Category: System Designs
How I Improved the Network Security of My Live Chat Application Architecture on AWS
In an increasingly connected world, the need for robust security measures for cloud infrastructures is constantly growing. Applications that are accessible over the internet must be secured in a way that prevents unnecessary exposure of sensitive backend components. A fully public Virtual Private Cloud (VPC) architecture may be sufficient for a quick start, but it…
Entwicklung eines skalierbaren File-Share-Services mit AWS
tl;dr: Unser Semester-Projekt bestand im Aufbau einer skalierbaren File-Share-Lösung auf AWS auf Basis von NextCloud. Unsere Motivation bestand darin die volle Kontrolle über die eigenen Daten zu erlangen, individuelle Anpassbarkeit zu ermöglichen und eine Kosteneffizienz zu erreichen. Es wurden klare Ziele in den Bereichen Verfügbarkeit, Performanz, Sicherheit und Skalierbarkeit definiert, anhand deren das Projekt ausgerichtet…
Cloudy mit Aussicht auf Wörter: Unser Weg mit CrowdCloud
Willkommen zu unserem Erfahrungsbericht aus der Vorlesung „System Engineering and Management“. In den letzten Monaten haben wir uns an ein Projekt gewagt, das uns sowohl technisch als auch persönlich herausgefordert hat – CrowdCloud. Anstatt uns in trockene Theorien zu verlieren, möchten wir euch in diesem Blog-Beitrag erzählen, wie aus einer spontanen Idee eine interaktive, skalierbare…
Importance and Impact of Quantum Safe Encryption for Enterprises
More than forty years ago Richard Feynman’s paper “Simulating Physics with Computers” was published [1], laying the foundational vision for what we now recognize as quantum computing. Since then, quantum computing has become a fascinating and fast-expanding field at the forefront of technological innovation. With the potential to revolutionize computing power and solve complicated issues that traditional…
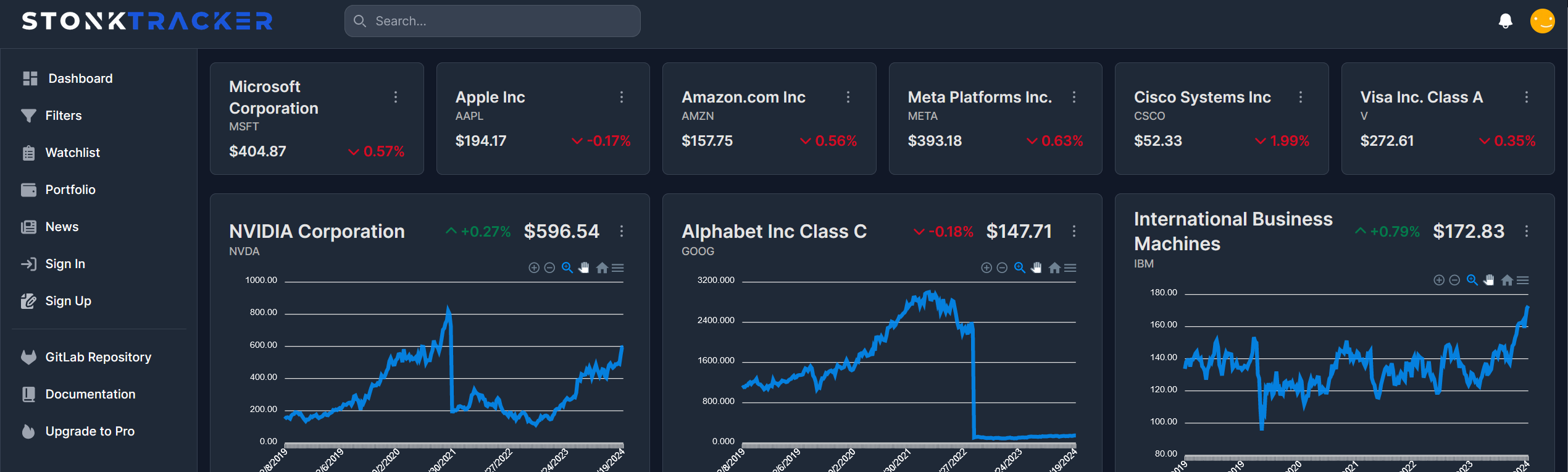
Die Meere der Systemtechnik navigieren: Eine Reise durch die Bereitstellung einer Aktien-Webanwendung in der Cloud
Auf zu neuen Ufern: Einleitung Die Cloud-Computing-Technologie hat die Art und Weise, wie Unternehmen Anwendungen entwickeln, bereitstellen und skalieren, revolutioniert. In diesem Beitrag, der im Rahmen der Vorlesung “143101a System Engineering und Management” entstanden ist, werden wir uns darauf konzentrieren, wie eine bereits bestehende Webanwendung zur Visualisierung und Filterung von Aktienkennzahlen auf der IBM Cloud-Infrastruktur…
Why system monitoring is important and how we approached it
Introduction Imagine building a service that aims to generate as much user traffic as possible to be as profitable as possible. The infrastructure of your service usually includes some kind of backend, a server and other frameworks. One day, something is not working as it should and you can’t seem to find out why. You…
Combining zerolog & Loki
Publish zerolog events to Loki in just a few lines of code.
- Allgemein, Student Projects, System Architecture, System Designs, System Engineering, Teaching and Learning
Using Keycloak as IAM for our hosting provider service
Discover how Keycloak can revolutionize your IAM strategy and propel your projects to new heights of security and efficiency.
Cybersecurity Breaches
Sicherheitsrisiken im digitalen Zeitalter: Eine Analyse aktueller Cyberangriffe und ihre Implikationen Data Breaches sind eine zunehmende Bedrohung, bei der Hacker und Cyberkriminelle weltweit nach Möglichkeiten suchen, sensible Informationen zu stehlen. Die Motive für solche Angriffe umfassen finanzielle Gewinne, Prestige und Spionage. Laut dem Verizon Report von 2023 machen technische Schwachstellen nur etwa 8% aller Angriffsmethoden…

