Before quantum technologies, there was darkness – now, there is light. Small quantums with huge amounts of processing power. It seems like the future has arrived: Welcome to the second quantum revolution!
The interdisciplinary field of quantum computing surely is amongst the hot topics of scientific research at the moment. Initiatives rise, groups are formed, standards are built – a lot of money is being invested. But where does the idea of using quantums for computing come from? Why should computer scientists be interested? And what impact does it have on our understanding of Cybersecurity? Let’s find out.
The Second Quantum Revolution
Over 40 years ago, It was proposed by Richard Feynman in one of his famous talks in 1981 (‘Simulating physics with computers’) that quantum physics may be ‘the way’ to build a very powerful computer. This computer could be used to simulate quantum systems which are too hard to simulate with conventional computers. [1]
Why simulate quantum systems you ask? Because their properties are unique and can be used for specific problems.
Having this perspective on computing with quantum mechanics, Feynman is remembered for launching Quantum Computing as a field of study. Exploring the possibilities of quantum technologies in a wide range of applications is one of the biggest challenges of the 21st century. This is why the second quantum revolution seemingly has begun. [2]
Looking back, the first revolution in quantum physics enabled inventions like lasers and transistors, which are the basic building blocks of computers and all technology we are using today. [2]
The second quantum revolution is about controlling individual quantum systems, where in example charged molecules belong to. Using quantum logic, highly complex systems can be built and – with the power of engineering – used to serve applications. The combination of quantum physics and computing theory is thereby also known as quantum information. [2]
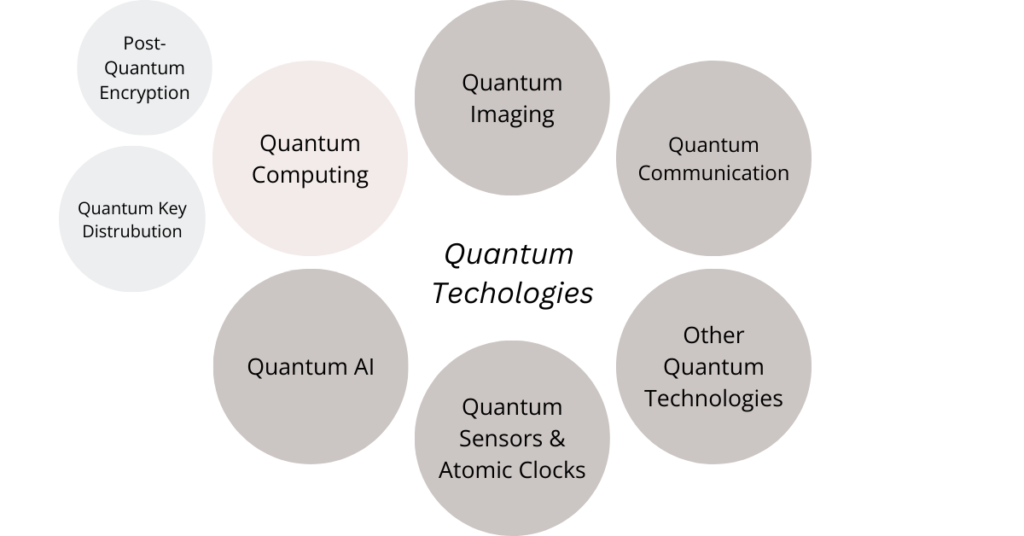
Quantum Technologies are more than just Quantum Computers. They have an influence on research in many fields from health to high-energy physics. But as they are indeed most interesting for Cybersecurity, let’s keep the focus on them. [3]
The Basic Rules of Quantum Systems
Without the understanding of some physics, you can’t wrap your head around quantum computers. Computer Scientists therefore need to learn physics as well for this technology. So let’s set the basics in order to understand what makes them so powerful.
As already described quantum systems have unique properties due to quantum mechanics. What seems like a mystery in behavior, nowadays can be described with the help of physics.
There are two main rules for quantum systems. [1]
- It can be in multiple states simultaneously.
- It only works, when you don’t look.
