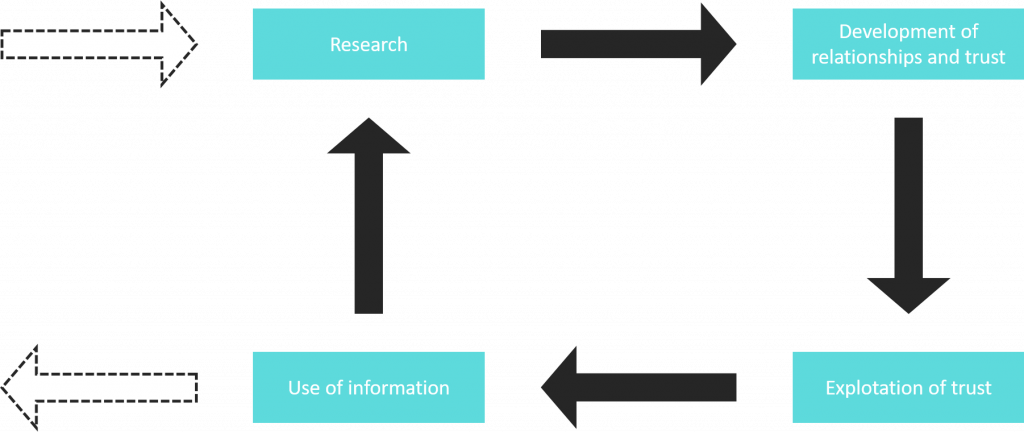
Everything starts with the research. The social engineer needs facts and information to know the intern jargon better. It’s requisite for developing relationships and trust in the next step. The research includes searching publicly accessible sources such as annual reports, newspaper clippings or content of websites. Sometimes dumpster diving could be necessary.
In the next phase, the social engineer develops relationships and trust. Therefore, he or she uses insider information or misrepresentation of identity. In some cases, the social engineer names references to a person known to the victim as well as taking advantage of the need for help or the bondage to authority.
After that, the attacker starts to exploit the trust. He or she’s requesting information or an action from the victim. Sometimes the social engineer manipulates the victim in such a way that he or she asks the attacker for help.
If the collected data isn’t the final information in demand. The social engineer returns to step one and repeats the whole cycle until the target is reached.
The Art of the Attacker: The 7 Steps to Get Someone to Do What the Attacker Wants
Some mentioned techniques are strongly interconnected. However, it’s neither necessary nor useful to use all techniques at the same time. But every technique can be advantageous at different times and for different victims. With every attack, a social engineer refines his or her sense of when which methods should be used. The following seven headlines are from Kevin Mitnick’s book “The Art of Deception” and correspond to chapters two to eight.
#1 When Innocuous Information Isn’t: The Hidden Value of Information
Even if individual pieces of information may be irrelevant in themselves when someone puts everything together the hidden value becomes visible. For example, when a social engineer collects pieces of information like department abbreviations and for what they’re responsible, he or she gets a clear picture of the internal structure of a company. Knowing the internal jargon and the structure of a company is very helpful. By having internal knowledge a social engineer gains credibility.
#2 The Direct Attack: Just Asking for It
Many attacks by social engineers are complicated and require good planning of the individual steps. They rely on technical sophistication and extensive manipulation. It’s amazing, however, that sometimes it’s enough to just ask for the wanted information. In this case, the knowledge of the internal jargon is of great importance. Employees would never give away sensitive information. But of course, different rules apply to colleagues than to outsiders. Another very common tactic is to hide the key question among a lot of unimportant questions and statements.
#3 Building Trust: The Key to Deception
It happens that an employee doesn’t know the person who asks him or her for something. They work in different departments of the company or at least the other one claims that. But if the information provided is appropriate and the other person gives the impression that he or she’s the necessary knowledge by using the right internal jargon. The victim will expand the circle of trust and includes the person in it. Then the employee probably gives the social engineer what he or she’s asking for. By having internal knowledge an attacker gains credibility and this credibility leads to trust.
