Smart thermostats, lamps, sockets, and many other devices are no longer part of any futuristic movies. These items can be found in most households, at least in parts, whether in Europe, America, or Asia. A trend that affects the entire globe and is currently gaining ground, especially in industrialized countries. It seems to be obvious that there is no way around a smart home in the future. Questions that arise are: whether these devices are safe, currently gaining ground, or can they be safe at all, and what practices are in place to secure them?
Take a look at the current trend
The following chart shows the growth trend for smart devices from 1990 to 2020. This curve appears almost exponential. While it began in the early nineties with computers, now the most diverse types of equipment are affected by this trend. Light bulbs, toothbrushes, locking systems, public devices such as traffic lights or household devices such as robot vacuum cleaners are among those.
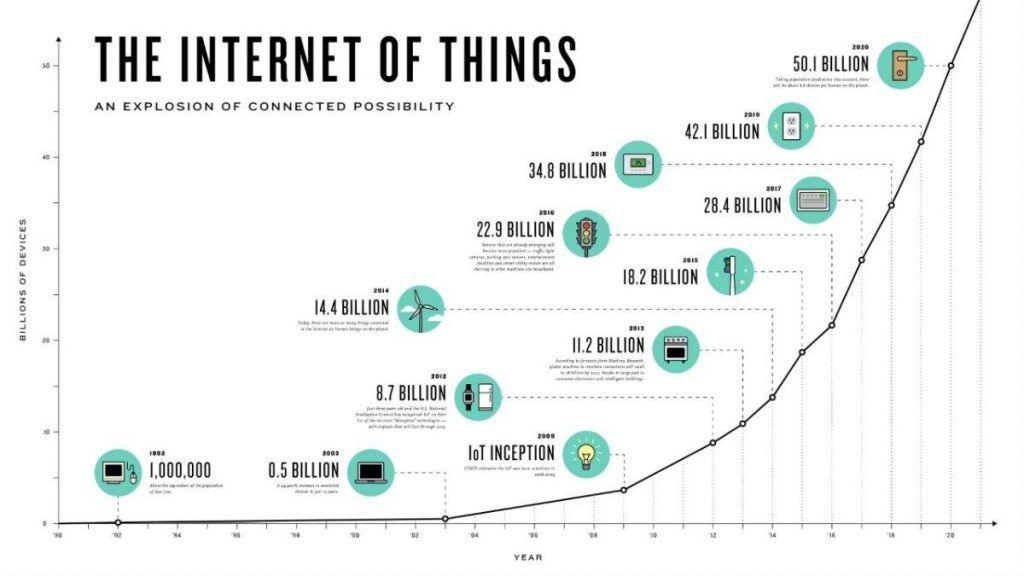
By the year 2020, as shown in the figure, a total number of 50.1 billion IoT devices has been reached. Calculated with the current world population of about 7.8 billion people in 2020, this means that there are about 7 devices for every person. As the number will be lower in developing countries, this means that even more devices will come to an average person in an industrialized country. Those numbers emphasize the importance for everyone to become better informed about IoT and especially the security aspect of all those different devices.
A more detailed examination of the problems
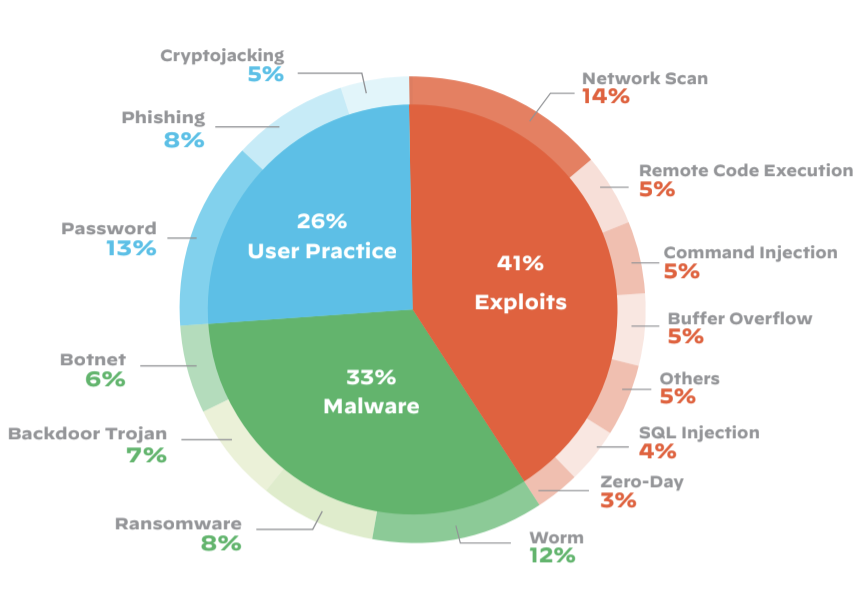
It is worldwide known that many IoT devices have major security vulnerabilities. Due to the many known security holes and no update strategy, IoT devices are the low hanging fruits for hackers. They can use the devices for example to build a large botnet or to get access to personal data of other people. The subsequent chart shows some of the top IoT threads of 2020.
