More than forty years ago Richard Feynman’s paper “Simulating Physics with Computers” was published [1], laying the foundational vision for what we now recognize as quantum computing. Since then, quantum computing has become a fascinating and fast-expanding field at the forefront of technological innovation. With the potential to revolutionize computing power and solve complicated issues that traditional computers cannot currently answer, quantum computing has captured the interest of researchers, scientists, and industry leaders.
The leap in computational power besides many new opportunities brings with it the potential to break current encryption methods, threatening the confidentiality and integrity of sensitive data. As a consequence, the need for quantum-safe encryption – cryptographic methods designed to withstand the capabilities of quantum algorithms – has become a pressing matter for enterprises globally.
This article explores the importance and impact of quantum-safe encryption for enterprises focusing on the main considerations that businesses must make to future-proof their security infrastructures. As a basis for this discussion, the key properties of quantum computing are introduced and a summary of the effects of quantum computing on digital security is given.
1. Understanding quantum computing through comparison to classical computing
Quantum computing is an interdisciplinary field combining aspects of quantum mechanics, quantum information theory and computer science.
A quantum computer is defined as a device that leverages the specific properties described by quantum mechanics to perform computation [2, p. 3]. Unlike classical computers, which also function under the principles of quantum mechanics, quantum computers utilize the unique quantum states and phenomena to perform computations more efficiently. This enables them to solve complex problems for which classical systems lack capability. Such properties of quantum states are superposition, entanglement and interference.