#4 “Let Me Help You”
Everyone is very grateful when he or she deals with a problem and then someone comes by with knowledge and skill to help and offer support. The social engineer takes advantage of this and knows exactly how he or she can solve the problems for others since the social engineer causes them. After solving the artificially generated problem the victim is very grateful and happy for the support. This can lead to a situation where the victim gives the attacker some critical information or do him or her a favor.
Another benefit is that an attacker who is called by the victim gains immediate credibility. Because the victim thinks that he or she’s calling someone who works in computer service, the victim would never ask the attacker to prove his or her identity.
To set up a situation in which the victim has to deal with a problem and asks the social engineer for help is called Reverse Social Engineering or the Reverse Sting. Another form of Reverse Social Engineering is when the victim recognizes the attack and uses psychological principles of manipulation to obtain as much information as possible from the attacker. With the help of this information, the company can try to protect themselves.
#5 “Can You Help Me?”
Another successful method of social engineering is to pretend that the attacker needs help. If somebody is in a jam, he or she’s the people’s sympathy. And this has proven to be an effective lever to achieve the social engineer’s goal. For example, an attacker introduces himself as an alleged colleague and the victim believes him or her. The diligence to help a colleague sometimes lubricates the cogs in the industry. But at the same time, this willingness to help could be a vulnerability and the social engineer would always take this chance and tries to exploit it.
#6 Phony Sites and Dangerous Attachments
People have a natural desire to get gifts for free. The smart attacker keeps that fact in mind while trying to break into the corporate network. Occasionally an offer appears in the mailbox that attracts the victim’s attention. No matter what the offer is about, the email will show how to download a file or click a link. And if the victim follows the instructions, the attacker wins.
The most damaging forms of malicious code – worms – have all relied on social engineering techniques to spread them, exploiting that everyone wants something for free. Especially when the email comes from a friend or business colleague, people tend to open the attachment without bad ulterior motives. The worm can multiply through innocent victims and appears to come from a trusted person.
Another type of internet fraud is that the attacker has set up a false login website, which looks very similar to the real website. The difference is that the wrong screen page does not give access to the computer system that the user wants to reach, but instead forwards his or her username and password to the hacker.
Another regularly recurring trick is to send an email with a tempting offer to visit a certain website, and the receiver can go there directly via a link in the email. Only that this link won’t take the receiver to the expected website, because the link in principle only pretends to connect to that website. The social engineer exploits the fact that people do not pay close attention to the exact link spelling or perceive a minimal deviation as a representation error. For example www.PayPai.com instead of www.PayPal.com. The fake website looks similar to the real website and the victims enter their usernames, passwords or credit card information carelessly.
#7 Using Sympathy, Guilt, and Intimidation
Skillful social engineers are very experienced in inventing impostures in which emotions such as fear, excitement or guilt are used to manipulate the victims. They use psychological triggers – automatic mechanisms that make others react immediately to concerns without a thorough analysis of all available information.
Everyone remembers the first day, especially when somebody is young and inexperienced. So when a newly hired person asks for help, he or she can assume that many people remember the feelings and help more than usual. A social engineer takes advantage of this and can use it to get the victim’s sympathies.
Furthermore, everyone wants to avoid difficult situations for themselves and others. Building on this positive impulse, the attacker can take advantage of a person’s sympathy, make the victim feel guilty, or use intimidation as a weapon.
A popular and highly effective form of intimidation relies on influencing human behavior through the use of authority. The name of the executive secretary alone can be of value. To mention the name of a person with a high(er) position is called name-dropping. It’s usually used to quickly establish a relationship with a victim because it assumes that the attacker is very close to an authority figure. The scam of intimidating someone by reference to authority works particularly well when the other person is in a fairly low position in the hierarchy of the company. Besides a victim is much more likely to do the social engineer a favor if he or she’s supposed to know a friend of the victim.
Are There Any Warning Signs for an Attack?
A warning sign could be if a caller refuses to provide a callback number or have unusual requests. Furthermore, if somebody tries to play out authority or has a request with particularly high urgency, special care should be taken. In such cases, intimidation shouldn’t be the reason for giving in. Maybe the attacker tries to increase the pressure with the threat of negative consequences in the event of non-cooperation. Often he or she reacts annoyed to inquiries. Also, the opposite could be used to manipulate the victim for example with compliments, flatteries or flirts. And last but not least, occasionally dropping known names.
