Welcome to the second part of my series about malvertising. In this second post, we’ll get to the important stuff: What is malvertising and how often do these attacks happen?
As previously mentioned, the word malvertising is composed of advertising and malware. It’s an attack form in which a victim is infected by malware through advertisements on the web. This phenomenon has been around since ca. 2007 and more prominent attacks have taken place in the last few years.
Malvertising can be divided into three different forms of attacks: Drive-by-Downloads, deceptive downloads and attacks via browserplugins. The most sneaky attack form of these is the drive-by-download. In this attack form, infected ads redirect users to a website with an exploit that uses weaknesses in browsers or browser plugins (Flash, PDF, etc.) to be able to run malicious code on the users system. For this to happen, the user often doesn’t even need to click on the advertisement. The second attack form is deceptive downloads. In contrast to drive-by-downloads, no weaknesses in browser add-ons are used but „weaknesses“ in the user. The user is deceived to click on the advertising and download the malware himself. For example, the ad could show a fake update message for the flash player. If the users clicks on it, a download is started with the malware. If the user then executes that program, the infection happens. The third form of malvertising is using browser plugins. Some browser plugins inject advertisements into web sites. This can happen when loading the site or on mouseover on some keywords. A study says, that 20% of advertisements delivered by browser plugins are malicious advertisements.
So this, in short, is, how users can get infected with malware through malvertisements. A very important question is now: How do these advertisements get to the user? As was discussed in the first part of this article series, ads are delivered to the user by ad networks or ad exchanges. But don’t these check the advertisements they deliver for malicious content? Turns out they don’t. There is often some kind of „creative quality assurance“ between ad networks and advertisers, but this is more concerning the visual quality of the ads and less the security. Another fact playing into the hands of attackers is the so called ad arbitrage. Ad arbitrage or Ad syndication is a practice that is used in ad networks and ad exchanges wherein the ad spaces at the publishers are sold again after they were sold before. By offering the ad spaces they bought, some advertisers can make profit. This can happen on some different ad network or ad exchange. This makes it difficult for a publisher to make sure, that only clean ads are shown on his page. By using Real Time Bidding, controlling the security aspect of advertisements is hard on ad exchanges. Other possibilities of malicious ads getting into ad network are hacking and social engineering. For social engineering, an attacker first offers legitimate ads to the ad network and later turns on some malicious code to turn the advertisments into malvertisements.
Now the questions are: How often does it really happen? Is it just some marginal issue or a real threat to users? What ad networks deliver malvertisements? On what pages are the malicious ads shown?
An answer to this is given in the paper „The Dark Alleys of Madison Avenue: Understanding Malicious Advertisements“ (pdf). In this paper the researchers made comprehensive measurements to learn about the share of malvertisements in all advertisements. In order to achieve this, they first collected a total of 673596 unique web advertisements. They achieved this by scanning websites in a datafeed from an antivirus company and the top and bottom 10000 pages from the Alexa website ranking as well as 20000 randomly selected sites from the same list. The obtained advertisements were then examined whether they’re malicious or not. For this, the researchers used different oracles including VirusTotal, which scans the advertisements and resulting downloads in over 50 different antivirus products.
In total, the researches found 6601 malicious advertisements. This corresponds to about 1% of all advertisements collected, which is a rather high percentage. The researchers then continued to collect data about the found malvertisements. First of all they were interested in the ad networks by which the malicious advertisements were delivered. They found that one particular ad network had a share of one third of all their delivered ads that were malicious. The researchers also looked at the size of this ad network and found that this is a rather small ad network, as were almost all of the ad networks that delivered malvertisements. This backst he thesis, that malvertisements are mainly delivered by small ad networks. One ad network stood out, as it had a percentage of about 3% of all delivered ads and had a high amount of malvertisements. The researchers also examined, on what types of sites malvertisements are shown. The results of these findings can be seen in the folllowing two graphs. It seems clear, that attackers mainly focus on the top sites on the web and that malvertisements are shown on every category of websites and not only on especially „dark“ parts of the web.
