Category: System Designs
Radcup Part 2 – Transition into Cloud
Written by: Immanuel Haag, Christian Müller, Marc Rüttler Several steps are necessary to transfer the Radcup backend to the cloud and make it accessible to everyone from the outside. These are explained in more detail in the following sections.
Radcup Part 3 – Automation with Gitlab CI/CD
Written by: Immanuel Haag, Christian Müller, Marc Rüttler The goal of this blog entry is to automate the previously performed steps. At the end all manual steps should be automated when new code changes are added to the repository. The new version of the backend will be made available in the cloud at the end.
Autonomous War – Which dangers are associated with warfare without human intervention?
The term autonomous war has been a controversial topic for years. But what exactly does the term actually mean? Autonomous war means the use of autonomous lethal weapons (short: LAWs) and machines or vehicles, which are primarily used by the military for modern warfare. Autonomous weapon systems can decide independently about life and death on…
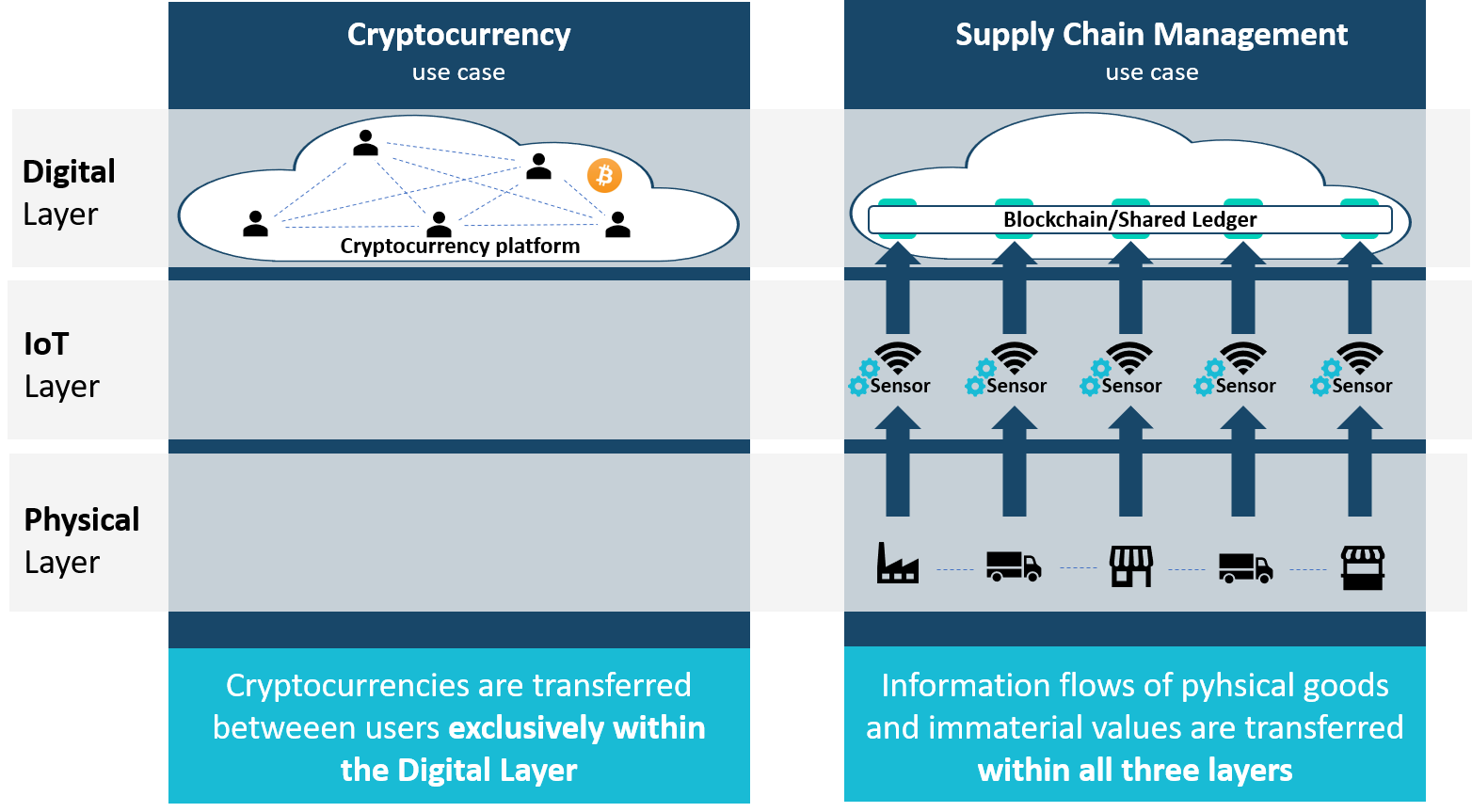
Blockchain Risks and Chances – An 2018 Overview on Public and Private Blockchain, Smart Contracts, DAOs and ICOs
A few years ago, talking about Blockchain was largely consistent with talking about the technology behind Bitcoin. In contrast, Blockchain nowadays comprises a whole technology branch, whereby the Blockchain itself can be implemented in lots of various ways. Not a year ago, on December 17, 2018, the peak of the Bitcoin hype was reached by…