What Can You Do to Protect Yourself and Your Company?
Kevin Mitnick has dedicated an entire chapter to the subject “Recommended Corporate Information Security Policies” in his book “The Art of Deception”. Here you can find some of his tips to reduce the chances of a social engineer. But the most important thing first, every company should adapt the policies to its demands and circumstances. There is no such thing as off-the-shelf safety.
- Never give anyone personal information or internal company information if the caller is unknown and the need for the request isn’t understandable.
- Each employee needs to be aware that when a caller knows internal company information like procedures or identifiers that isn’t enough to authenticate the requester or authorize him or her to get information.
- A fast way to verify the identity of a person on the phone is to call that person under the telephone number in the company’s phone directory. In the case that the call can’t be answered personally, there is the possibility to hear the voice of the colleague via voicemail and compare it to that of the attacker.
- The employees of a company usually have different roles and responsibilities, and each position has its weaknesses. There should be a basic training to be done by everyone. Furthermore, employees must also be trained according to their tasks. Persons who work with confidential information or occupy positions of trust should receive additional special training.
- Employees need to know about the strategies and methods of social engineering to carefully analyze the requests they receive. Role-playing can be a useful tool so that employees gain a better understanding of how a social engineer acts.
- Security personnel and system administrators also need to ensure for themselves that they follow the security rules, procedures, and practices. Sometimes they forget about it while they focus on everyone else sticking to it.
- A huge amount of scam emails have not well-formulated texts and when a company asks for private information about another company, everyone should become suspicious.
- Everyone should know the symbol looks like a tiny padlock. That symbol appears somewhere on the website. If it’s been certified as safe the hanger is closed, otherwise, the communication isn’t encrypted and the website should be closed immediately.
Conclusion
Your system is only as secure as the weakest link in your security chain. No matter how good your safety precautions are. You should never underestimate the human risk factor. Unfortunately, it isn’t possible to be fully covered. However, with a sufficient understanding of social engineering and security policies appropriate to your company, the probability of a successful attack can be reduced.
If you’re curious to hear more about the topic, then the book “The Art of Deception” is recommendable. Kevin Mitnick offers you many sample stories and conversations to deepen your understanding of the different techniques. He also offers a wide range of recommended security guidelines.
References
The blog entry content is based on the German version [7] of Kevin Mitnick’s book “The Art of Deception”. If not, the source is explicitly marked. All online references and images were last checked on August 31, 2019.
[1] https://www.phishprotection.com/heroes/kevin-mitnick/
[2] https://mitnicksecurity.com/about/kevin-mitnick-worlds-most-famous-hacker-biography
[3] https://en.wikipedia.org/wiki/Kevin_Mitnick
[4] https://www.mitnicksecurity.com/about/the-global-ghost-team
[5] https://mitnicksecurity.com/about/mitnick-example-clients
[6] Kevin D. Mitnick, William L. Simon, Steve Wozniak: The Art of Deception: Controlling the Human Element of Security. (Wiley 2002) p. 4
[7] Kevin D. Mitnick, William L. Simon: Die Kunst der Täuschung: Risikofaktor Mensch. (mitp 2011)
Image Sources
Post Image (at the top of the page) https://pbs.twimg.com/profile_images/746860382225076224/qMcxl_W7_400x400.jpg
[2] https://urgente.files.wordpress.com/2008/12/kevin_mitnick.gif
[3] https://www.denverpost.com/wp-content/uploads/2018/03/210139.jpg?w=910
Further Readings
Kevin D. Mitnick, William L. Simon: The Art of Intrusion: The Real Stories Behind the Exploits of Hackers, Intruders and Deceivers. (Indianapolis: Wiley Publishing Inc. 2005)
Kevin D. Mitnick, William L. Simon, Steve Wozniak: Ghost in the Wires: My Adventures as the World’s Most Wanted Hacker. (Little, Brown 2011)
Kevin D. Mitnick, Robert Vamosi, Mikko Hypponen: The Art of Invisibility: The World’s Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data. (Little, Brown 2017)

Leave a Reply
You must be logged in to post a comment.