41 percent of the top threads go out through exploits, where hackers take advantage of existing security holes. And even 26 percent of the attacks are caused by bad user practices. Therefore, it can be concluded that we need different approaches to solve the problems.
General problems of IoT devices
One problem that leads to security risks is the increasing autonomy of the devices. An example of this is the increase of machine learning. But what happens if the hacker manipulates the algorithm in a direction that can lead to human injury? This is not as unrealistic as it seems at first glance. Applications that should control autonomous driving can be influenced, for example, by applying a physical perturbation to a stop sign. So how much autonomy should a device get and how safe can a machine learning system be developed? These questions do not have a clear answer yet but they will gain relevance in the next years for sure.
Another major problem of IoT devices is that they can have physical effects on their environment. It must first be said that information security is based on three important points:
- The confidentiality of the data
- The integrity of the data
- The availability of the data
In the past attacks to IoT devices were mostly done in the area of data security to get access to confidential data. Nowadays, IoT devices can be used for attacks on integrity or availability. By attacking the integrity of a stove, it is possible to influence the temperature and thus start a fire. Or by attacking the accessibility of a braking system, it is possible to deactivate it and create a crash. On the one hand, it is dangerous that these devices can have these physical effects. But on the other hand, without this “smart” physical effect they are just normal devices and they would not make our lives any easier.
A root cause of this situation is that the production of the IoT devices should be as cheap as possible. Therefor low security standards are implemented very often with no option to update the system. This leads to the security problems we see on the IoT devices.
Problems concerning the companies
The security risk caused by the low-cost production of IoT devices is mainly defined by the companies. As there is always a trade-off between the costs for additional security or features, device performance or customer satisfaction. When an offering manager needs to decide between features, performance, usability, or security for a new IoT product, the decision rarely falls on security. It is hard to blame him, because his action correspond to the current market and the market is not willing to pay more for security. More about end users belonging to the market will be discussed in the next section
Another aspect regarding the security problems from cheap production of smart devices is the supply chain. Hardware is made in China, software developed in India and marketing is done here. Such exemplary supply chains are not unusual nowadays. Everything is produced or purchased where it is cheapest. This results in complications in the enforcement of certain security standards within the supply chain. Subsequent improvements of security features are usually difficult or impossible.
A company should always close known security holes or prevent them from the beginning. This may sound simple, but in practice it is complicated. Many IoT devices do not get regular updates or are not able to update at all. Only the way companies design their products could fix this serious problem. As shown in the last graph, 41 percent of attacks are carried out via exploits. Some of the system vulnerabilities are known, some are not. Every company should see it as their duty to close known vulnerabilities with updates and therefore offer ways to do regular updates. But how can they be motivated to react with regular updates? And how can small and medium-sized enterprises be pushed to implement this? If there would be a clear answer to these questions, they would probably already be common practice today. In the continuation of this article, we will look at the different options that can be taken.
Problems concerning the users
End users determine the market by their demand. So, if we are not willing to pay more for more security, how can we require that we get more secure systems? Any decision, even if only unconsciously, for cheaper products with less security reinforces the assumption that users are not willing to pay more for security. For companies, therefore, raising the price for security would mean an economic loss. But is it possible to change the mindset of the end user?
But not only the motivation to pay more for a feature which is not visible to users is missing, also the user knowledge to take action for better security. By looking at the last chart, it can be seen that 26 percent of the top threads are made possible by bad user practice. It already starts with the simple choice of a secure password. Isn’t this something we are reminded of every time we register for a new app or website? It seems that this is not enough, maybe because it is just an IoT device running at home in your own four walls. Who thinks about the fact that an unknown person might soon have access to the smart camera as well? This probably only happens to others in foreign countries and not to me. A wrong but often chosen solution is to ignore the problem.
The points above do not represent a complete list of problems. But they certainly contain some of the important points, which is why we have such insecure IoT devices in place. So, what can be done to solve these problems and improve the IoT security situation?
Solutions to increase the security
The question that probably arises now is why to only increase security and not guarantee it completely. The answer is provided by the following quote from Gene Spafford in 1989:
The only truly secure system is one that is powered off, cast in a block of concrete and sealed in a lead-lined room with armed guards – and even then I have my doubts.
A completely secure system is therefore not possible. Every action taken is only intended to increase the current security of the system. So, the question you should ask yourself is: where is the best place to start? This is no easy question. There are different areas where it can be applied, whether it is the government, companies, or end users.
