Author: Oliver Hummel
Apache Kafka – The one Stream Processor to rule them all?
If there is one statement that can be made about the current developments in the realm of distributed systems, it would probably be how most developers are turning away from a centralised, monolithic architecture and move towards a microservice architecture. This type of architecture proved itself as much more flexible and robust for the modern…
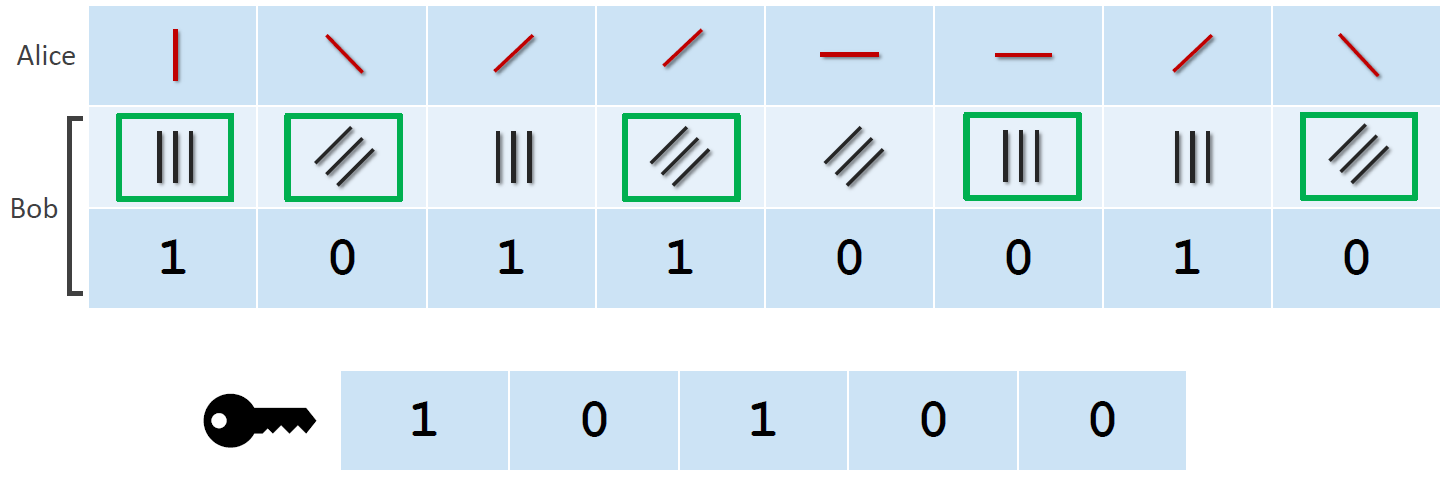
Quantum and Post-Quantum Cryptography
In a world where political activists and dissidents get persecuted by authoritarian governments, strong cryptography is more necessary than ever. But the general public benefits from it as well. Identity theft, banking fraud and cyber bullying can happen to anybody. The most effective protection is to not make sensitive material available to anybody. Unfortunately some…
