Category: Secure Systems
Cryptomining Malware – How criminals use your devices to get wealthy!
Has your computer ever been slow and you couldn’t tell what the problem was? Nowadays, illicit cryptomining can cause those performance problems. It dethroned ransomware as the top cybersecurity threat in 2018. (Webroot Threat Report 2018) A simple website visit can start the mining process as a javascript running in the background of the browser…
The (in)security about speaker legitimacy detection
For the most of us, voices are a crucial part in our every-day communication. Whether we talk to other people over the phone or in real life, through different voices we’re able to distinguish our counterparts, convey different meanings with the same words, and – maybe most importantly – connect the voice we hear to…
Security and Usability: How to design secure systems people can use.
Security hit a high level of importance due to rising technological standards. Unfortunately it leads to a conflict with Usability as Security makes operations harder whereas Usability is supposed to make it easier. Many people are convinced that there is a tradeoff between them. This results in either secure systems that are not usable or…
How does Tor work?
Written by Tim Tenckhoff – tt031 | Computer Science and Media 1. Introduction The mysterious dark part of the internet – hidden in depths of the world wide web, is well known as a lawless space for shady online drug deals or other criminal activities. But in times of continuous tracking on the Internet, personalized…

About the Robustness of Machine Learning
In the past couple of years research in the field of machine learning (ML) has made huge progress which resulted in applications like automated translation, practical speech recognition for smart assistants, useful robots, self-driving cars and lots of others. But so far we only have reached the point where ML works, but may easily be…
Mobile Security – How secure are our daily used devices?
Nowadays, the usage of mobile devices has become a part of our everyday life. A lot of sensitive and personal data is stored on these devices, which makes them more attractive targets for attackers. Also, many companies offer the possibility to work remotely, which results in storing confidential business information on private phones and therefore…
Crypto-Trading: Securing Million Worth API-Keys in a Distributed System
The teaching of IT security is often about trust boundaries – these are drawn at the interface of the system to the outside world. While this view is dangerous even with a monolithic system, it is simply wrong with a distributed system. Especially when the system’s data is so delicate that you don’t even want…
Autonomous War – Which dangers are associated with warfare without human intervention?
The term autonomous war has been a controversial topic for years. But what exactly does the term actually mean? Autonomous war means the use of autonomous lethal weapons (short: LAWs) and machines or vehicles, which are primarily used by the military for modern warfare. Autonomous weapon systems can decide independently about life and death on…
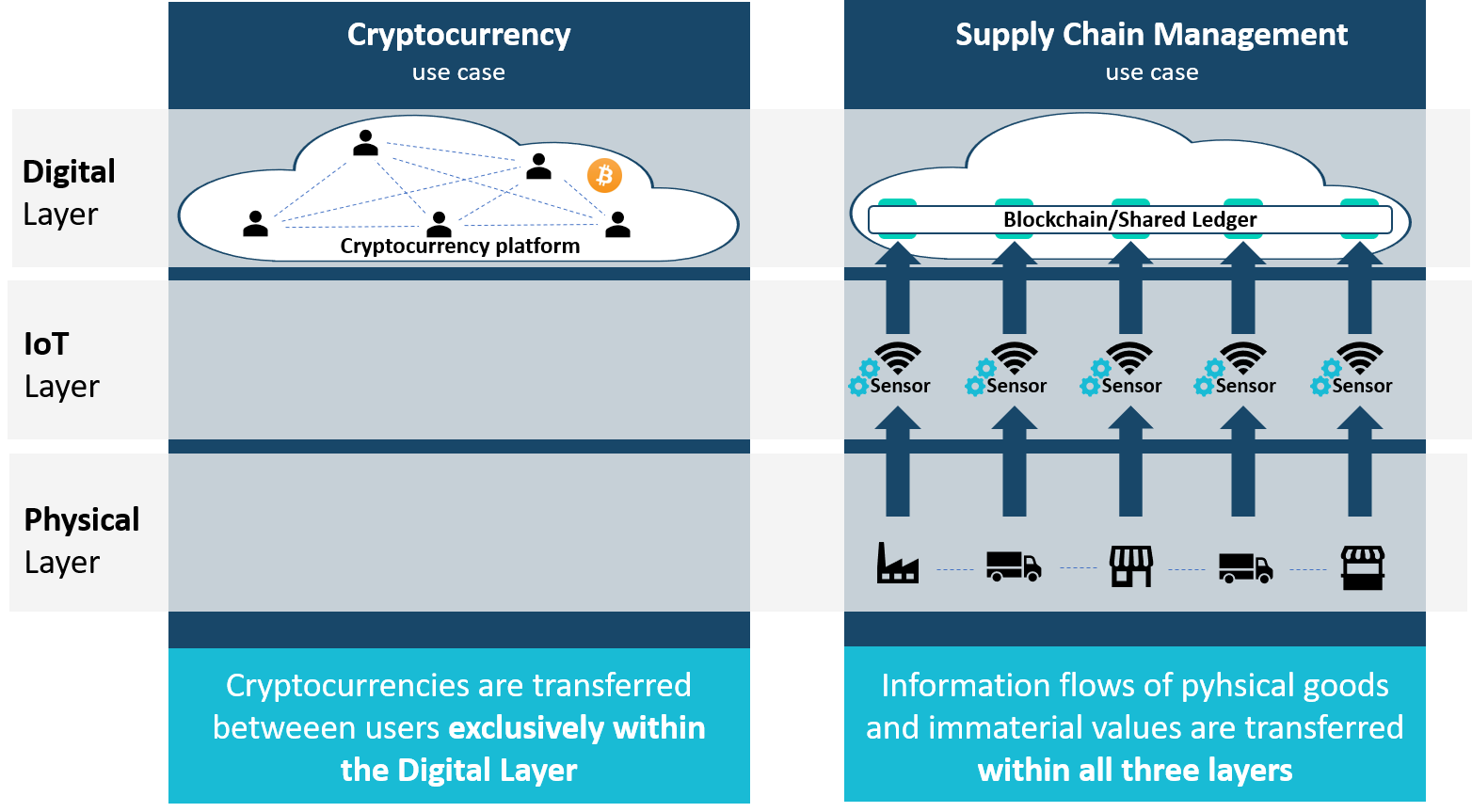
Blockchain Risks and Chances – An 2018 Overview on Public and Private Blockchain, Smart Contracts, DAOs and ICOs
A few years ago, talking about Blockchain was largely consistent with talking about the technology behind Bitcoin. In contrast, Blockchain nowadays comprises a whole technology branch, whereby the Blockchain itself can be implemented in lots of various ways. Not a year ago, on December 17, 2018, the peak of the Bitcoin hype was reached by…

You must be logged in to post a comment.