Category: Secure Systems
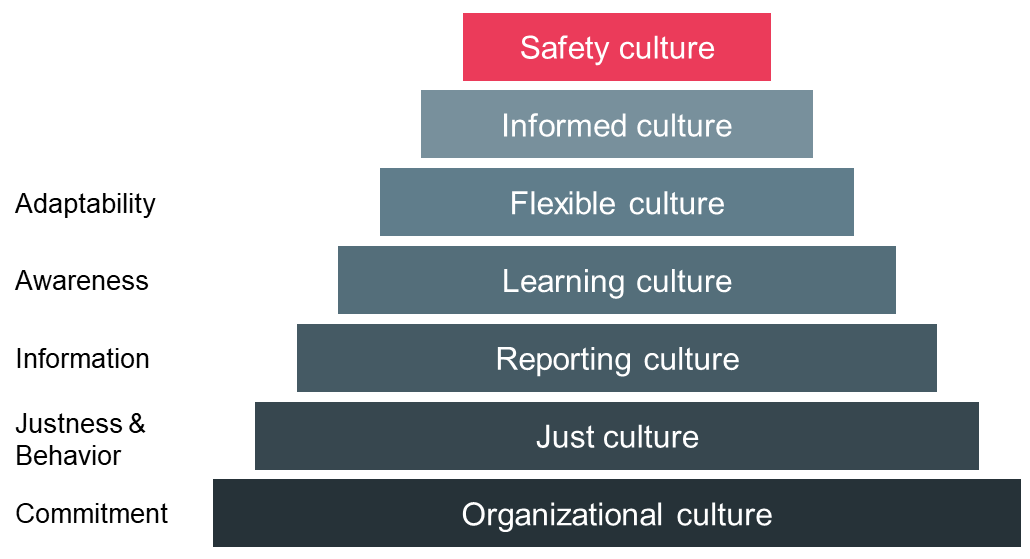
Safety Culture – Improve “the way we do things around here”
The safety culture of an organization is the key indication of its performance related to safety. It incorporates the visible rules, norms and practices as well as the implicit factors such as values, beliefs and assumptions. That is why the safety culture reflects “the way we do things around here” which is the most precise…
Smart Meter
Smart meters are a controversial topic in Germany. Still there are no certified products available although the roll out was planned at the beginning of 2018. Security breaches can affect customer data as well as the safety of the energy net. That’s why there are very strict security guidelines provided by the BSI. Several smart…
Why AI is a Threat for our Digital Security
Artificial intelligence has a great potential to improve many areas of our lives in the future. But what happens when these AI technologies are used maliciously? Sure, a big topic may be autonomous weapons or so called “killer robots”. But beside our physical security – what about our digital one? How the malicious use of…
Cloud security tools and recommendations for DevOps in 2018
Introduction Over the last five years, the use of cloud computing services has increased rapidly, in German companies. According to a statistic from Bitkom Research in 2018, the acceptance of cloud-computing services is growing. Cloud-computing brings many advantages for a business. For example, expenses for the internal infrastructure and its administration can be saved. Resource…
Usability and Security
Usability and Security – Is a tradeoff necessary? Usability is one of the main reasons for a successful software with user interaction. But often it is worsened by high security standards. Furthermore many use cases need authentication, authorisation and system access where high damage is risked when security possibilities get reduced. In this article the…
Security in Smart Cities
Today cities are growing bigger and faster than ever before. This results in various negative aspects for the citizens such as increased traffic, pollution, crime and cost of living, just to name a few. Governments and city administrations and authorities are in need to find solutions in order to alleviate these drawbacks. Over the past…
Differential Privacy – Privacy-preserving data analysis
It is widely known that tech companies, like Apple or Google and their partners collect and analyse an increasing amount of information. This includes information about the person itself, their interaction and their communication. It happens because of seemingly good motives such as: Recommendation services: e.g. word suggestions on smartphone keyboard Customizing a product or…
Beyond Corp – Google’s approach to enterprise security
What is Beyond Corp? Beyond corp is a concept which was developed and is used by Google and is by now adopted by some other companies. The idea behind it was to get away from the intranet and its perimeter defense, where, if you breach the perimeter you can access much of the enterprise data.…
Disaster prevention in Germany
This article has two main topics: First a short overview about the organization of the disaster prevention in Germany. The second part of this article is about the consequences of a national blackout and how to prepare for this disaster.

You must be logged in to post a comment.