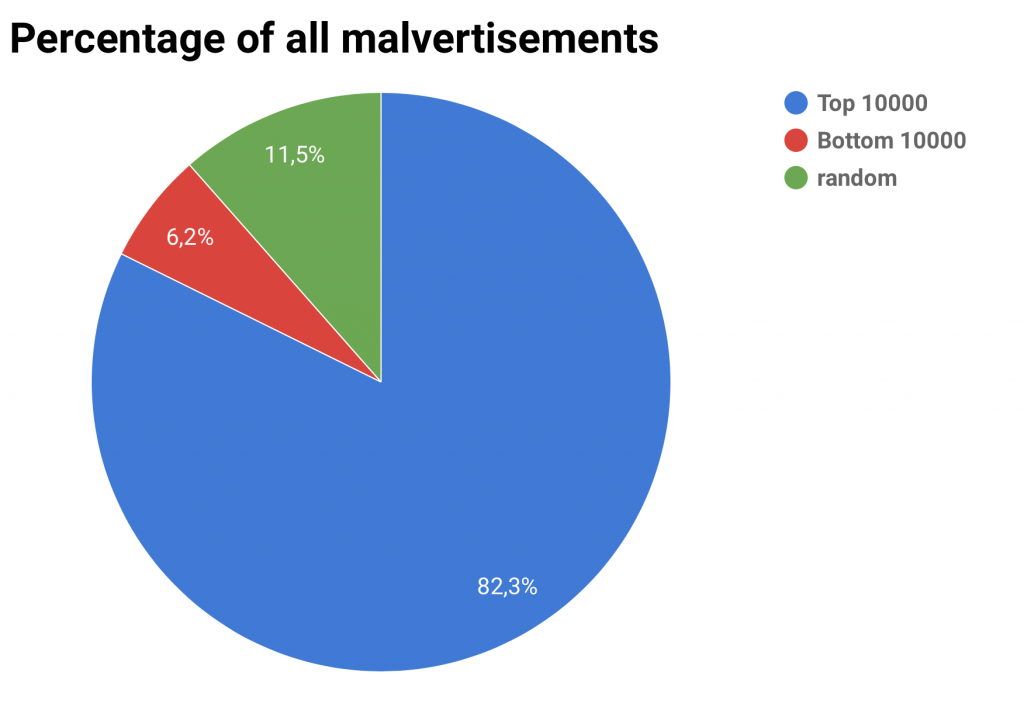
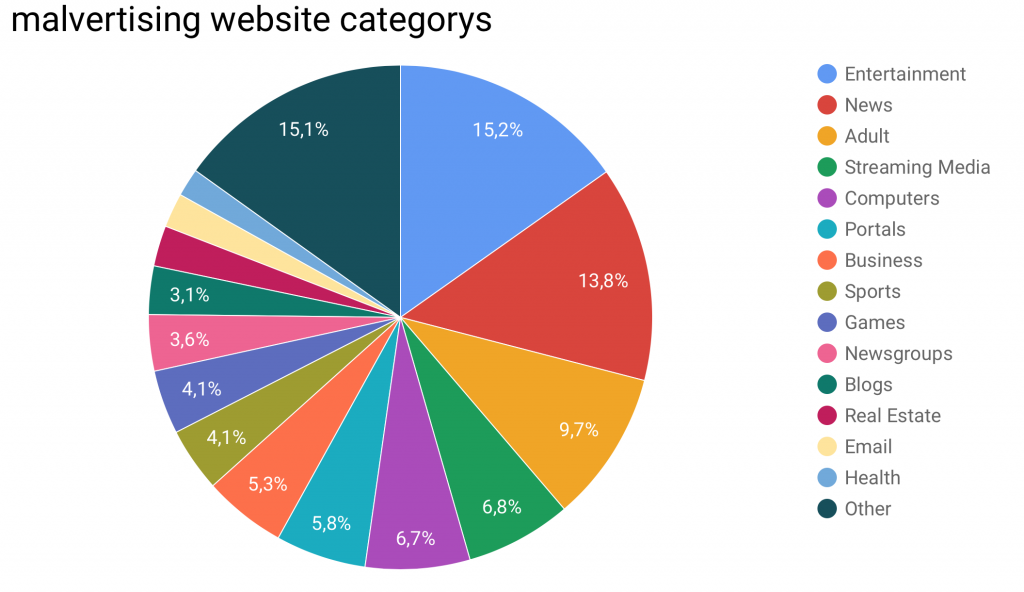
Malvertising has been on a rise in recent years, as is shown by these recent attacks. So the question remains, what can you as a user do against malvertising attacks? The answer is dillusioning: not much. Since most attacks use weaknesses in browser plugins, one way to stop infections by malvertisements would be to disable all of them. But this is not a realistic option, as this destroys much of the user experience and the fun in the web. Another way would be to use an adblocker, but this destroys the business model of many websites.
At the end of this article, a few questions remain: How can you realise a security check of advertisements before they’re delivered to the user? Is this even possible considering the real time bidding in ad exchanges? Could this check be realized inside the users browser? Would it be a solution to just sandbox all advertisements inside a website, so they can’t execute malicious code? Are secure ads even possible with the current ad system or should there be a rethink? All these questions remain unanswered for now, but could be a subject of further research.


Leave a Reply
You must be logged in to post a comment.