The following graphic shows the interaction of the important instances. Although the government cannot change anything directly on its own, it can have an influence on end users and companies. End users and companies also influence each other. The form in which this can take place is explained in more detail below.
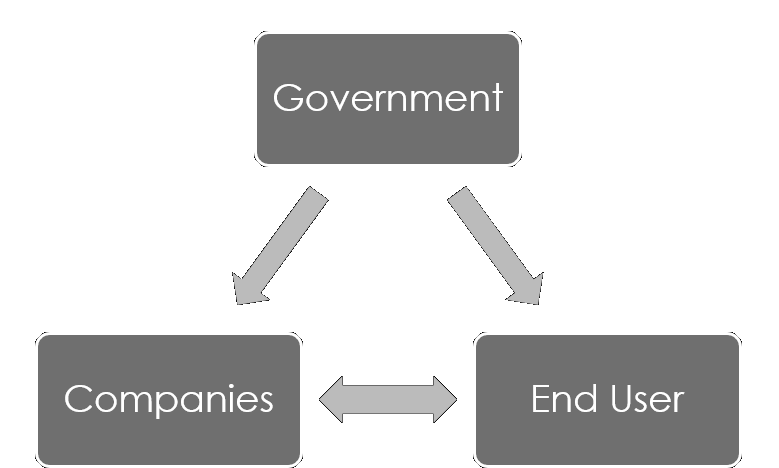
The influence of end users
If there is a possibility that the user’s mindset could be changed, this would increase the security of the devices in the near future. As explained above, demand determines the market, and the market influences companies. Maybe a statement on unsecured products like “there is a high risk that a hacker could take it over” could help to motivate? But to be realistic, mindset change does not happen overnight, otherwise, there would probably be no wars, violence, or injustice in the world. Moreover, not everyone has the money for more expensive products and thus the possibility of this change. So, it can be concluded that a mindset change alone is not the solution.
Even without influencing the market, there are possible actions for end users to achieve more security. There are many tips and tricks on the internet to help users to use their IoT devices more safely. But who reads security tips before they integrate the device into their home network without being affected in the past? An awareness of the risks must be created so that at least some of the following tips are applied:
- Are regular updates offered and how long are they offered? What data is collected and what data is stored locally or in the cloud? Is it possible to use the device offline or does the toaster only work when it is connected to the Internet? Is encrypted communication guaranteed? There are many of these questions, which should be answered satisfactorily before the purchase.
- After the purchase think about whether you really need the online function. If this is not the case, the possible risks have already been significantly reduced. If an Internet connection is desired, a separate network for the smart home devices should be considered.
- Right from the start, ensure that all possible settings are selected as safely as they can be. Default passwords should not be used and be replaced with strong passwords. Even with secure passwords, it is probably time to activate the router’s firewall and not protect it with a default password either.
From the above points, it should be clear that the user himself can have a great influence on how secure his IoT device is and hopefully avoid that his device does become part of a botnet.
The power of the companies
It is the companies that have the greatest influence on the safety of their own products. To relieve users of responsibility, companies can already use more secure default settings. Instead of default passwords for each device, a unique generated strong password should be used. Updates should be offered on a regular basis and, if possible, also provide the setting so that they are installed automatically. There are many best practices such as these, but the question remains open which ones are mandatory and which ones can be omitted? More on this will be discussed in the penultimate part of this article.
A probably less practical tip for a solution could be a security transparency to the customers. So that the potential customer knows beforehand which security problems are covered and which are not and when no more updates are offered.
The security of many of those IoT devices and the software running on those is tested after they have been produced. A change in the thinking of how important security is and that it should be integrated from the beginning is named security by design. The following points can be counted as examples:
- Encryption of data traffic should not be an option but should be standard.
- Known threats to security should be avoided from the start of implementation.
- Security tests should test the system for common threads before release.
- If there are already good implementations that have been extensively tested, such as protocols, they should be used instead of own or unknown solutions.
The possibilities of the government
The question that is now left open, is what can the government do to improve the situation? As you can see in the last chart, the government can influence the users as well as the companies to protect their citizens and their domestic economy. First of all, it requires an appropriate authority to take care of the concerns of IT security. Like the Federal Office for Information Security (BSI) in Germany or the Communications-Electronic Security Group (CESG) in Great Britain.
In order to have an influence on the companies, regulations or certifications can be used. The introduction of certain standards means that companies are forced to implement them. A drawback of this solution is that it only affects certain regions of the world or individual countries. Companies that are not affected do not have to implement these standards, therefore they can produce cheaper and, in the end, their products are much cheaper. Non-uniform solutions can, therefore, lead to an imbalance in the market. Another disadvantage of these regulations is that they usually take late effects and are not comprehensive enough.
Certification of companies can be used to give users a better overview. The question remains what such a certificate must cover or whether there are different levels? And do the users have any interest or understand the reason of those certifications? If there is no interest, certified companies are again spending more money during the development without getting the investment back and this should be avoided.
