Most companies use perimeter security to secure their cooperate applications, services and data from attackers and unauthorised users. This approach includes a cooperate network, where clients, that are part of the network are able to access the applications. This includes attackers that got access to these networks.
Additionally more applications are getting shifted from cooperate networks into the cloud and clients are getting more mobile from day to day. It’s getting increasingly difficult to trust or identify who and what should be allowed or trusted with access to their network. That means that setting up firewalls and other security mechanisms, securing the perimeter, is getting a real challenge and can result in very high costs. [12] [13]
In order to adapt to the new requirements and to create a system that is compatible with the cloud- and the cooperate applications there is a new security approach: Zero Trust Security.
Zero Trust Security
Zero Trust Security is a security approach that is mainly the further development of perimeter security. The idea of perimeter security is gaining trust and getting access to a system when you become a member of a specific network. Zero Trust Security is based on the security and compliance of assets and not on their network location. The general assumption is that the network has been compromised. You could call the mantra ”never trust, always verify”. [4] [13] [14]
The heart of such a system is identities, representing people, services, IOT devices or other clients that want to interact with the system. There is no difference between the endpoints (contractors, partners, guest devices, apps and devices of employees) and the device own- ership does not matter. Therefore it is very important to verify this identity with a strong authentication and use mechanisms like Multi Factor Authentication (MFA). MFA improves the security and allows to authenticate even if the IP address or the behaviour of a user changes. Especially if the MFA isn’t a part of the strategy user behaviour should be monitored and used to decide whether the access is typical for a specific user or not. [4]
In addition to the authentication a strong authorisation is very important. In order to control the blast radius of an attack, users should always have the least access privilege as possible. All access is defined by policies, that describe in-app permissions, permissions based on user roles and information that is based on real time analytics and monitoring. Furthermore the level of continuous verification is going to be increased as if the permission is updated regularly and checked with each request. [4]
Since the users don’t have to be members of a specific network, the applications have to be deployed into the public internet. The so called ”intranet” doesn’t exist anymore.
In conclusion, Zero Trust Security is a more holistic security concept in contrast to perimeter security. Due to the continuous analysis and monitoring of the system it is possible to identify business processes, data (flows), users and associated risks as well. Besides this, these mechanisms help to uncover Shadow-IT. [4] [13]
