Tag: Vulnerabilities
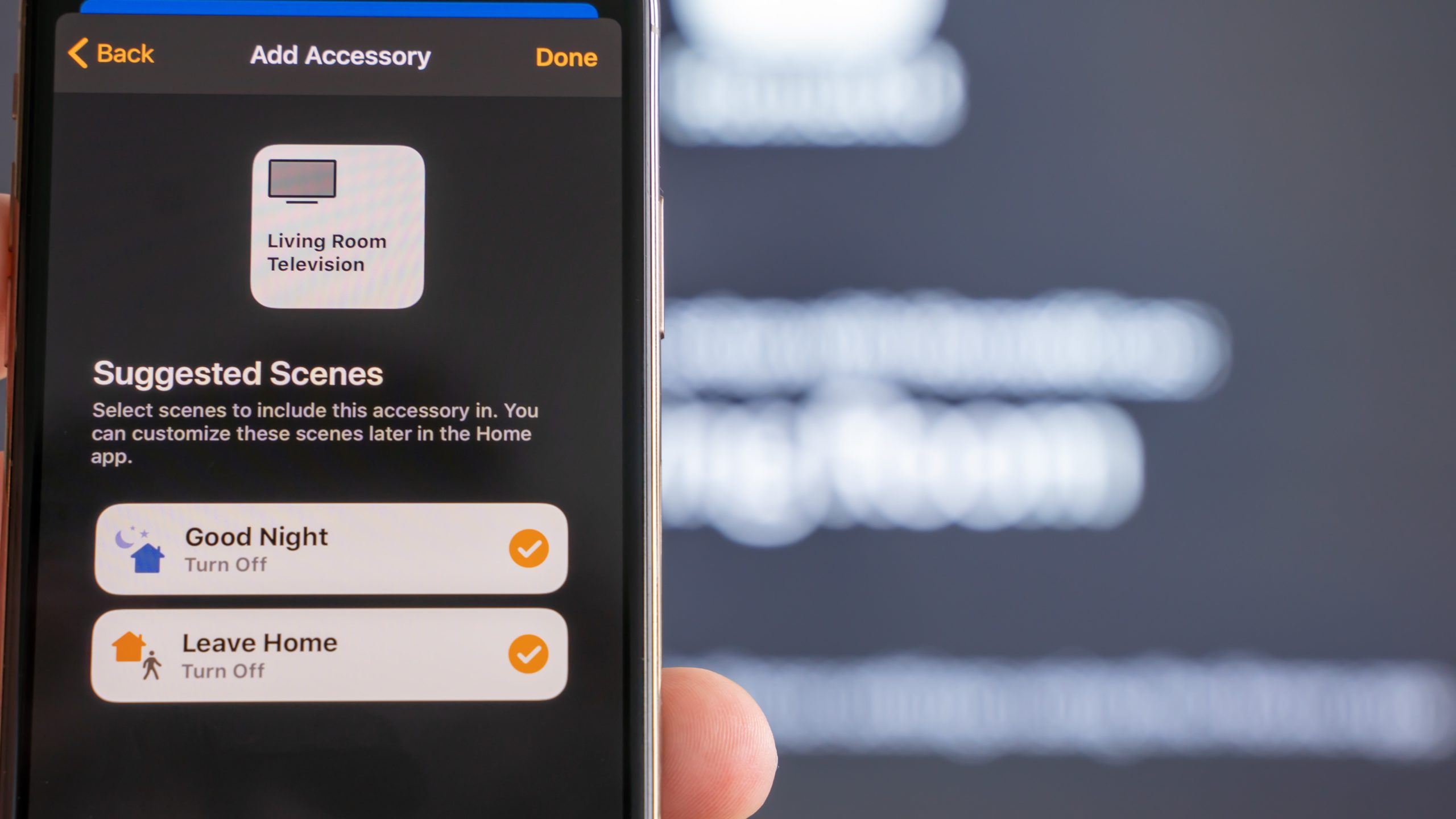
Why It’s So Easy to Hack Your Smart Home
Every day, new smart home accessories go online for the first time to join the Internet of Things. Many of them enjoy the unwarranted trust of their owners.
HAFNIUM EXCHANGE SERVER ATTACKS – What happened and how to protect yourself
an article by Carina Szkudlarek, Niklas Schildhauer and Jannik Smidt This post is going to review the zero day exploit of the Microsoft Exchange Servers starting in January 2021.It will look into the methods of SSRF and the exploitation of mistakes in the deserialization of input values to procure privileged code execution. INTRODUCTION In early…
Improved Vulnerability Detection using Deep Representation Learning
Today’s software is more vulnerable to cyber attacks than ever before. The number of recorded vulnerabilities has almost constantly increased since the early 90s. The advantage of Deep Learning algorithms is that they can learn vulnerability patterns on their own and achieve a much better vulnerability detection performance. In this Blog-Post, I will present a…
Cloud Security – Part 2: The vulnerabilities and threats of the cloud, current scientific work on cloud security, conclusion and outlook
The second of two blog posts about cloud security. This post covers the vulnerabilities and threats of the cloud, the current scientific work on cloud security and a conclusion and an outlook.