1.1 Qubits and superposition
According to Nielsen and Chuang [3, p. 13], a quantum bit (qubit), similarly to a classical bit, possesses a state, which can be either 0 or 1. Those two states represented as |0⟩ and |1⟩ in quantum computing are known as computational basis states. However, before measurement a qubit can also exist in linear combinations of multiple states, known as superposition:
|ψ⟩=α|0⟩+ β|1⟩
The „| ⟩ “ notations are called Dirac notation. The coefficients α and β are complex numbers, but for practical purposes, they can be thought of as real numbers. When a qubit gets measured, the result we get is either 0 with probability |α|2 or 1 with probability |β|2.
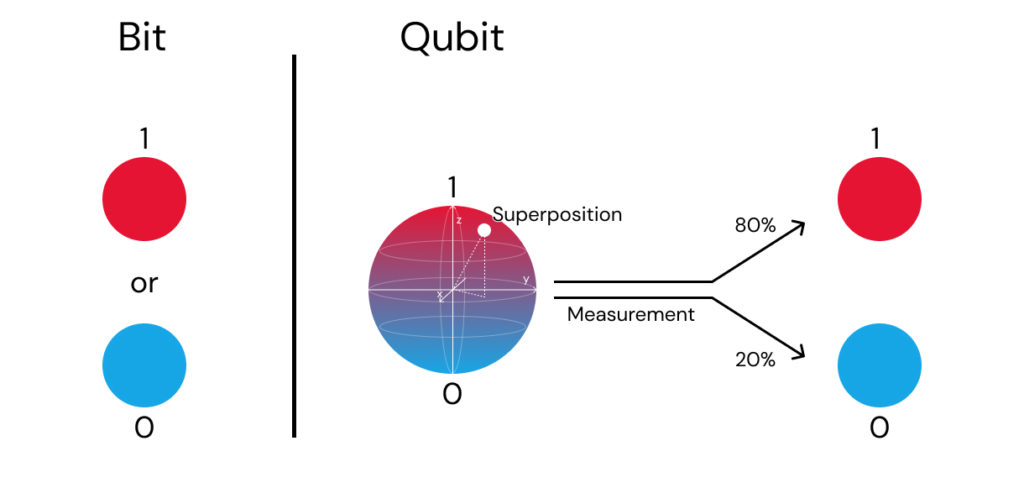
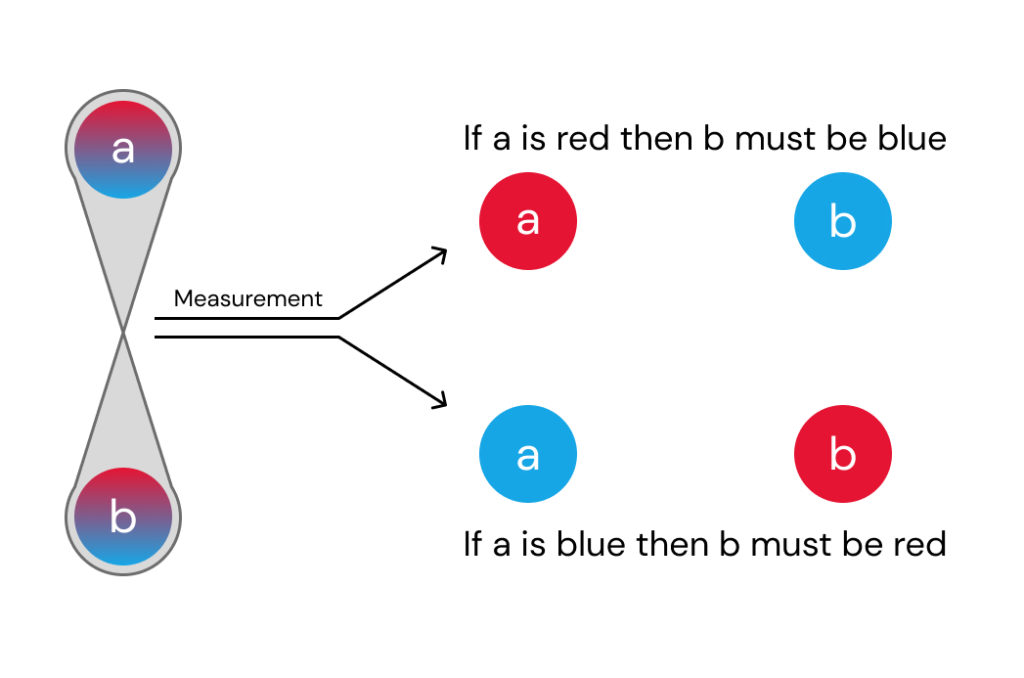
1.2 Entanglement
A particular form of quantum superposition where two systems exhibit a correlation in their measurement outcomes that surpasses what can be achieved by classical correlations is called entanglement [2, p. 8]. In this special case the states of the two systems become inseparable, and the measurement of one system directly affects the state of the other.
1.3 Interference
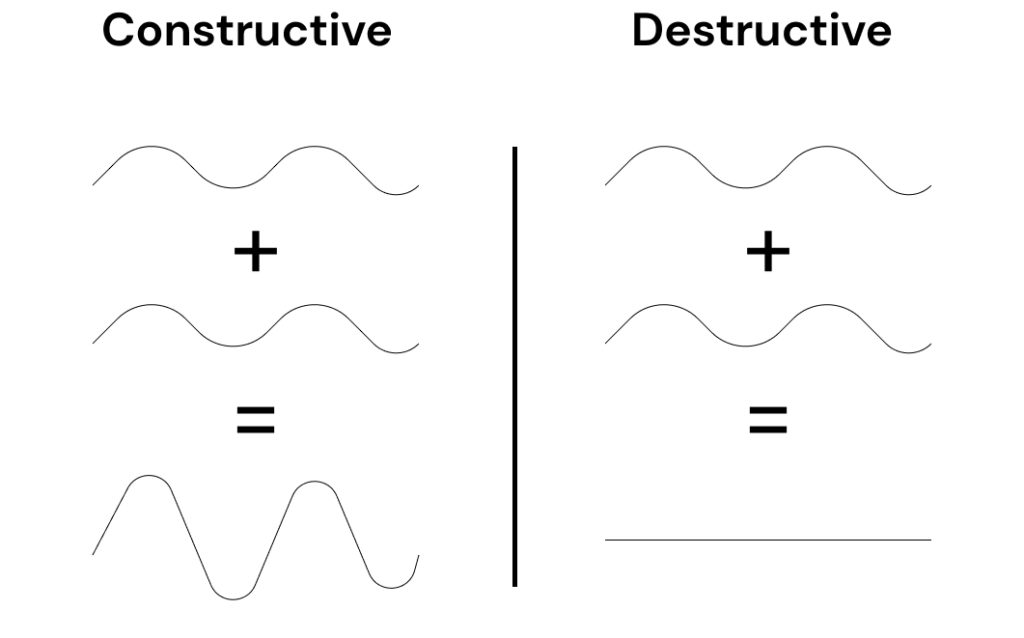
Interference is a unique quantum phenomenon arising from the wave-like nature of quantum states, where each state has a complex coefficient or amplitude. It allows for the manipulation of probabilities to enhance the likelihood of desired outcomes and suppress unwanted ones. The term refers to the phenomenon where the probabilities of different outcomes can increase or decrease due to the relative phases of the quantum states involved.