Microsoft has made a small survey, asking for the biggest motivators to adopt a Zero trust strategy that summarises some of the benefits:
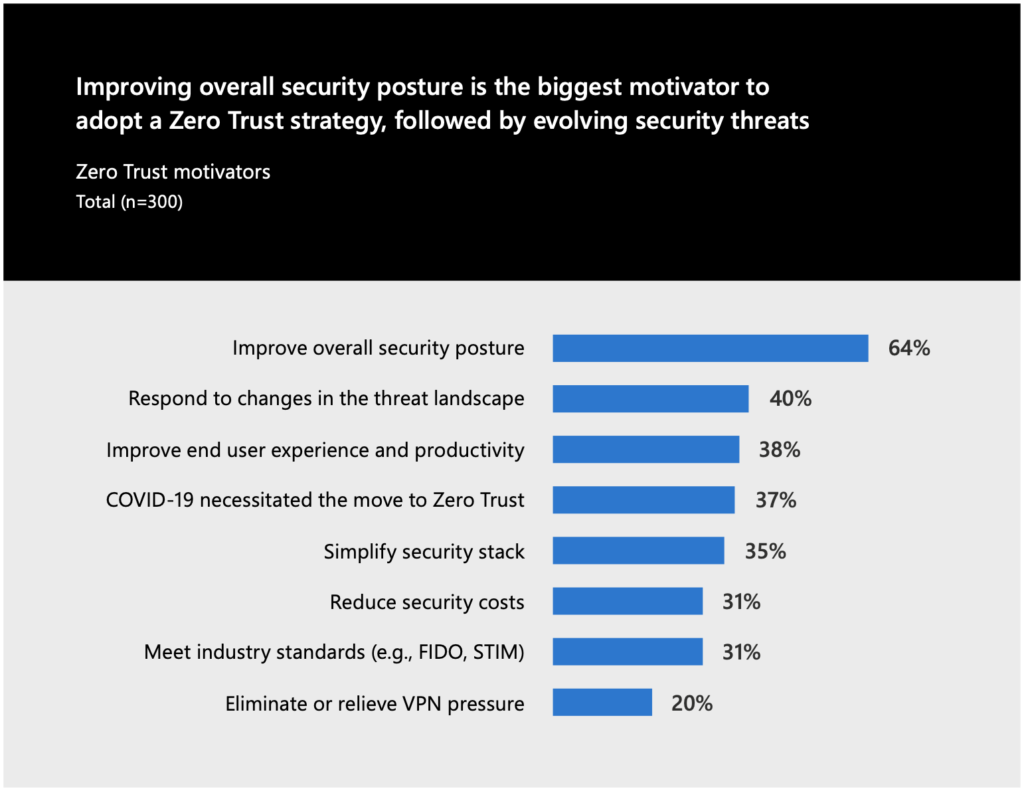
Besides these arguments some non technical aspects have an impact as well. Since all applications are available on the public internet, the employees can work from anywhere without any problems. The user experience for employees working in a cooperate building or in any other place is similar. The only difference might be the latency. Google used this argument for potential employees and they changed their orientation for hiring. [5] [12]
Goodbye VPN
Since Zero Trust Security doesn’t assume that users have to be part of a specific network, Virtual Private Networks (VPNs) aren’t needed anymore. The applications now are part of the public internet. Cooperate security stacks and data centers don’t matter. Furthermore VPNs weren’t build to manage heavy loads over a long period of time. This is what modern applications are tempting to do. [8] [11]
Besides that, especially the Corona pandemic has shown us that VPNs aren’t agile. They don’t scale very fast, are high in CPU cost, the encryption is heavy and it’s extremely expensive to maintain these systems. [8]
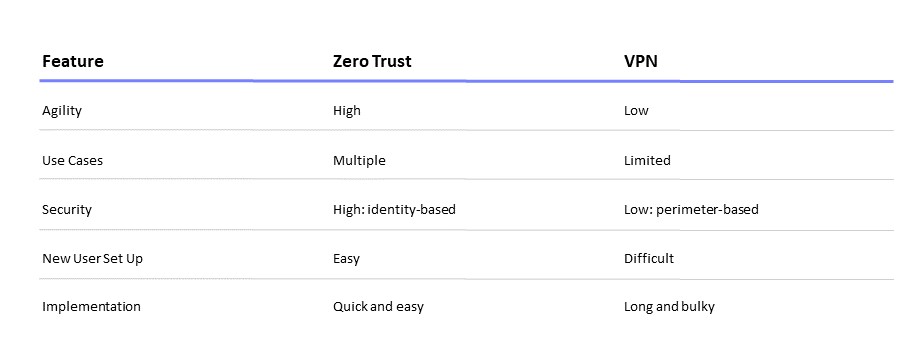
The following table summarises some of the benefits of a Zero Trust system in comparison to a traditional VPN:
BeyondCorp
For the purpose of understanding how Zero Trust Security can be implemented, we are going to take a look at BeyondCorp. BeyondCorp is Google’s implementation of Zero Trust Security and the answer to the fact that more and more services are moving into the cloud. BeyondCorp is based on three pillars [1]:
- Perimeterless design: The network does not matter
- Context-Awareness: Access to services based on user and device
- Dynamic Access Control: All services have to be authenticated, authorised and encrypted
Components of BeyondCorp
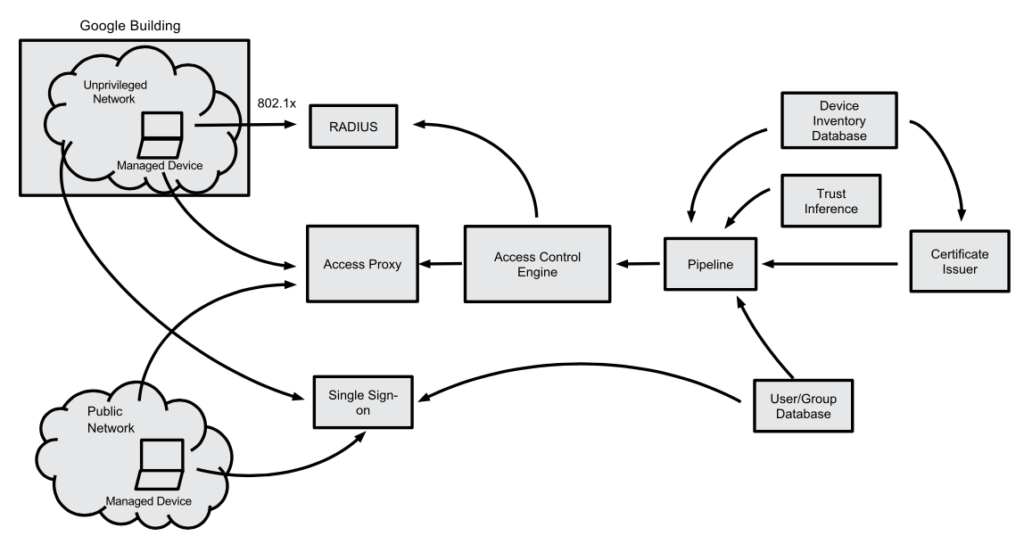
Device Management
In order to use the device as one part of the authentication and authorisation process, all devices have to be recorded. For that reason Google implemented a Device Inventory Database that saves all the managed devices Google hands out to its employees. In addition to the plain device metadata, the changes made to the devices will be tracked as well. [12]
To identify devices, each device owns a certificate that is stored on a hard- or software Trusted Plattform Module (TPM) or in a trusted certificate store. It is important to mention that the certificate does not grant any access privileges. It is used as a key to access a set of information regarding the device that will be used to grant access. Additionally, all certificates will be renewed on a regular basis. [12]
User Management
Besides the device authentication and authorisation the user is the second key element of the access control. Therefore a centralised User and Group Database was implemented which is tightly coupled with the HR processes. This is necessary so that job categorisation, usernames, group memberships and other metadata, that is constantly changing, have a direct impact on the access privileges of the users. [12]
