A blog about current topics in computer science and media, maintained by students of the Hochschule der Medien Stuttgart (Stuttgart Media University).
Recent Posts
Web Performance Optimization for Continuous Deployment – Move fast and don’t lose performance
The performance of websites today is a decisive factor in how many users visit them and thus how much money can be earned from them. The impact of this fact is further enhanced by the widespread use of mobile devices and the speed of the mobile Internet. To counteract the development of heavyweight websites, web…
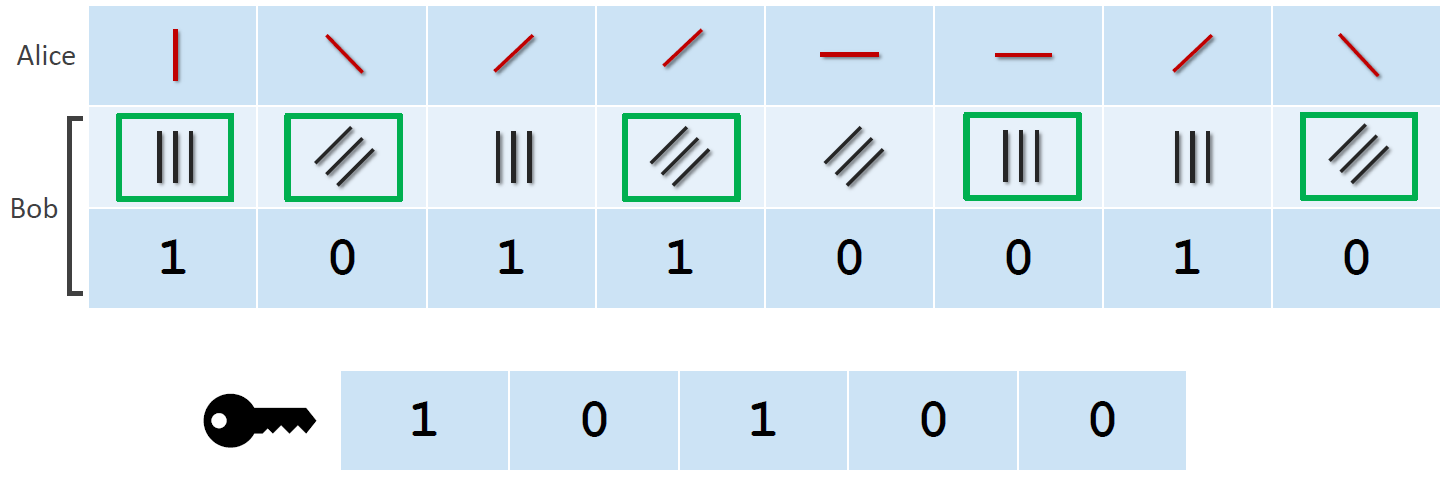
Quantum and Post-Quantum Cryptography
In a world where political activists and dissidents get persecuted by authoritarian governments, strong cryptography is more necessary than ever. But the general public benefits from it as well. Identity theft, banking fraud and cyber bullying can happen to anybody. The most effective protection is to not make sensitive material available to anybody. Unfortunately some…
- Cloud Technologies, Scalable Systems, Student Projects, System Architecture, Ultra Large Scale Systems
Building a fully scalable architecture with AWS
What I learned in building the StateOfVeganism ? By now, we all know that news and media shape our viewson these discussed topics. Of course, this is different from person to person. Some might be influenced a little more than others, but there always is some opinion communicated. Considering this, it would be really interesting…
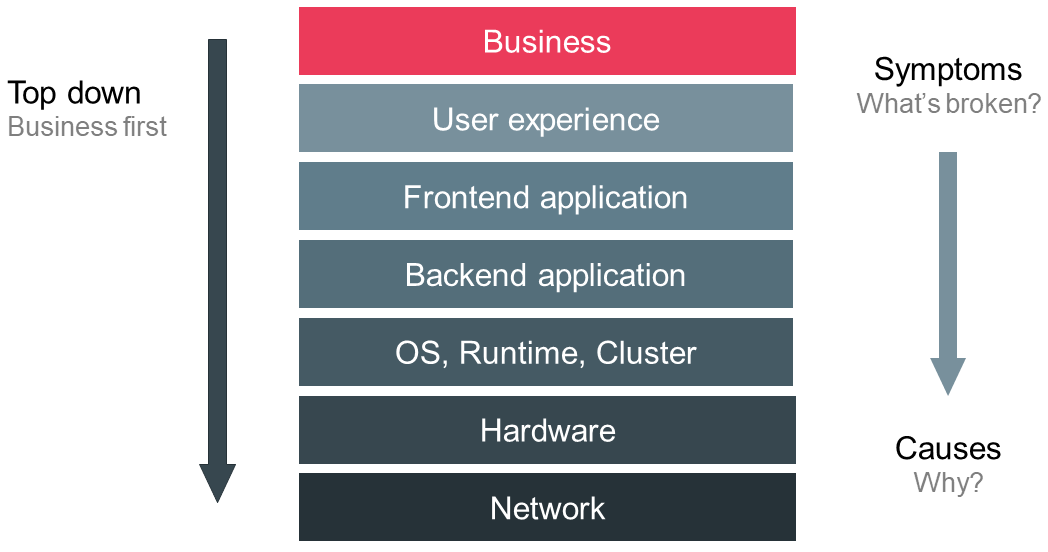
End user monitoring – Establish a basis to understand, operate and improve software systems
End user monitoring is crucial for operating and managing software systems safely and effectively. Beyond operations, monitoring constitutes a basic requirement to improve services based on facts instead of instincts. Thus, monitoring plays an important role in the lifecycle of every application. But implementing an effective monitoring solution is challenging due to the incredible velocity…
RUST – Safety During and After Programming
Summary about Rust and how RustBelt has achieved to prove its safety with mathematical concepts.