This is what makes quantum technologies super fascinating. As described in the particle-wave dualism or with Schrödingers cat, we can assume a system in multiple probable states. Therefore you can only derive results when looking at multiple results, because quantums have their own movements and behave differently each test. This works through statistical methods on a high scale. [3,4]
The highly statistical and therefore mathematical approach makes Quantum Computing drawn to the engineering field, physics and computer science. [3]
Alright. Small physics lesson done. Back to the computing aspect.
How does a Quantum Computer work?
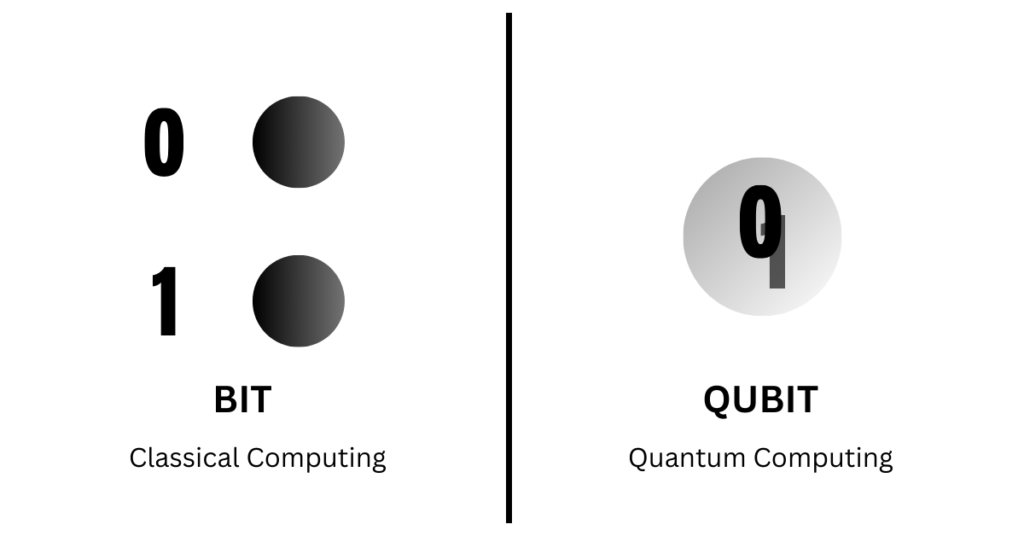
In classical computing, simple operations are made by addressing the block of bits. Having the state 0 or 1, the operations take place via simple electrical fields. The bits are joined together by logical gates such as AND, OR and NOT. [4,5]
Computing with quantums is different. The quantum computer works with quantum bits, the so-called qubits. Qubits can also have a value of either 0 or 1. So far so good, this is what we know already. But they can also represent both 0 and 1 at the same time. Why is that? [4,5]
Physics kicks in again with the main two principles of quantum mechanics:
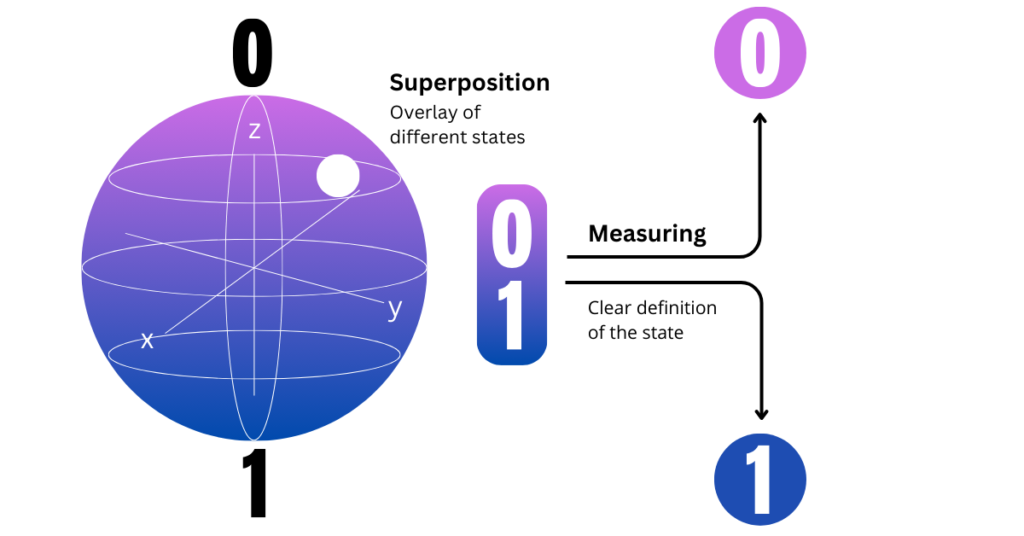
- Superposition: Famously introduced with the double-slit experiment, a particle such as an electron or photon can be in different states simultaneously. Known as ‘superposition’, this means that qubits can represent both 1 and 0 at the same time (i.e. 0, 1 and 10). Quantum computers use this characteristic by processing the states as possibilities of results, exploring multiple solutions to a problem simultaneously. This means that the software developer can take both cases (1 and 0) simultaneously, making a quantum computer faster than the classical one. [4,5]
- Entanglement: Quantums seem to be connected with some force, no matter how far apart they may be. Changing one state instantly affects the other. This principle known as ‘entanglement’ was proposed by Albert Einstein in 1945. It can be compared to a wire connection without any wires. If one quantum moves, the other one moves. This means that information can be encoded and manipulated in different ways, that would have been to unsolvable with classical bits. In reverse a new way of proramming is needed, presented in the form of a Hamiltonian. [5,6]
Adding qubits, the possibilities of computing power increases exponentially instead of linearly (i.e. N qubits = 2N bits). They can theoretically compute faster than any classical supercomputer already built (>100 qubits == supercomputer). Let’s talk numbers. The current record of qubits, in August 2023, is held by IBM with the quantum processor “Eagle” with 433 qubits. The aim for IBM currently is a quantum computer with 100,000 qubits. [7,8]