When we have a superposition of quantum states, the relative phases (or angles) between these states determine whether the amplitudes add up constructively or destructively:
- Constructive interference occurs when the relative phases of the states cause their amplitudes to reinforce each other, leading to a higher probability of a certain outcome.
- Destructive interference happens when the relative phases cause the amplitudes to cancel each other out, leading to a lower probability of a certain outcome. [2, pp. 26-27].
By harnessing the collective properties of quantum states, quantum systems can process and manipulate vast amounts of information simultaneously. For example, in classical computing the number of possible states grows linearly with the number of bits, while in quantum computing, the principle of superposition allows the number of states to grow exponentially with the number of qubits. This exponential growth means that the number of possible states that can be investigated at the same time increases dramatically, providing a remarkable advantage over classical computing in domains such as cryptography.
2. Implications of quantum computing for digital security
The introduction of quantum computing has created both new possibilities and challenges for digital security. Many of the widely-used cryptography mechanisms today rely on the assumption that certain mathematical problems are computationally hard to solve. That assumption was made with only classical computers in mind. The introduction of quantum computers fundamentally challenged our understanding of digital security, creating both new possibilities and difficulties for the field.
2.1 Shor’s algorithm
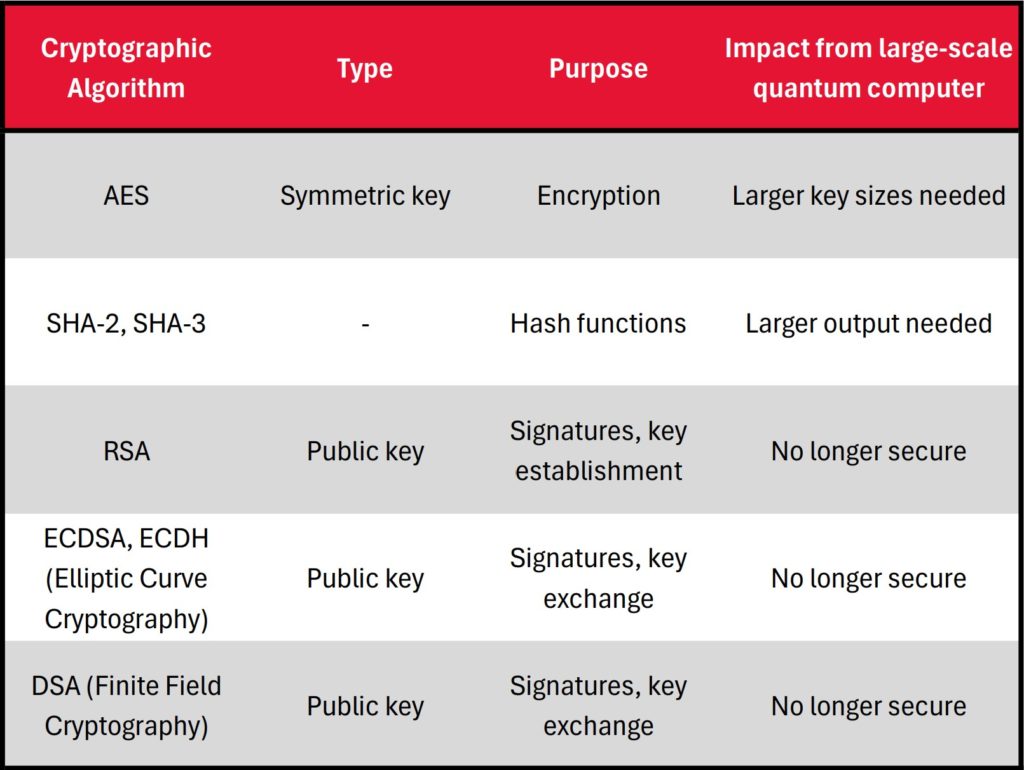
In 1994 Peter Shor introduced an algorithm for factoring large numbers and finding discrete logarithms on a quantum computer [7]. The ability to solve those two difficult classical computers problems renders widely used in public-key cryptography algorithms obsolete. That means that attackers could potentially forge digital signatures, compromise encrypted data, and intercept communications.
