To run a successful business in the IT market, you have to have some sort of Cybersecurity. To forgo security does not only hurt the reputation immensely once a data breach happens, a data breach is also very costly. According to Forbes[^1] and IBM[^2] the average cost of a data breach in 2024 was around $4.88 Million, which is a 10% increase from 2023. In addition, it took companies an average time of 204 days to identify a breach and an additional 73 days to close it[^3]. With these numbers in mind, you want to have a strong cybersecurity protecting your organization from potential data breaches.
1 Cybersecurity Frameworks
Frameworks are the theoretical foundations of IT security and there exist quite a few different cybersecurity Frameworks. One of them is called “Pyramid of pain” and it shows the levels of difficulty for attackers to change different parts of their attack.
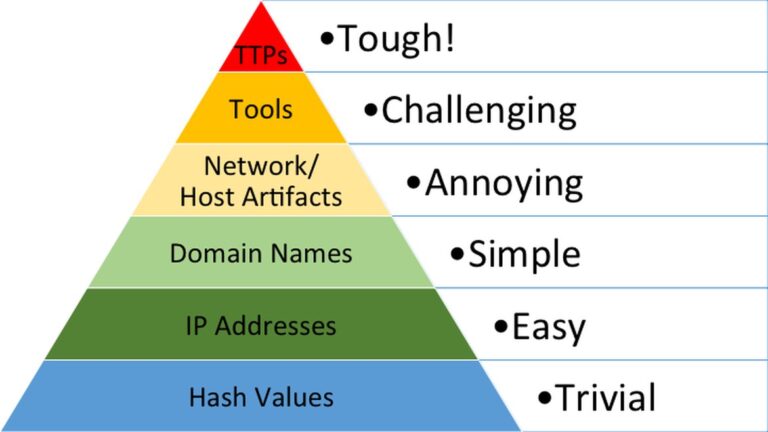
The pyramid shows that:
- Changing the hash value of malware is trivial because it just needs to be recompiled.
- Switching IP addresses of the command and control server is easy because they can use dynamic IPs, proxies or VPNs to change them.
- Changing the malicious domain is simple because they can register a new one.
- Hiding Network/Host artifacts is annoying because they have to alter the malware itself and maybe even change their setup.
- Changing tools is challenging because the adversaries must develop or acquire new tools to stay undetected which takes time, money and skill.
- Altering Tactics, Techniques and Patterns (TTP) is extremely tough, because it requires the hackers to completely rethink their strategy and change up habits.
The key takeaway from this is, The higher up the pyramid the organization focuses their defenses on, the more resources the attackers will need to invest.
2 Application Security
Securing your applications might sound difficult but there are many tools out there that can help a lot. The three big code repository hosting services Gitlab, Github and Bitbucket all come with tools for static code analysis. Static code analysis can help the developer to spot vulnerabilities inside the code before it is deployed. With tools like “Snyk Code”[^4], an analyzer that leverages machine learning to search through millions of open source libraries, static code analysis can also be performed directly inside the IDE, allowing the developer to fix identified vulnerabilities such as exposed credentials or insecure code before they even get into the repository. This has the advantage that the developers can already spot mistakes before pushing their code which saves time needed for fixing these issues later on. But one should not expect these tools to find every vulnerability. Many of these tools will not find so called logic errors inside the code which typically are miss-ordered conditions, or incorrect assumptions on runtime. Logic errors can be found by using a methodology called “test driven development” where the developer writes the test for a feature first before implementing it. An alternative to the common static analysis tools is a more advanced code analysis tool like SonarQube[^5] which utilizes Artificial Intelligence (AI) to uncover more complex problems like maintainability as an example. They also check the third party libraries used inside the project which many tools do not. But relying on tools alone can be a costly mistake. It is therefore advisable to also invest into the adaptation of secure software development guidelines such as the developer guide from OWASP[^6]. It is one of the most recognized frameworks for Application security next to the standards published by the National Institute of Standards and Technology (NIST). Aside from code analysis and coding guidelines, Web application Firewalls also known as WAFs filter the incoming HTTP traffic as well as the outgoing traffic of your application. They work independently from the application but can be quite costly, with costs ranging up to over $100 per month per application alone. On the other hand however, all of the hyperscalers like AWS, Azure and google cloud come with native solutions which require minimal overhead.
Network security
Monitoring an Enterprise Network can be a challenging task, and without the tools it is nigh impossible for humans to keep up with the traffic. The employees in charge of monitoring the network will fall into a phenomenon known as “alert fatigue.”[^7] It occurs when “[…]cybersecurity professionals are inundated with such a high volume of security alerts that it leads to a diminished ability to react effectively to and investigate real threats.”[^7] This flood of security alerts usually stems from […] not filtering or prioritizing alert-triggering issues as well as unmanaged incoming notifications. In many cases, it’s a combination of these reasons.”[^7] Of course there are other reasons as well, but all of this can lead lead to missing real security breaches or at least very delayed reactions to it, because the analysts are flooded with so much information that the important is drowned out by the less important. To fight this issue, companies often use a Security Information and Event Management system (SIEM). A SIEM is an “Application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface.”[^8]. To further help the security analysts, some also use a Security Orchestration, Automation and Response system (SOAR). As the name somewhat implies, it orchestrates different systems like SIEMs, Firewalls or EDRs to automatically respond to security incidents following predefined workflows[^9]. SIEMs together with SOARs work for a wide variety of systems. If a company is exclusively focused on securing their network, a combination of an Intrusion Detection system (IDS) with an Intrusion Prevention system(IPS) should be the way to go. While a SIEM system gathers logs from a wide variety of systems and analyzes them, an IDS only focuses on network packets. And while a SIEM is fast in processing the logs, an IDS works in real time and can send out an alarm to the IPS more quickly. On the other hand, an admin running a vulnerability scan might trigger an IDS alert because the IDS does not have the full context like the SIEM does. It does not know anything about the vulnerability scan being run but only sees the network packets, which could lead to more false positives.