“Quantum computing is a rapidly-emerging technology that harnesses the laws of quantum mechanics to solve problems too complex for classical computers.”
– IBM [9]
The Perfect Environment
Handling the fine states of a qubit is a challenge. They are extremely sensitive to any form of disturbance such as light, heat or radiation inside the quantum computer. And the qubits as well interact with each other, making their manipulation extremely difficult. In order for the quantum system to work correctly, different measures need to be applied. [4,5]
Note: Different conditions apply to Photonic Quantum Computers. They are based on a photonic approach without the need of superconducting materials. They will not be discussed within this blog entry.
To be able to manipulate the qubits, they need to be trapped in a high-vacuum chamber at a temperature near absolute zero. Only this way, electrical and magnetical fields work at their best. And we need the quantums themselves to be trapped inside the chamber, with different laser beams to change the particles into qubits, setting them in superposition and entanglement state. Attention please: The more qubits, the more noise of atom entanglement! It’s not that easy. [4,5]

The stability of the qubits can only be achieved by ‘cooling down’ the atoms with physical and laser cooling. Physically cooling down magnets is extremely important for the characteristic of superconductivity. When cooled down, certain materials conduct electricity without energy loss (which basically means they are non-resistant). [4]
Laser Cooling is a concept of slowing down atoms to stabilize them. ‘Cooling’ refers to the process of slowing down a large amount of atoms, which will have an associated temperature that gets reduced. [10]
This is just a small insight in what it takes to built a quantum computer. You can imagine that there is a lot more precision and expertise needed.
State of Research
Just thinking about the electrical and material costs, internal and external factors that are invested in the construction of a quantum computer might lead to the fact that quantum computers are far away from being a personal computer. Billions of dollars are need for such a system. Huge computing power – but at what cost?
the need for superconducting materials. Therefore initiatives in collaboration between industry and research institutions arise for future innovations. Organizations like IBM, Google, Microsoft, and academic institutions are at the forefront of quantum computing research and often publish their latest breakthroughs. Small breakthroughs thereby accumulate and add to the ‘Second Revolution’ of Quantum Computing and its usage for real life applications. [6]
With this basic understanding of quantum computers, let’s have a look at what it means for the world of cybersecurity.