2.2 Grover’s algorithm
In 1996 Lov Grover introduced an algorithm that offers a quadratic speedup on unstructured search problems [8]. That discovery poses a potential threat to symmetric cryptographic algorithms and hash functions by significantly reducing the time complexity of brute-force search attacks. While the National Institute of Standards and Technology (NIST) finds it unclear, whether Grover’s algorithm will ever be practically relevant, they still recommend doubling of key sizes for symmetric key systems to preserve security [9].
2.3 Quantum-safe encryption
To address the challenge to cryptography that quantum computing poses, quantum-safe encryption algorithms, also known as post-quantum cryptography (PQC) algorithms are being developed. Those algorithms are resistant to attacks both from classical and quantum computers. PQC includes not only quantum algorithms, that is algorithms that use the principles of quantum mechanics, such as the transmission protocols BB84 for Quantum Key Distribution [10], but also classical encryption algorithms that are believed to be quantum safe. Examples of the latter are the lattice-based CRYSTALS-Dilithium digital signature algorithm and the code-based Classic McEliece public-key encryption algorithm. The German Federal Office for Information Security (BSI) recommends also hybrid solutions where the classical cryptographic algorithms are being enhanced by quantum cryptography (for more information see [11]).
3. The Road to a Useful Error-Corrected Quantum Computer
3.1 The NISQ era
In his article “Quantum Computing in the NISQ era and beyond” [12] John Preskill states, that the core of what makes advancements in quantum computing so hard is that it is impossible to observe a quantum system without causing an uncontrollable disturbance in it. He also introduces a name for the era of quantum advancement we are entering – Noisy Intermediate-Scale Quantum (NISQ):
Here “intermediate scale” refers to the size of quantum computers which will be available in the next few years, with a number of qubits ranging from 50 to a few hundred. 50 qubits is a significant milestone, because that’s beyond what can be simulated by brute force using the most powerful existing digital supercomputers. “Noisy” emphasizes that we’ll have imperfect control over those qubits; the noise will place serious limitations on what quantum devices can achieve in the near term.
John Preskill [12]
3.2 A two-dimensional horse race
Hidary [2, pp. 65-66] compares the NISQ era to the early stages of classical computing in the 1940s and 1950s and explains that to achieve a fully error-corrected quantum computer, it is necessary to reach a scale of more than 106 qubits. This perspective aligns with John Martinis’ analogy from his presentation at the HPC User Forum [13], where he describes quantum computing as a “two-dimensional horse race”. Martinis emphasizes that progress in the field should be measured with having both quantity (number of qubits) and quality (limiting error rate) in mind.