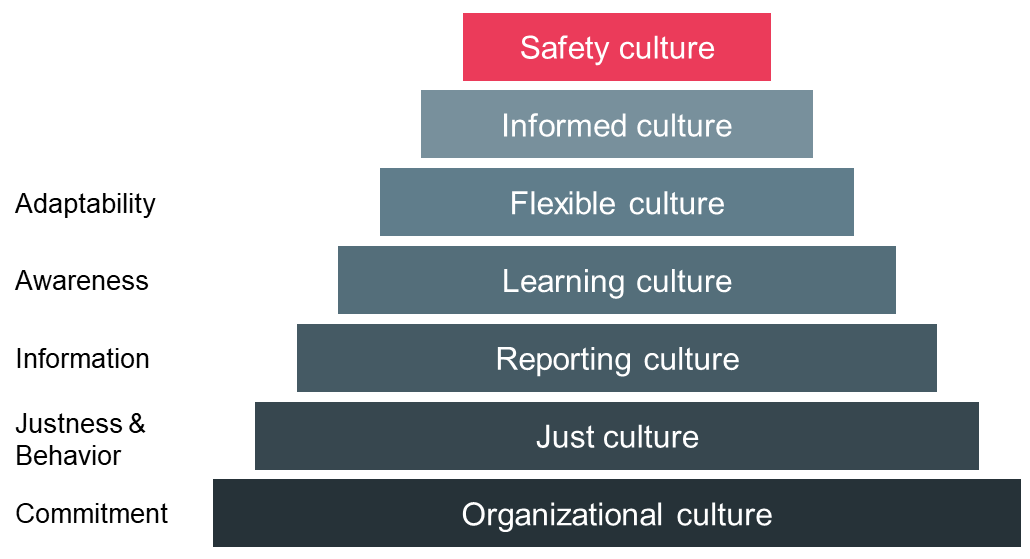
Safety Culture – Improve “the way we do things around here”
The safety culture of an organization is the key indication of its performance related to safety. It incorporates the visible rules, norms and practices as well as the implicit factors such as values, beliefs and assumptions. That is why the safety culture reflects “the way we do things around here” which is the most precise…
Smart Meter
Smart meters are a controversial topic in Germany. Still there are no certified products available although the roll out was planned at the beginning of 2018. Security breaches can affect customer data as well as the safety of the energy net. That’s why there are very strict security guidelines provided by the BSI. Several smart…
Why AI is a Threat for our Digital Security
Artificial intelligence has a great potential to improve many areas of our lives in the future. But what happens when these AI technologies are used maliciously? Sure, a big topic may be autonomous weapons or so called “killer robots”. But beside our physical security – what about our digital one? How the malicious use of…
Cloud security tools and recommendations for DevOps in 2018
Introduction Over the last five years, the use of cloud computing services has increased rapidly, in German companies. According to a statistic from Bitkom Research in 2018, the acceptance of cloud-computing services is growing. Cloud-computing brings many advantages for a business. For example, expenses for the internal infrastructure and its administration can be saved. Resource…

You must be logged in to post a comment.