Being Quantum-Safe
With the release of massive computing power through quantum computers, conventional cryptography protecting our systems is in danger. The RSA-Cryptosystem, the Diffie-Hellman key exchange or the algorithm of Elliptic Curve Cryptography (ECC) will be broken, because the underlying security lays in the way that discrete algorithms such as linear factorization cannot be solved in polynomial time. Quantum Computers could easily solve that. [4,11]
Asymmetric cryptography, which we are using on a daily basis, is threatened by quantum computers. This is why they are a threat to convential cybersecurity. Maybe a diversification of our understanding of cybersecurity is needed. It definitely requires a change of encryption. [12]
“The quantum security market was valued at just under 500 million U.S. dollars in 2022, with forecasts suggesting that this is likely to rise to 9.8 billion U.S. dollars by 2030. The majority of quantum security revenue is generated by the post quantum security or cryptography (PQC) method”
– Statista [13]
Knowing about the power of quantum computers, Peter Shor proposed a quantum algorithm in 1994, which will break regular encryption. The challenge of developing quantum-safe encryption algorithms is currently faced by the new field of Post-Quantum Cryptography research. [8]
In the following blog article, you can find more information on Quantum and Post-Quantum Cryptography.
The Overall Impact on Cybersecurity
Looking at the overall cybersecurity and number of attacks, people are starting to worry. Being resistant to attacks that could be launched from quantum computers is a goal that need to be achieved in the near future. Or is it still rather distant in 10-20 years?
Breakthroughs like the number of 127 qubits developed by IBM are suggesting that it might happen faster than expected. IBM already claims to have developed quantum-safe algorithms. Quantum Computers aren’t strong enough to break current forms of encryption – yet. But the impact when they will just from the encryption perspective is profound. [8,14]
Technology is expensive, research is complicated. The private sector will probably not see the inner workings of a quantum computer for a while – let alone use it. But thinking about what can happened and what can be applied to hinder possible security breaches is needed. [14]
From “Safe” to “Quantum Safe”
As new challenges arise in maintaining the CIA principles (confidentiality, integrity, authentication), society must take action to get on a common ground of awareness. One of the ways of making sure that everyone is on the same page, are some guidelines and a suite of tools helping being resilient to quantum computers. [15]
“Planning and preparing is critical. A new suite of tools resilient to quantum computers must be standardized and deployed in order to maintain the availability and reliability of cyber systems and protect confidentiality and integrity.”
– ETSI, 9th ETSI/IQC Quantum Safe Cryptography Event [15]
ETSI is a European Standards Organization, which recognizes standards regarding telecommunications, broadcasting and other electronic communication networks and services. Having a global perspective, they have initiated a ‘Quantum Safe Event’ dedicated to plan an prepare for tools resilient to quantum computers and the transition into quantum computers when becoming more commercial. [15]
IBM and NIST (National Institute of Standards and Technology) work together on quantum-safe cryptography protocol standards for cybersecurity, that are just the start for new standards involving industry. The express the importance of setting standards in a long path of adoption. Because the entire software industry need to change their software inventory and quantum-safe solutions. The expertise of building quantum computers and the need for change in encryption is the perfect combination for development. [8]
The Impact
Let’s look at some positive and negative impacts of Quantum Computing regarding Cybersecurity in detail. [9,12,14]
Positive Impacts
- Stronger Encryption: Encryption methods such as RSA and ECC rely on the difficulty of factoring large numbers or solving other mathematical problems. With quantum computing the encryption could be performed much easier in less time, making systems harder to break. This is also a negative impact at the same time.
- Quantum Key Distribution (QKD): Enhancing security through new technologies built on the principles of quantum mechanics, QKD opens up a secure communication channel. The security is in the idea of the quantum state changing when the communication is being eavesdropped. This could alert the sender and receiver, making a break in security obvious.
- Optimization and Simulation: Quantum Computer could help solve complex optimization and simulation problems. These are relevant for various cybersecurity applications such as risk assessment, network security and threat modeling. Overall this could lead to improved defense strategies and more effective vulnerability assessments.
Negative Impacts
- Breaking Encryption: There is a high potential of breaking widely used encryption methods, making current cryptographic systems vulnerable. This leads to the compromise of sensitive data such as personal information (i.e. medical records), confidential communication (i.e. private messaging) and financial records. A new kind of cryptography therefore is needed.