Education could be a way to convince users of such certificates or to create general awareness. This is not a short-term solution but must be addressed for the future. Spending money now on education to develop IT security awareness could have a positive impact on the “smart” future. But the time to start is now, so that besides standard literature and mathematical formulas also the foundations for IT security will be established.
How to handle the “best practices”?
As I mentioned before, there are many suggestions, especially for companies, what they can do to achieve more secure systems. A recently published paper [6] deals with these proposals, analyses them, and provides companies for their analysis. But why do companies need help with this important topic?
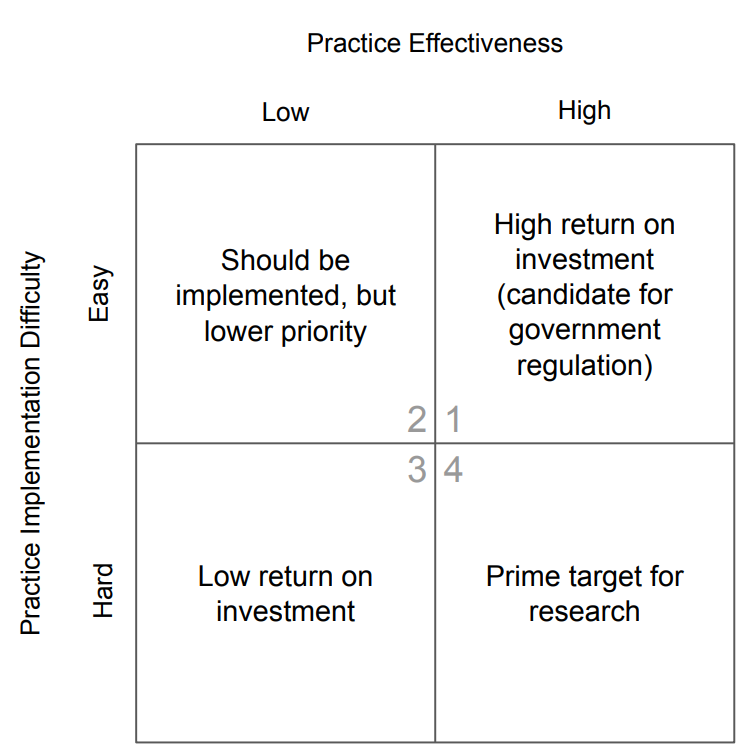
Within the paper, it was noted that there are major misunderstandings about what really is “best practice”. Four categories were developed in order to classify them as shown in the following figure, these result from the implementation difficulty and the practice effectiveness. In addition, there are recommendations at which points in the life cycle of an IoT device these specifications get relevant. Furthermore, stakeholders have been identified which have an influence on the life cycle of a product. Through their research with the help of 1014 guidelines, they were able to determine that approximately 70 percent of these must be implemented very early in the life cycle of the product. In other words, it must be applied during the manufacture of the product hardware, which presents certain difficulties due to the supply chains as previously mentioned.
In conclusion, they note that about 91 percent of best practices are insufficiently defined, which can lead to misunderstandings and incorrect implementation. Thus, in order to provide stakeholders with real best practices, they need to be more specific and not just thought-provoking. Only then is it possible to achieve a good IoT security foundation.
If you or your company plan to implement one or more guidelines and do not really know where to start, it is really worth taking a look at this paper.
Conclusion
So, it is clear that there are different contributors that have an influence on better IoT security. There are different approaches to achieve possible solutions, including clear guidelines, regulations, personal responsibility, and much more. But in the end, the companies have the greatest influence and must be put on the right track from all sides. It is not clear whether it is a solution forced by the state, influenced by the user, or forced by expensive legal proceedings to reach a better security foundation. But one thing is clear, there must be a solution in the near future.
At the end of the day, there is no way around the IoT and therefore IoT security. With the increase of home office due to the Corona crisis it gets more and more important for companies that employees have a secure home network. Therefore, maybe the current pandemic crisis leads to improved awareness of the security problems within the IoT: “Alexa, lights off”.
Sources
[1] Schneier, Bruce (2018): Click Here to Kill Everybody. Security and Survival in a Hyper-Connected World.
[2] https://unit42.paloaltonetworks.com/iot-threat-report-2020/
[4] https://dzone.com/articles/10-iot-security-tips-you-can-use-to-secure-your-io
[5] https://www.schneier.com/crypto-gram/archives/2020/0715.html#cg12
[6] https://arxiv.org/pdf/2004.12179.pdf
Image Sources
[1] https://sites.google.com/site/iots160567385/home/the-trend-of-iot-in-the-market
[2] https://unit42.paloaltonetworks.com/iot-threat-report-2020/

Leave a Reply
You must be logged in to post a comment.