Client devices
When it comes to end user devices used inside the company network, one of the first things to think about would be passwords. According to a publication from NIST in 2024, they recommend that “Users should be encouraged to make their passwords as lengthy as they want, within reason. Since the size of a hashed password is independent of its length, there is no reason to prohibit the use of lengthy passwords (or passphrases) if the user wishes. Extremely long passwords (perhaps megabytes long) could require excessive processing time to hash, so it is reasonable to have some limit.”[^10] In contrast to that, the German “Bundesamt für Sicherheit in der Informationstechnik” (BSI)[^11] recommends a password length of “[…]at least eight characters long and consist of four different types of characters (Uppercase and lower case, numbers and special characters).[…]” or “[…]20 to 25 characters long and two character types are used (for example, a sequence of words). It is then long and less complex.[…]” In practice, companies should strive for password policies with a required length of at least 12 characters without restricting special characters. When it comes to monitoring the devices for suspicious activities, Endpoint detection and response systems (EDRs) are typically used to monitor these. As the name implies, EDRs not only detect threats or suspicious activities on end user devices, they also provide the possibility to automatically respond to such incidents[^12] which makes them a powerful tool to use on the defensive side. Examples for Endpoint detection and response systems would be Crowdstrike Falcon or the Microsoft Defender for Endpoint. While EDRs are are a good choice against foreign actors, they re not as powerful if the threat comes from within the organization. If the scenario of an internal employee becoming the malicious actor occurs, EDRs are usually very limited against the extraction of sensitive information, given the employee has legitimate access. This is where Data Loss Protection systems like Symantec or Forcepoint come into play. They can prevent the extraction of sensitive information from within, which would look like a legitimate email to an EDR for example[^13]. To prevent access to sensitive information, an Identity and Access Management (IAM) system can be used to filter precisely, who can access which resources. This is done by a simple implementation of policies in the IAM system. Some Cloud providers like Microsoft, AWS and Google come with their cloud native IAM solutions, but there are also other solutions for on-premise or hybrid scenarios like Ping Identity, which is quite popular in the finance industry[^14], or IBM verify, which can be used as a hybrid IAM system[^15].
Physical security and employee behavior
Of course, not only do the digital assets need protection but also the physical ones. Not every employee should have access to the servers or to areas where increased protective measures should be taken. Maybe there are areas where hazardous elements are used and therefore one must wear protective gear or there are parts which are sensitive to electrostatic discharge. No matter what it is, there will be reasons to restrict certain areas for some employees. To implement this, a possible solution could be the use of ID cards. Combining the ID cards with different levels of authorization and locking mechanisms on doors leading to those restricted areas can improve the security of the protected assets. At the same time, this also serves the purpose of knowing who is a legitimate employee of the company, who is a visitor and who might be trying a tailgating attack. Tailgating is a social engineering attack in which the attacker gains unauthorized physical access by following a legitimate employee. The most basic form of tailgating is simply following a legitimate employee close enough, so that when they open a door with their ID card, the attacker can enter right after them while the door is still open. In other times, excuses may be used like that the attacker has left their ID card on their desk. Having physical security measures such as separation systems or ID card locked doors in place takes the attacker more effort to construct convincing lies. Physical protection alone only gets one so far. Raising the security awareness of all employees helps reduce the risk of social engineering attacks in general. Social engineering in general is the “manipulation of individuals into divulging confidential information or performing actions that compromise security[…]”[^16]. Humans are likely to trust other humans based on inherent trust, which makes them a vulnerable target for a foreign adversary. This also comes with the added bonus of not having to deal with all of the digital security measures in place. It is therefore crucial to raise the awareness of all employees to not fall victim to those attacks.
Conclusion
It is not advisable to only focus on one specific area when protecting an enterprise environment. There are many different ways adversaries can attack a company and therefore, all of them must be protected to keep the assets secure. Just because the attackers might overcome one line of defense it doesn’t mean that they will have free reign then. The other defensive measures are still active and able to detect unusual patterns which makes it harder for attackers and therefore less lucrative. This is why defense in-depth is so important. The better the security, the less likely it is that a hack will be successful albeit the probability is never zero.
Sources
Pyramid of pain: https://www.attackiq.com/wp-content/uploads/2019/06/blog-pyramid-pain-01-768×432.jpg
[^1]:https://www.forbes.com/advisor/education/it-and-tech/cybersecurity-statistics/
[^2]:https://www.ibm.com/reports/data-breach
[^3]:https://acsense.com/blog/ibm-2024-cost-of-data-breach-report/
[^4]:https://snyk.io/product/snyk-code/
[^5]:https://www.sonarsource.com/solutions/security/
[^6]:https://owasp.org/www-project-developer-guide/assets/exports/OWASP_Developer_Guide.pdf
[^7]:https://www.proofpoint.com/us/threat-reference/alert-fatigue
[^8]:https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-128.pdf
[^9]:Mike Chapple, James Michael Stewart, Darril Gibson (2021). (ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide (Sybex ed.). pp. 845–846. ISBN 978-1-119-78623-8.
[^10]:https://pages.nist.gov/800-63-4/sp800-63b/passwords/
[^12]:paloaltonetworks.com/cyberpedia/what-is-endpoint-detection-and-response-edr
[^14]:https://www.pingidentity.com/en/solutions/industry.html

Leave a Reply
You must be logged in to post a comment.