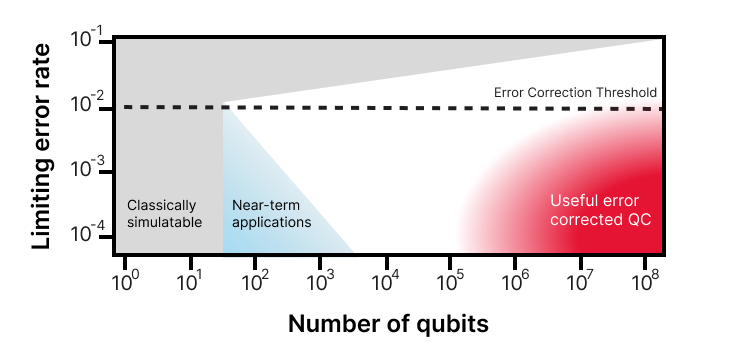
To better understand how far we are currently on the way to a useful error corrected QC, we can compare the roadmaps of some of the leading companies in the field of quantum computing – IBM and Google:
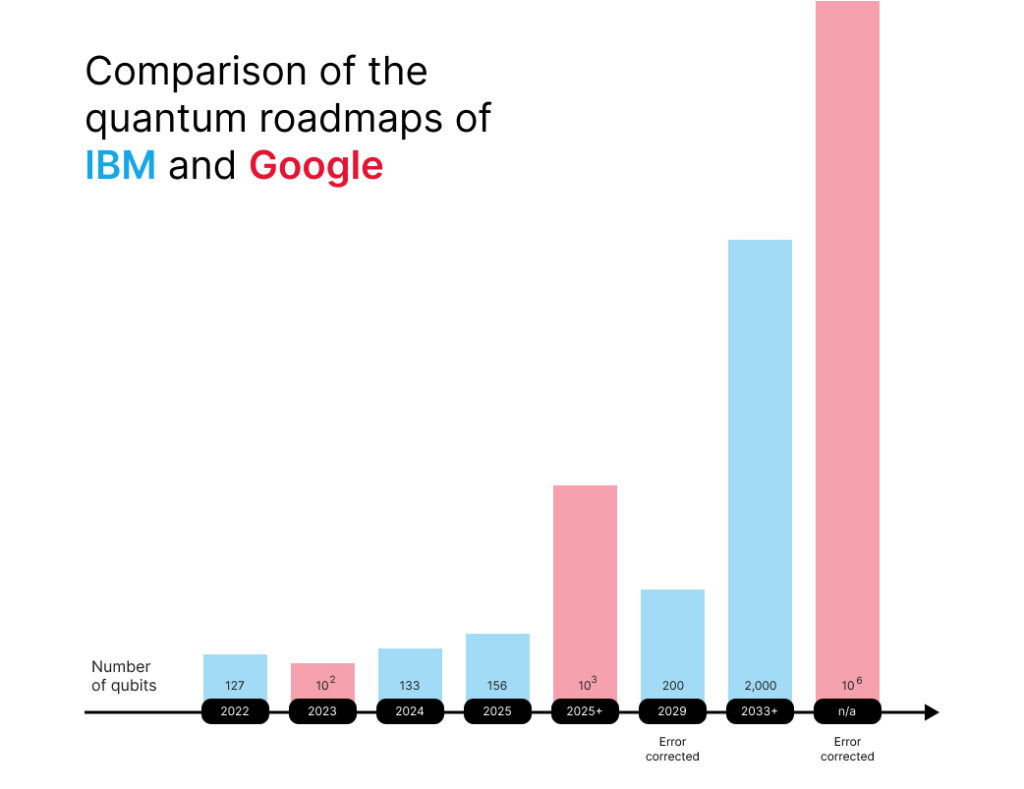
4. Importance of Quantum Safe Encryption for Enterprises
Although looking at the roadmaps of quantum leaders it might be easy to speculate that a quantum computer will not be able to reach 106 qubits any time soon, there are multitude of reasons for enterprises to invest in their quantum readiness today.
4.1 Security risks
Since the security risks that quantum computing poses seem to be a problem for the distant future, people might naturally want to delay taking action in order to focus on other urgent matters. What should be considered though, is whether or not we will be ready for an era with quantum computers. Based on Michele Mosca proposal [16], the answer seems to be highly personalized for each business case:
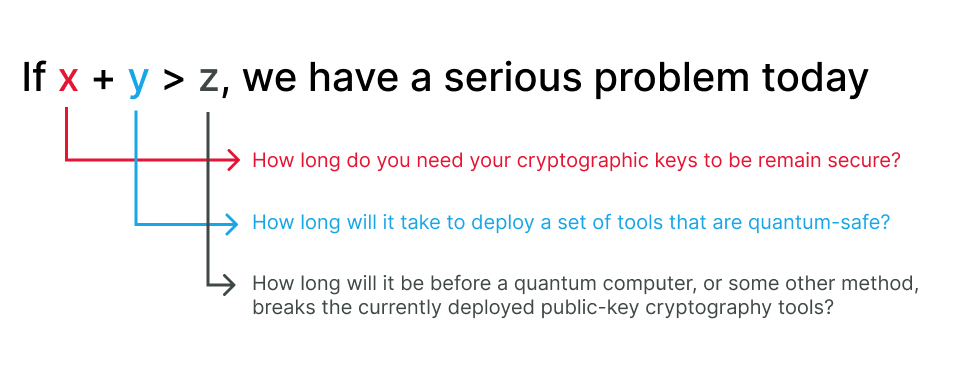
To better illustrate this, we can use health information as an example. For personal health information, we typically need long-term security, possibly up to 100 years, to ensure patient confidentiality over an extended period (x=100). Migrating to quantum-safe cryptographic tools in a healthcare system might take a considerable amount of time due to the complexity and regulatory requirements involved. Let’s assume this migration time is around 20 years (y=20). The collapse time (z) is the estimated period before a quantum computer or another method can break the currently deployed public-key cryptography tools.