- Cryptographic Vulnerabilities: Quantum computers may introduce new vulnerabilities. Cyber attackers with access to quantum computing power might exploit these vulnerabilities to breach systems in novel ways. Because these vulnerabilities are not known, no defense strategy or plan can be implemented.
- Threat to Blockchain: Many cryptocurrencies and blockchain technologies rely on cryptographics algorithms. Quantum computers could undermine the security of these systems, producing a need to develop new technologies.
Conclusion: What impact has Quantum Computing on Cybersecurity?
Bringing all input together, Quantum Computing can be summarized as ground-breaking for Cybersecurity. Quantum Technologies overall have a tremendous impact on the world in different disciplines from science to engineering.
To really know the impact, it is important to be acquainted with this new technology and the concepts that lay beyond it. Research and market values rise, as well as many companies start to understand the importance of Quantum Computing because of the possible breach of security. The impact therefore gains more weight and is not to be underestimated.
Important standards for Quantum-safe algorithms already have been formed, making the transition into a quantum-safe era existent. Preparation is being made, and the impact of the new technology is recognised. The implementation of new strategies and multiple layers of quantum-safe algorithms is needed.
However, the threat for Cybersecurity is dependent on having the Quantum Computing Power itself. Although research is on top of their plans on how to realize the next supercomputer, most probably quantum computers still need a few decades to be built small, reliable and affordable for everyone. In reverse this means that any cyber criminal most likely will not have access to new security methods for quite some time. The impact to be a current issue for applications and personal usages therefore is less high. Regarding big companies, this might be an issue for the next five years, as they could afford the power.
As a final statement, Quantum Computing has an impact on Cybersecurity. The question is: How long will it take to build affordable Quantum Computers opening up new kinds of security breaches for everyone – not just the big players, but the cyber criminals as well?
Outlook: The General Impact of Quantum Technologies
Quantum technologies not only play a role in computing, which this article has focused on. Other fields of usages are communication, imaging, AI and sensors in scientific and engineering fields like physics, chemistry, material science, biology, and information science. Especially medical research could vastly benefit from these technologies. Quantum sensors in example could detect new ways of brain functions. Quantum imaging could help in diagnostic procedures. And quantum computers themselves could help compute molecular chemistry. [3]
The major impact of quantum science on technology, culture and our understanding of the world has resulted in publicity. It is becoming increasingly important to gain awareness as part of the society for this meaningful concept. Therefore, currently a resolution is prepared for the 2023 General Conference of the United Nations Educational, Scientific and Cultural Organization (UNESCO) and the 2023 General Assembly of the United Nations (UN), to proclaim 2025 as the International Year of Quantum Science and Technology. The year-long initiative would celebrate the profound impacts of quantum science. It suits the year of 2025, because it is 100 years after the initial development of quantum mechanics. [16]
If you’re interested in learning more about Quantum Science and Technology, this is a list of useful resources where to get started.
- Series by Caltech University Experts on Quantum Science and Technology https://scienceexchange.caltech.edu/topics/quantum-science-explained
- Introduction to A New Quantum Revolution by NIST
https://www.nist.gov/physics/introduction-new-quantum-revolution - For trying out programming (first circuits) with Quantum Computers, IBM has officially launched a IBM Quantum channel, which can be accessed by the Qiskit package https://qiskit.org/ and https://quantum-computing.ibm.com/
Literature
[1] R. P. Feynman, “Simulating physics with computers,” International Journal of Theoretical Physics, vol. 21, no. 6–7, pp. 467–488, Jun. 1982, doi: https://doi.org/10.1007/bf02650179.
[2] Robin Materese, “Introduction: A New Quantum Revolution,” NIST, Mar. 21, 2018. https://www.nist.gov/physics/introduction-new-quantum-revolution (accessed Aug. 31, 2023).
[3] “Quantum technologies,” Fraunhofer-Gesellschaft, Apr. 01, 2019. https://www.fraunhofer.de/en/research/current-research/quantum-technologies.html (accessed Aug. 08, 2023).