To authenticate users, an externalised Single Sign-On System (SSO) is used that needs two factors. When everything is fine a short-lived token is returned to the user which can be used for authentication. [12]
Remove Network Privileges
The goal of the zero trust model is to remove privileges from networks to users and devices. In cooperate buildings you still want to have your own network but this network should favor a remote network. Therefore Google deployed an unprivileged network, which is like an external network that has a private address space. This unprivileged network is connected to the internet and all devices in cooperate buildings are able to connect to that network. To make sure that you can’t access other Google networks an access control list (ACL) will be used. [12]
If your device is located in a Google building, a second mechanism is implemented, that decides whether you can access the unprivileged network or not. RADIUS servers are used to authenticate your device using 802.1x authentication. After the authentication the user is going to be assigned to an appropriate VLAN dynamically. If the device can’t be authenticated, it will be assigned to a remediation or guest network. [12]
BeyondCorp’s Gateway
If you want to access a Google enterprise application you have to get through the Access Proxy that is configured for each application. The Access Proxy is reachable globally and enforces encryption, load balances traffic, performs authorisation, checks the applications health and protects the application from denial-of-service attacks. [12]
In order to access the applications, DNS entries are created for each application that points to the Access Proxy. After users authenticated themselves using the SSO system, they are able to interact with the Access Proxy. [12]
The heart of the Access Control System
The heart of the access control system is the Access Control Engine which is a part of the Access Proxy that offers service-level authorisation. In order to grant access to an application the token of the SSO system and the device certificate is used. [12]
The information that is needed will be aggregated by a Pipeline, collecting all information useful for the authorisation. Information that is provided, includes certificate whitelists, different trust levels for users and devices and specific details about the user and the device. The decision process is very dynamic. That’s why it’s possible to restrict single parts of applications. An example is, that a user is only authorised if the newest OS version is installed on its device. [12]
Internal Cooperate Web Services
With the intention of providing some internal cooperate web services, that aren’t available via the public internet Google implemented a BeyondCrop Chrome Extension that routes specified traffic through the Access Proxy. This way developers don’t have to add a public DNS entry pointing to the Access Proxy. [5]
Challenges of Zero Trust Security
With all major system design changes there are some challenges as well. One of the biggest is the identity management since all applications have to work with the same users. Combining all of them is a big project and can take some time.