That means that in order to guarantee the protection of personal health information against quantum attacks, governments have to be sure that a quantum computer will not be able to break the deployed public-key cryptography tools in the next 120 years. Given the rapid advancements in quantum computing, risking inaction and being wrong in this specific case is something we cannot afford. The consequences of compromised health information could be severe, leading to breaches of patient confidentiality, identity theft, and other security threats.
4.2 Future-Proofing Security
As discussed in section 2, with the advancement of quantum computing traditional cryptographic methods like RSA and ECC will become vulnerable to quantum attacks. Sensitive data with long-term confidentiality needs, such as financial records, personal data, and intellectual property, must be protected against future quantum decryption capabilities already today. That is due to the “Harvest now, decrypt later” strategy used by cyber criminals, where they intercept and store encrypted data with the intention of decrypting it later when quantum computers that are capable of breaking current encryption methods become available to them. In order to protect their valuable information against such future threats, companies need to start implementing quantum-safe encryption now.
4.3 Compliance
Organizations around the world are already developing and promoting cryptographic standards and best practices. For example, since 2016, the National Institute of Standards and Technology (NIST) in the United States has been conducting a competition to identify and standardize quantum-resistant cryptographic algorithms (for more information see [17]), while in 2022 the Federal Office for Information Security (BSI) in Germany released guidelines for migrating to quantum-safe cryptography (for more information see [11]).
Although these guidelines and standards are not legally binding on their own, they frequently influence regulatory frameworks and are incorporated into legal requirements and policies. For example, In May 2022 the White House issued a National Security Memorandum [18], according to which the release of quantum-resistant cryptographic algorithm standards by NIST will play a crucial part in the roadmap for transition to quantum-resistant systems of the country. Quantum-safe encryption will be required for both the public and private sector. That means that staying informed about and adopting new quantum-safe encryption standards helps enterprises ensure their cryptographic practices are robust and compliant with future regulations.
4.4 Maintaining Trust
For industries like IT, where customer confidence directly correlates with business success, maintaining trust is key. When organizations put efforts into adhering to guidelines and standards for quantum-safe encryption, they exhibit a commitment to staying ahead of cybersecurity challenges. By regularly updating their practices in response to evolving research, businesses uphold their position as trustworthy entities. That in turn leads to an increase in customer loyalty and a boost of the business’s reputation in the market.
4.5 Competitive Advantage
Early adoption of quantum-safe encryption helps organizations position themselves as leaders in cybersecurity and sets them apart from competitors. For instance, Zoom’s rollout of post-quantum end-to-end encryption (E2EE) [19] demonstrates a commitment to robust security practices and increases confidence among stakeholders, including customers and partners.
Furthermore, investing in cutting-edge security technologies, like post-quantum cryptography, positions enterprises as pioneers of innovation. That way organizations can attract strategic business partnerships and investments, strengthening their market position and fostering growth opportunities. The collaborative efforts of IBM and industry leaders in telecommunications [20] illustrate their collective commitment towards quantum-safe networks and further emphasize their position as industry leaders.
5. Impact of Quantum Safe Encryption for Enterprises
As we already established, quantum safe encryption enhances data security for enterprises by strengthening the resilience against both classical and quantum threats. Beyond this improvement of security, implementing quantum safe encryption will also have additional impacts on businesses.
5.1 Crypto-agility
As the Post-Quantum Cryptography (PQC) competition announced by NIST is nearing its end, enterprises are in a difficult situation. They must choose between new, unproven encryption algorithms and old, reliable ones that might become obsolete soon. Many of the risks, that the new algorithms bring, might still be unknown, as shown by one finalist of the competition being easily broken with regular computers in 2022 (for more information see [21]). That means that early adopters must be prepared to change or undo updates if needed.