[4] R. Jindal, “Future With Quantum Computers,” www.c-sharpcorner.com, 2023. https://www.c-sharpcorner.com/article/future-with-quantum-computers/ (accessed Aug. 31, 2023).
[5] J. Goldstein and C. Monroe, “Quantum Computers Could Change Everything (Podcast),” Spotify, Aug. 03, 2023. https://open.spotify.com/episode/2q7smFVzbH8QZtgIvzsPdg?si=FWxeIAusSvi54IRgPUVRng (accessed Aug. 08, 2023).
[6] IBM, “IBM Quantum Computing | IBM,” www.ibm.com, Oct. 01, 2015. https://www.ibm.com/quantum (accessed Aug. 08, 2023).
[7] M. Brooks, “IBM wants to build a 100,000-qubit quantum computer,” MIT Technology Review, May 25, 202AD. https://www.technologyreview.com/2023/05/25/1073606/ibm-wants-to-build-a-100000-qubit-quantum-computer/ (accessed Aug. 31, 2023).
[8] “NIST’s quantum-safe standards,” IBM Research Blog, Feb. 09, 2021. https://research.ibm.com/blog/nist-quantum-safe-protocols (accessed Aug. 08, 2023).
[9] IBM, “What is Quantum Computing? | IBM,” www.ibm.com, 2022. https://www.ibm.com/topics/quantum-computing (accessed Aug. 08, 2023).
[10] “Laser Cooling (Be+) | ALPHA Experiment,” alpha.web.cern.ch, Aug. 2020. https://alpha.web.cern.ch/science/laser-cooling-be (accessed Aug. 31, 2023).
[11] S. Dahmen-Lhuissier, “Quantum-Safe Cryptography (QSC),” ETSI, 2023. https://www.etsi.org/technologies/quantum-safe-cryptography (accessed Aug. 08, 2023).
[12] “Quantum computing and cybersecurity: How to capitalize on opportunities and sidestep risks,” IBM, Jul. 2018. https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/quantumsecurity (accessed Aug. 08, 2023).
[13] T. Alsop, “Quantum security market size 2021-2030,” Statista, Jun. 05, 2023. https://www.statista.com/statistics/1332857/quantum-security-market-revenue/ (accessed Aug. 10, 2023).
[14] “The Quantum Computing Impact on Cybersecurity,” QuantumXC, Jan. 24, 2020. https://quantumxc.com/blog/quantum-computing-impact-on-cybersecurity/ (accessed Aug. 08, 2023).
[15] S. Dahmen-Lhuissier, “9th ETSI/IQC Quantum Safe Cryptography Event,” ETSI, 2023. https://www.etsi.org/events/2117-2023-02-9th-etsi-iqc-quantum-safe-cryptography-workshop (accessed Aug. 08, 2023).
[16] “International Year of Quantum Science and Technology,” quantum2025.org, 2023. https://quantum2025.org/ (accessed Aug. 08, 2023).
[17] “IBM Q Dilution Refrigerator by Graham Carlow,” IBM Newsroom | Image Gallery, 2023. https://newsroom.ibm.com/media-quantum-innovation?keywords=quantum&l=100 (accessed Aug. 08, 2023).
[18] “Qubit vs bit. States of classical bit compare to quantum bit superposition, Vector concept Stock-Vektorgrafik,” Adobe Stock. https://stock.adobe.com/de/images/qubit-vs-bit-states-of-classical-bit-compare-to-quantum-bit-superposition-vector-concept/469735494 (accessed Aug. 31, 2023).
[19] P. Patel, “Qubit,” Devopedia, Jan. 05, 2022. https://devopedia.org/qubit (accessed Aug. 31, 2023).
Pictures
- Picture 1 | Quantum Technologies
- Picture 2 | Difference between Bit and Qubit, adapted by [18]
- Picture 3 | Multiple States of a Qubit, adapted by [19]
- Picture 4 | Liquid Helium Dewars for Physical Cooling, Picture by Nadine Weber
- Title Picture | First Quantum Computer in Europe by IBM [17]

Leave a Reply
You must be logged in to post a comment.