Besides this legacy applications could lead to problems as well. Sometimes they work with proprietary protocols that are based on TCP or UDP. Google uses SSH tunnels and on device SSL and TLS proxies to interact with these legacy apps. The challenge at this point is that the tunnelled traffic has to confirm with their Access Control Engine.
A few legacy apps using newer protocols could get addressed with the approach described in the ”Internal Cooperate Web Services” chapter. There might be services that are’t meant to run public but refactoring them is too much work and a rewrite is already in progress. Even if they are secured with the zero trust mechanism it might not be the best idea to tell the whole world of the existence of this service. With a DNS entry everyone would know the service. [9] [12]
In order to be able to perform the authorisation, a lot of data from different monitoring and analysis systems must flow together. Therefore the quality of the data has to be very good. Other systems, using the data to monitor the business processes, are dependent on high quality data as well. Otherwise decisions can lead to major problems. [9]
Since Google uses device parameters to authorise users to access resources, changing hard- ware parts could lead to issues. If the process can be tested in prevision, less problems occur afterwards when an employee receives the repaired device.
Google implemented an application that enables running synthetic records. Firstly this helps in the repairing process, since new potential parts can get tested. Secondly the test applica- tion can be used to test the whole system of authentication and authorisation. This increases the security immensely and can prevent a lot of failures.
Otherwise, such a system can get very complex and developing the interfaces is very expensive. [9]
Another big challenges is the introduction phase of a Zero Trust mechanism. Firstly there are all the technical challenges. Secondly there are the users and the corresponding user experience.
Google reported that their employees still ask for VPN access after the introduction of BeyondCorp. They were familiar with the process. To prevent this they started using BeyondCorp as one of the benefits right in the application process of new employees.
In order to inform their existing employees they created information pages on which the whole process was described. Furthermore, they added several ”obstacles”, like links to the information pages and other explanations in the registration process for the VPN. Additionally, they withdrew VPN access from employees that didn’t use it for 45 days after sending them several reminders.
Considering all you can see that it is very important to inform users about what happens, will happen, has happened. In this process users should be informed about possible side effects as well.
Google wrote a paper about this that can be found on the BeyondCorp website if you are interested in this topic. [5] [9]
The last point is less of a challenge of Zero Trust Security and more of an important component that should be considered as well and can lead to very big problems, if ignored. The issue I am talking about is disaster recovery.
If the system is compromised, a small number of maintainers should be able to restore backups. This includes users, devices, policies and other configuration parameters that have impact on the authentication and authorisation. [9]
Conclusion
All in all you can see that Zero Trust Security solves a lot of problems of perimeter security and seems like the right approach in order to get a more secure system.
Besides this, Zero Trust is a more holistic security concept and increases the over all security level. In a world where on premise installations are getting more rare and hosting applications in the cloud is the status quo, perimeter security isn’t adequate anymore.