This uncertainty makes crypto-agility a necessity. Crypto-agility is a strategy to be flexible and quickly update protocols, keys, and algorithms. It involves using tools and technologies that can easily switch between cryptographic technologies, ensuring that systems built today can accommodate future changes. Companies must focus on crypto-agility to protect their systems and ensure they can continue to operate without interruption as cryptographic standards evolve and new threats like quantum computing appear.
5.2 Technical and Operational Changes
Some already existing systems might not have been created with crypto-agility in mind. In such cases, implementing quantum-safe encryption might require overcoming common challenges such as outdated algorithms and dependency on long-life data secured by obsolete schemes. Those challenges can make updating cryptographic systems difficult and may require custom solutions. That is why enterprises need a well-planned migration strategy to transition smoothly from classical to quantum safe encryption without disrupting operations.
Another major challenge is that many organizations lack awareness of their cryptographic assets. For instance, 58% of enterprises do not know the number of keys and certificates they use [22, p. 12]. The lack of centralized crypto-management strategies in many organizations also makes it difficult to track, manage, and secure cryptographic keys and certificates. This highlights a pressing need for companies to take comprehensive inventories of their cryptographic keys and to streamline current cryptographic infrastructures. Automation in assessing and evaluating cryptographic systems can aid in prioritizing and executing targeted migrations.
5.3 Financial Implications
Transitioning to quantum-safe encryption entails significant initial financial investment for new technology, staff training, and possibly hiring specialized personnel. However, this investment can lead to long-term savings by preventing costly data breaches and avoiding regulatory fines. Despite those benefits, only 30% of organizations are currently budgeting for post-quantum cryptography (PQC) readiness, and 51% cite a lack of resources as the primary barrier to implementation [22, p. 7].
The lack of budget is closely connected with the lack of awareness in leadership about the significant challenges quantum computing poses to current encryption methods. In their 2023 quantum readiness report Ponemon Institute stated, that nearly half of respondents to their surveys (49%) indicate that their leaders are only somewhat aware or not aware of the security implications of quantum computing [22, p. 3]. That means that there is a further need for teams to highlight the risks and potential financial impacts of quantum threats, demonstrating the urgent need for proactive investment in quantum-safe encryption to protect the enterprise’s future.
6. Conclusion
Driven by its foundational principles of qubits, superposition, and entanglement, quantum computing represents a revolutionary change in technology with profound implications for digital security. The capabilities of algorithms like Shor’s and Grover’s highlight the challenges quantum computing will bring and emphasize the urgency of transitioning to quantum-safe encryption methods.
Even though quantum computing is still in its early stages, it is important for enterprises to already start preparing for the challenges this technology will present. This proactive approach will help future-proof their security infrastructures, ensure compliance, maintain trust, and secure a competitive advantage. The transition to quantum-safe encryption will require organizations to ensure crypto-agility, to address technical and operational challenges, and to understand the importance and the financial implications of the transition itself.
Leadership awareness and investment in quantum-safe strategies will be crucial in protecting enterprise data against the looming threat that quantum poses. Moreover, these measures will enable businesses to capitalize on the future benefits of quantum technology without compromising security. Ultimately, proactive investment in quantum-safe encryption will empower organizations to secure their data today and thrive in the quantum-driven future.
References
[1] R. Feynman, “Simulating physics with computers,” International Journal of Theoretical Physics, no. 21, p. pages467–488, 1982.
[2] J. D. Hidary, Quantum Computing: An Applied Approach, 2nd ed., Palo Alto, CA, USA: Springer Cham, 2021.
[3] M. A. a. C. I. L. Nielsen, Quantum Computation and Quantum Information: 10th Anniversary Edition, 10th ed., Cambridge University Press, 2010.
[4] S. Golestan, M. Habibi, S. Mousazadeh Mousavi, J. Guerrero and J. Vasquez, “Quantum computation in power systems: An overview of recent advances,” Energy Reports, vol. 9, no. 2352-4847, pp. 584-596, 2023.
