Month: September 2020
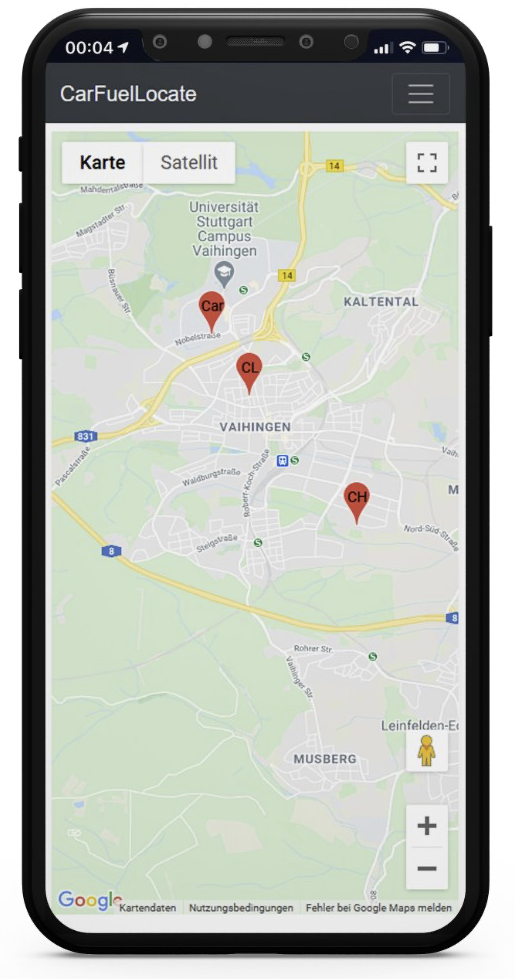
Get car location using Raspberry Pi and Google Cloud IoT Core
Google Cloud Platform There is no specific point, why we used the Google Platform. Our decision is based on serveral points. First of we learned a lot about the IBM Cloud and AWS in our Lecture Software Development for Cloud Computing and wanted to learn how other cloud providers work. Another point is, that we…
Your first Web App in the cloud – AWS and Beanstalk
Hello fellow readers! In this blog you will learn how to set up a web-game with worldwide ranking in the cloud without having to deal with complicated deployment. That means for you: More time on your application. The app uses Node.js with Express and MongoDB as backend. The frontend is made out of plain html,…
Getting Started with your first Software Project using DevOps
This Post is a getting started guide for creating a DevOps enabled web based software project.
Racism as consequence of catastrophes?
The Corona pandemic has worsen racism towards some ethnic groups, but it has not created something that was not already there. This article examines how racism has developed during the Corona pandemic. In addition, a study will be referred to which examines psychological aspects of the perception of ethnicity under scarcity.
Sicherheitssysteme in der Raumfahrt
Disclaimer Die heutige Raumfahrt oder auch allgemein Raumfahrt ist ein sehr komplexes und vielschichtiges Thema. Nicht grundlos werden umgangssprachlich schwierige Themen als “Raketenwissenschaften” bezeichnet. Dieser Artikel möchte nicht die Raumfahrt in ihrer Gänze beschreiben sondern nur einen sehr kleinen Teil im Bereich der Sicherheit beleuchten. Hierfür wurden sich vor allem auf den Start einer Rakete…
Personenerkennung und Personenidentifizierung EDV-NR: 143307a zu Hören bei Prof. Walter Kriha
Rafael Janetzko, Matrikel-Nr.: 40190 Die Anwendungsgebiete der Personenerkennung und Personenidentifizierung wachsen und werden immer präziser, daher gilt die Personenerkennung und Personenidentifizierung im Bereich der Sicherheit zunehmend als essentiell notwendig und ist fast überall vertreten. Heutzutage entsperren die meisten Leute ihr Smartphone mit biometrischen Daten oder überwachen ihr Eigentum mittels Kamerasystemen, die immer ausgereifter und günstiger…
The development of the intranet into BeyondCorp
Aron Köcher, Miro Bilge Only a few years earlier, the solution to exchange digital information like documents or pictures was to establish a physical connection between the participants. A usb stick was passed around the class to exchange music, you went to your friends house to print some urgent papers or a group of friends…
How are vulnerabilities exploited to compromise a system?
This article is a recap of the “Live Hack” presentation, held in the lecture “Sichere Systeme” in SS 2020. It will introduce different vulnerabilities like XSS and SQL-Injection and shows how passwords can be cracked under certain circumstances. The last step explains how a SUID binary was exploited to gain root access on the target…
Behind the scenes of modern operating systems — Security through isolation (Part 1)
In recent years, since the Internet has become available to almost anyone, application and runtime security is important more than ever. Be it an (unknown) application you download and run from the Internet or some server application you expose to the Internet, it’s almost certainly a bad idea to run apps without any security restrictions…