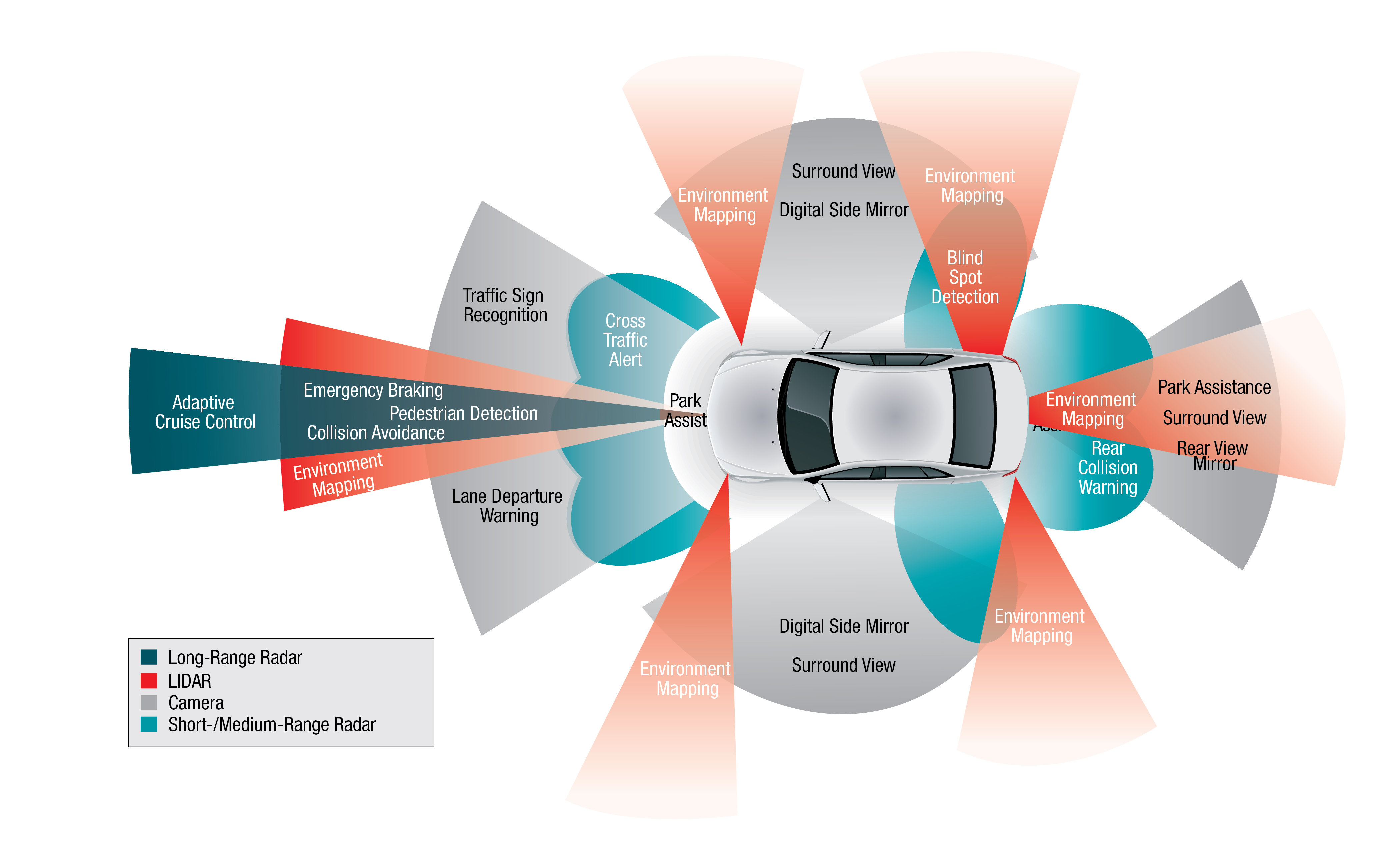
Safety and protection of autonomous vehicles
Autonomous cars are vehicles that can drive to a predetermined destination in real traffic without the intervention of a human driver. To ensure that the car gets from A to B as safely and comfortably as possible, various precautions must be taken. These precautions are explained in the following sections using various questions and security…
The new CI world, Wrapping it up with Git
Welcome to part 6 – Man we are on a writing flow! – of our blog posts series. After all the coding done in the last parts, let’s take a more laid back look at CI and Git. Nowadays many agile teams work with Git and Feature Branches. A developer works with on a feature…
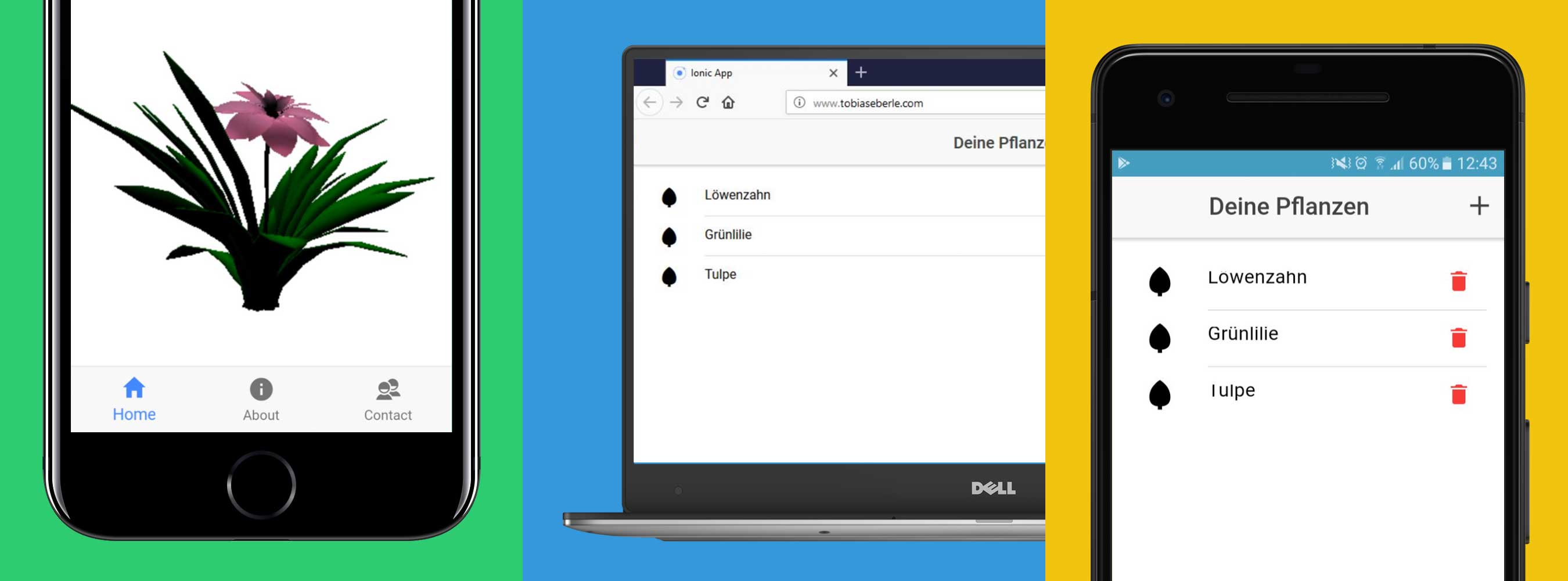
Continuous Integration & Deployment for a Cross-Platform Application – Part 2
In the first part we pointed out how we set up the infrastructure for our CI system. Now we would like to explain how we build a pipeline for our cross-platform application and what features of GitLab CI we made use of.
Supply Chain Management using Blockchain Technology – Hands-On Hyperledger (Part 2)
Implementation Model The model we’ve chosen is an attempt to implement one part of a large SCM business model. Since an example of shipping processes for single items does already exist on IBM’s platform ‘DeveloperWorks’, we focused on the ability to create and place composite orders.
Buzzwords
AI Amazon Web Services architecture artificial intelligence AWS AWS Lambda Ci-Pipeline CI/CD Cloud Cloud-Computing Cloud Computing Containers Continuous Integration deep learning DevOps distributed systems Docker Enterprise IT Git gitlab Gitlab CI IBM Bluemix Jenkins Kubernetes Linux loadbalancing machine learning Microservices Monitoring Node.js Python scaling secure systems security serverless social media Sustainability System Engineering System Engineering and Management Terraform Test-Driven Development Testing ULS ultra large scale systems Web Performance