Adding a lot of flexibility to users, it is perfect for more and more employees that want to work from home or anywhere else in the world. In conclusion, Zero Trust Security is faster and more agile compared to perimeter security, which is perfect for a permanently changing environment.
Despite of all the advantages there are some disadvantages as well.
First of all the transition from a system that uses perimeter security to a Zero Trust system can be a real challenge. In the beginning there is the whole technical environment that has to be installed and the applications that need to be adapted. Additionally, there are users that need some time to get used to the new system.
Since it is possible to manage the authorisation very granular, it can get very difficult to keep track of all policies that apply to the users. Furthermore Google showed that they aren’t ready to tell everyone which services they are using, by not adding public DNS entries for applications.
In a world of browsers – A look into the crystal ball
Besides BeyondCorp there exist several movements pointing into the future and showing how we might work then.
In the future employers might just hand out cheap laptops that only run a browser. With the user account and the cooperate device that’s signed, employees could get access to all the applications and services they need to work with. I think authentication and authorisation without device certification isn’t likely and bigger companies won’t take that risk. Besides this, all we need is a browser that can interact with our Zero Trust System and the cooperate applications.
With Zero Trust Security we solved the problem that we have to work from a specific (network-) location in order to access cooperate services. In the next few paragraphs I am going to show several projects, adapting Zero Trust Security on other areas like computing and even browsing.
Windows 365 – Zero Trust Computing
Microsoft deployed a PC into the cloud that ”follows you wherever you go”. Mainly what they did was, that they built a browser adapter on top of their Azure Remote Desktop machines. This allows users to access a virtual Windows computer with the help of any browser. With the help of the Azure Endpoint Manager administrators are capable of managing users and devices that are allowed to access this virtual Windows machine.
Besides this hosting the computer in the cloud enables users to scale their device according to their needs. If a user is only doing small business related tasks, there is no need for a lot of computational power. If there is need for more power, for example to build your code as a developer, you can scale the power of your virtual computer. Also, removing the need for several firewalls, security agents or the installation of VPN clients. [6] [7]
On August 2nd, the service will be available to the community and prices are going to be be revealed. I can imagine that the service will be very expensive and doesn’t compete with desktop computers yet. Besides this, the idea is very good and might be successful. In contrast to the advantages, you could ask yourself why there should be desktop computers in general, as every application could get deployed to the web.
Cloudflare’s Browser Isolation – Zero Trust Browsing
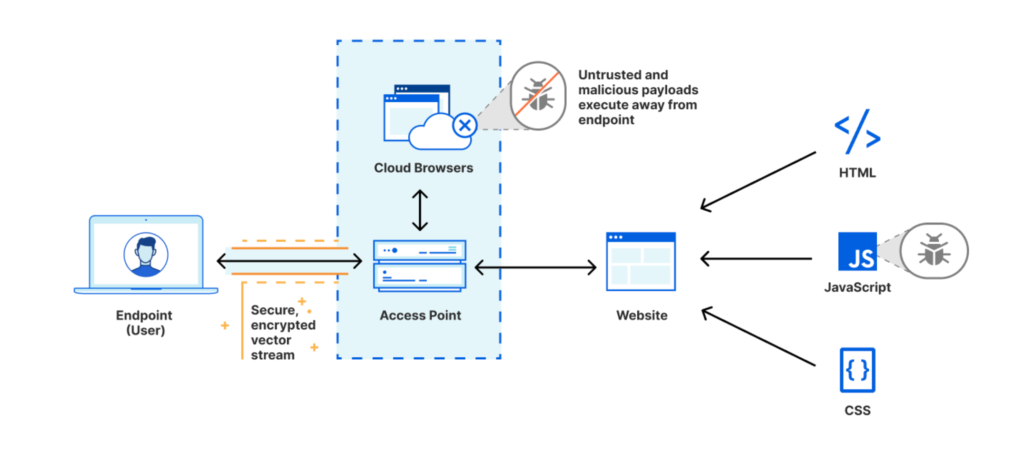
Cloudflare’s Browser Isolation [2]
With Browser Isolation by Cloudflare, everything is getting pushed a bit further. Instead of having a computer running in the cloud (Windows 365), they have a browser running in the cloud. This ”cloud browser” assembles the requested websites and only transfers the screen to the client. The technology they are using is called network vector rendering. To perform even faster, Cloudflare is hosting their browsers right at the edge of the internet.