[5] “Quantum Entanglement,” The Quantum Atlas, [Online]. Available: https://quantumatlas.umd.edu/entry/entanglement/. [Accessed 23 July 2024].
[6] A. Giani and Z. Eldredge, “Quantum Computing Opportunities in Renewable Energy,” SN Computer Science, vol. 2, no. 5, 2021.
[7] P. Shor, “Algorithms for quantum computation: discrete logarithms and factoring,” in Proceedings 35th Annual Symposium on Foundations of Computer Science, IEEE, 1994, pp. 124-134.
[8] L. K. Grover, “A fast quantum mechanical algorithm for database search,” in Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, Pennsylvania: Association for Computing Machinery, 1996, p. 212–219.
[9] L. Chen, S. Jordan, Y.-K. Liu, D. Moody, R. Peralta, R. Perlner and D. Smith-Tone, “Report on Post-Quantum Cryptography,” National Institute of Standards and Technology , 2016.
[10] R. Ciesla, Encryption for Organizations and Individuals: Basics of Contemporary and Quantum Cryptography, Apress Berkeley, 2020.
[11] F. O. f. I. S. (BSI), “Quantum-safe cryptography – fundamentals, current developments and recommendations,” Federal Office for Information Security (BSI), Bonn, 2022.
[12] J. Preskill, “Quantum Computing in the NISQ era and beyond,” Quantum, vol. 2, p. 79, 2018.
[13] J. Martinis, “Quantum Computing and Quantum Supremacy,” 22 April 2018. [Online]. Available: https://www.youtube.com/watch?v=nycwc-wXuuw&ab_channel=InsideHPCReport. [Accessed 19 July 2024].
[14] “Quantum technology,” IBM, [Online]. Available: https://www.ibm.com/quantum/technology. [Accessed 26 July 2024].
[15] “Explore,” Google, [Online]. Available: https://quantumai.google/. [Accessed 26 July 2024].
[16] M. Mosca, “Cybersecurity in an Era with Quantum Computers: Will We Be Ready?,” IEEE Security & Privacy, vol. 16, no. 5, pp. 38-41, 2018.
[17] “Post-Quantum Cryptography,” National Institute of Standards and Technology, [Online]. Available: https://csrc.nist.gov/projects/post-quantum-cryptography. [Accessed 19 July 2024].
[18] J. R. Biden, “National Security Memorandum on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems,” 2 May 2022. [Online]. Available: https://www.whitehouse.gov/briefing-room/statements-releases/2022/05/04/national-security-memorandum-on-promoting-united-states-leadership-in-quantum-computing-while-mitigating-risks-to-vulnerable-cryptographic-systems/. [Accessed 19 July 2024].
[19] “Zoom bolsters security offering with the inclusion of post-quantum end-to-end encryption in Zoom Workplace,” Zoom, 21 May 2024. [Online]. Available: https://news.zoom.us/post-quantum-e2ee/. [Accessed 19 July 2024].
[20] R. Harishankar, “How IBM is helping make the world’s networks quantum safe,” IBM, 29 September 2022. [Online]. Available: https://research.ibm.com/blog/quantum-safe-crypto-for-telco. [Accessed 19 July 2024].
[21] C. Q. Choi, ““Quantum-Safe” Crypto Hacked by 10-Year-Old PC,” IEEE Spectrum, 19 August 2022. [Online]. Available: https://spectrum.ieee.org/quantum-safe-encryption-hacked. [Accessed 20 July 2024].
[22] Ponemon Institute LLC, “Preparing for a Safe Post Quantum,” 2023.
Images
Image 1 – Bit vs. Qubit. Adapted from [4]
Image 2 – Entanglement. Adapted from [5]
Image 3 – Constructive vs. destructive interference. Adapted from [6]
Image 4 – Quantum computing as a “two-dimensional horse race”. Adapted from [13].
Image 5 – Comparison of the quantum roadmaps of IBM and Google. Adapted from [14] and [15]
Image 6 – Measuring the possibility to delay quantum action. Adapted from [16]
Tables
Table 1 – Impact of Quantum Computing on Common Cryptographic Algorithms. Adapted from [9]

Leave a Reply
You must be logged in to post a comment.