Month: August 2018
Differential Privacy – Privacy-preserving data analysis
It is widely known that tech companies, like Apple or Google and their partners collect and analyse an increasing amount of information. This includes information about the person itself, their interaction and their communication. It happens because of seemingly good motives such as: Recommendation services: e.g. word suggestions on smartphone keyboard Customizing a product or…
Beyond Corp – Google’s approach to enterprise security
What is Beyond Corp? Beyond corp is a concept which was developed and is used by Google and is by now adopted by some other companies. The idea behind it was to get away from the intranet and its perimeter defense, where, if you breach the perimeter you can access much of the enterprise data.…
Disaster prevention in Germany
This article has two main topics: First a short overview about the organization of the disaster prevention in Germany. The second part of this article is about the consequences of a national blackout and how to prepare for this disaster.
Server “less” Computing vs. Security
Summary about Serverless Computing with Security aspects.
Web Performance Optimization for Continuous Deployment – Move fast and don’t lose performance
The performance of websites today is a decisive factor in how many users visit them and thus how much money can be earned from them. The impact of this fact is further enhanced by the widespread use of mobile devices and the speed of the mobile Internet. To counteract the development of heavyweight websites, web…
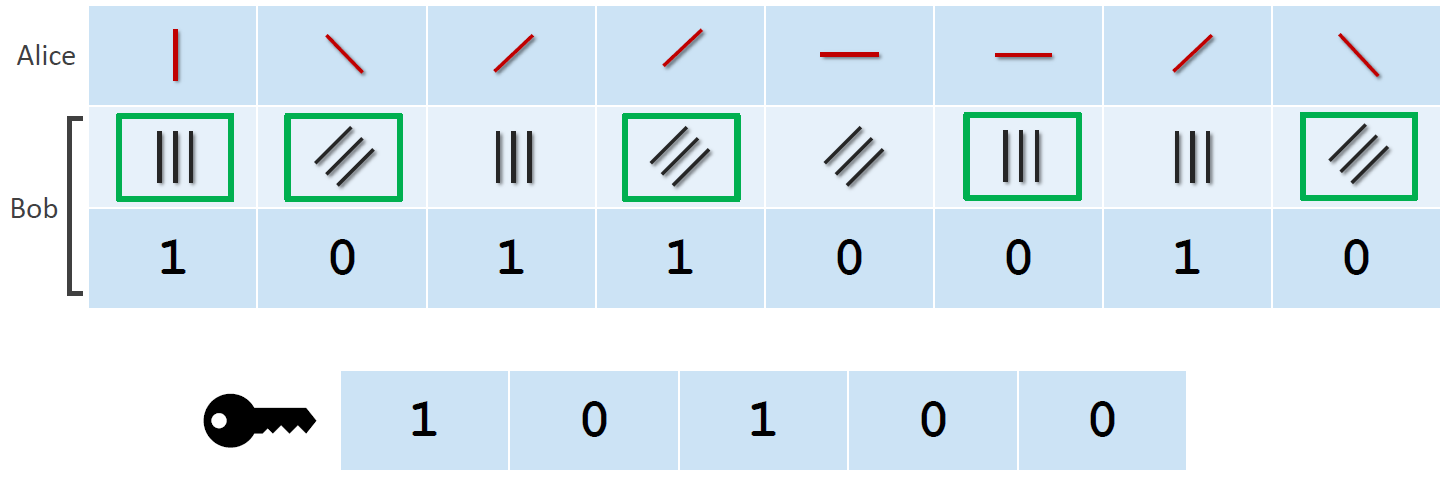
Quantum and Post-Quantum Cryptography
In a world where political activists and dissidents get persecuted by authoritarian governments, strong cryptography is more necessary than ever. But the general public benefits from it as well. Identity theft, banking fraud and cyber bullying can happen to anybody. The most effective protection is to not make sensitive material available to anybody. Unfortunately some…