Due to the fact that Cloudflare only transmits the part a user can see, all malicious code won’t be executed on a client’s device. This would lead to a securer environment for the user.
There is another benefit: saving the users data. If a user creates a new Browser Isolation instance every time they want to go to a website, tracking users over several browser sessions would be more difficult.
The mechanism allows users to access websites safely without receiving a lot of data. Nowa- days websites can be very clunky and contain a lot of resources that have to be transmitted.
Since Cloudflare only transmits an ”interactable screenshot” of the website, less data has to be transferred. This is interesting for users who don’t have a large bandwidth accessible. Images could be transmitted with a smaller resolution as well. [10] [2]
This product could be interesting for areas where very strict security is necessary. An example could be critical infrastructure. Since the code of the websites won’t be executed in their system, malicious code doesn’t affect them.
Furthermore, it is very important to mention that the client browsers using the Browser Isolation service should have security mechanisms implemented as well. It is very nice, that malicious code will be executed in the cloud and that the users don’t have to worry on the first hand. If you take a look at supply chain attacks, Cloudflare could be malicious as well. In this case you won’t have a security mechanism that secure your users.
Chromebooks
It might be possible that Google already saw the future of browsers when they introduced their Chromebooks in 2011. They were built to do browser related tasks where the data is getting stored in the cloud and not on the device. This is perfect for the shift of all applications into the cloud and the browser. In combination with BeyondCorp they are able to provide a device that can perform all related tasks right in the browser. [3]
Author: Max Merz — merzmax.de, @MrMaxMerz
References
[1] BeyondCorp — run zero trust security like google – http://www.beyondcorp.com/
[2] Browser isolation for teams of all sizes – https://blog.cloudflare.com/browser-isolation-for-teams-of- all-sizes/
[3] Chromebook – https://en.wikipedia.org/w/index.php?title=Chromebook& oldid=1035329116
[4] Examining zero trust – https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RWAoJs
[5] Beyondcorp: The user experience – https://storage.googleapis.com/pub-tools-public-publication-data/pdf/c8da594124dab1f91e6750995e2b7805403b19f1.pdf
[6] Get started with windows 365 – https://techcommunity.microsoft.com/t5/windows-it-pro-blog/get-started-with-windows-365/ba-p/2530504
[7] Windows 365, Microsoft Customers Stories – https://customers.microsoft.com/en-us/story/1394372441759478452-nunavut-government-windows-365
[8] Is VPN dead? zero trust network access vs secure VPN access – https://cyolo.io/blog/is-the-vpn-dead-vpn-vs-zero-trust/
[9] Beyondcorp: Design to deployment at google – https://storage.googleapis.com/pub-tools-public-publication-data/pdf/44860.pdf
[10] Protect teams with browser isolation – https://www.cloudflare.com/teams/browser-isolation/
[11] Secure internet gateway — zscaler internet access (ZIA) – https://www.zscaler.com/products/zscaler-internet-access
[12] BeyondCorp: A new approach to enterprise security – https://storage.googleapis.com/pub-tools-public-publication-data/pdf/43231.pdf
[13] What is zero trust? A trustworthy approach to security – https://www.mcafee.com/enterprise/en-us/security-awareness/cloud/what-is-zero-trust.html
[14] Zero trust security model and framework – https://www.microsoft.com/en-us/security/business/zero-trust

Leave a Reply
You must be logged in to post a comment.