Since the amount and value of data are constantly increasing more and more data of each individual is collected and processed. Moreover Facebook’s recent data leak with Cambridge Analytica shows that collected data cannot be absolutely securely treated and stored.
In 2014 and 2015, the Facebook platform allowed an app … that ended up harvesting 87m profiles of users around the world that was then used by Cambridge Analytica in the 2016 presidential campaign and in the referendum.
This is one of the reasons why we’ll take a look on our digital identity, how it can be linked to our real identity and how we can restrict that. An understanding of what data is collected while surfing on the web is a first step in preserving anonymity.
Anonymity has a lot of advantages and disadvantages and the discussion if it should be strengthened or not is roughly as old as the internet itself. We just concentrate on technical aspects here. But wait, what exactly does anonymity mean?
Definition
Anonymity is derived from the Greek word ἀνωνυμία, anonymia, meaning “without a name” or “namelessness”.
That’s more a historical point of view. Today we don’t need a name to identify an user on the internet, just think of the IP address. Thus a modern definition of anonymity is being unreachable. You can communicate, access or publish information and use services without revealing your identity.
Common identification methods
A very common method of identification on the internet is the user revealing his information on his own, such as registering on Facebook with the real name or purchasing clothes on Amazon.
There are several methods to track your usage behaviour, the websites you visit and the services you use, so that a clear picture of you can be created. These identification methods are split up into two categories: cross-domain tracking and cross-device tracking.
Cross-domain states tracking on one device, in one browser across different websites and applications, whereas cross-device tracking relates to multiple devices and applications.
Cross-domain tracking techniques include:
- Tracking cookies
- Virtual fingerprints
- DNS profile
- Browser profile
Tracking cookies are sent in a header field of the HTTP request and response, so that a server can recognise recurring users. These cookies are mostly not limited to one website, but shared across multiple domains through ad networks. Virtual fingerprints are individual characteristics, which distinguish one user of another, for example the combination of the browser type, operating system, installed fonts and plugins. On https://panopticlick.eff.org/ you can start a short test to see if your browser is unique and safe against cross-domain tracking.
Cross-device tracking techniques:
- User permission
- Device fingerprint
- IP address
- Eavesdrop
- Compromised system
- Ultrasonic cross-device tracking
As mentioned above obtaining the user’s permission is a great tool for cross-device tracking. If you’re logged into your Google account on several devices one can perfectly comprehend which services you used on which device. Another method, similar to cross-domain tracking with browser fingerprints are device fingerprints. These consist of your phone type, operating system, wifi and browser information and several other. If not using any proxy or VPN the IP address is also a good indicator. A user’s data traffic can be obtained through eavesdrop on the provider or proxy side and through compromised systems, consequently indicating user’s identity. Ultrasonic cross-device tracking is a method where a device emits a unique “ultrasonic audio beacon” that can be picked up by your device’s mobile application containing a receiver. It does not require any connections, but only access to the microphone.
With these techniques a lot of separate information can be collected, which often lead through connections to an user’s identity.
Defending your anonymity
Defending your anonymity is not an easy task to achieve, because it is not a discrete condition but a spectrum. This section is targeting users with a normal internet behaviour and should give a first insight on the tools and methods for preserving anonymity.
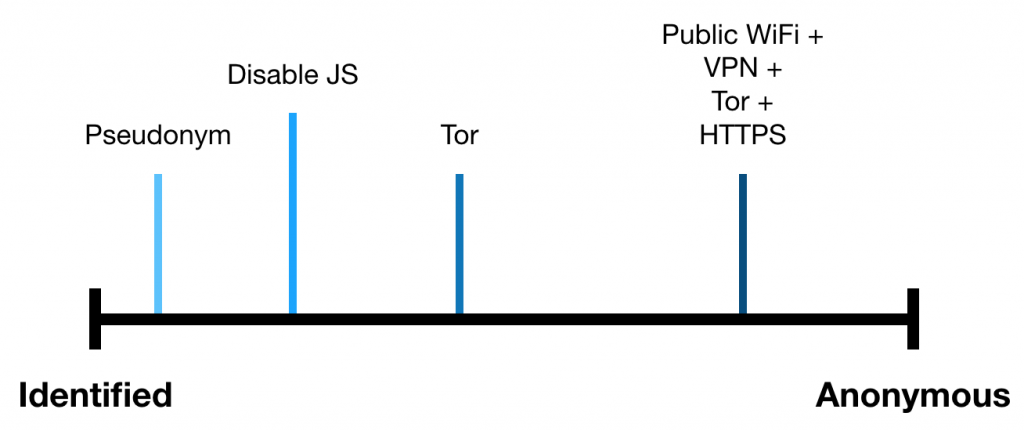
An unwritten law on the internet is using pseudonyms instead of real names in online forums and games, so you don’t give out your identity to everyone. Exceptions are social networks like Facebook, where the real identity is a central part of the application.
To come back to the two mentioned categories, cross-domain tracking and cross-device tracking, there are tools and techniques to prevent this kind of tracking.
Tracking-Cookies can be either marked as not preferred through the Do Not Track Value (DNT) or completely disabled in most browser’s settings. The user experience on websites can suffer from disabled tracking cookies, as the individualization of websites relies on these cookies.
Virtual fingerprints can be reduced through the usage of a common, less individualized browser, e.g. Safari on an iPhone. Disabling JavaScript prevents obtaining installed fonts and plugins, but at the expense of usability. The Tor browser includes a feature for reducing the browser fingerprint and is immune against most of the conventional browser fingerprinting techniques.
Prevention of cross-device tracking techniques includes:
- Anonymizer
- Anonymous remailers (Mixmaster) and filesharing (Freenet)
- Friend-to-friend networks (Ripple)
With an Anonymizer the real IP address can be hidden through a connection to a broker, which forwards the requests and responses. There are different architectural types, including proxy, VPN and onion routing. Anonymous remailers and filesharing tools are based on the peer-to-peer (P2P) principle, where systems are connected with each other without the need of a central instance. Friend-to-friend networks are working similar, but the peers are solely familiar people.
User permissions are critical for preserving anonymity and should be chosen wisely, so that unnecessary information and rights are not provisioned. As described above, there are several ways to protect your digital identity, but mostly at the expense of usability.
Further research
There are several unaddressed topics which are gaining relevance in the future and thus require further research:
- How to provide positive aspects of anonymity without strengthening cyber crime?
- How would the internet change if every user would need a clear identification for access?
- How does the uprising connectivity of all kinds of objects (IoT) influences anonymity?
References
[ 1 ] – https://www.theguardian.com/technology/2018/jul/11/facebook-fined-for-data-breaches-in-cambridge-analytica-scandal
[ 2 ] – https://www.dictionary.com/browse/anonymous
[ 3 ] – https://thehackernews.com/2017/05/ultrasonic-tracking-signals-apps.html
[ 4 ] – https://www.eff.org/issues/do-not-track

Leave a Reply
You must be logged in to post a comment.