A blog about current topics in computer science and media, maintained by students of the Hochschule der Medien Stuttgart (Stuttgart Media University).
Recent Posts
Cloud basierter Password Manager
von Benjamin Schweizer (bs103) und Max Eichinger (me110) Abstract Können Passwort Manager Anbieter meine Passwörter lesen? Wir wollten auf Nummer sichergehen und haben unseren Eigenen entwickelt. Dieser Artikel zeigt auf welche Schritte wir hierfür unternehmen mussten.Dabei haben wir unser Frontend mittels Flutter und unser Backend in AWS umgesetzt. Außerdem gehen wir auf IaC mittels Terraform…
How do you get a web application into the cloud?
by Dominik Ratzel (dr079) and Alischa Fritzsche (af094) For the lecture “Software Development for Cloud Computing”, we set ourselves the goal of exploring new things and gaining experience. We focused on one topic: “How do you get a web application into the cloud?”. In doing so, we took a closer look at Continuous Integration /…
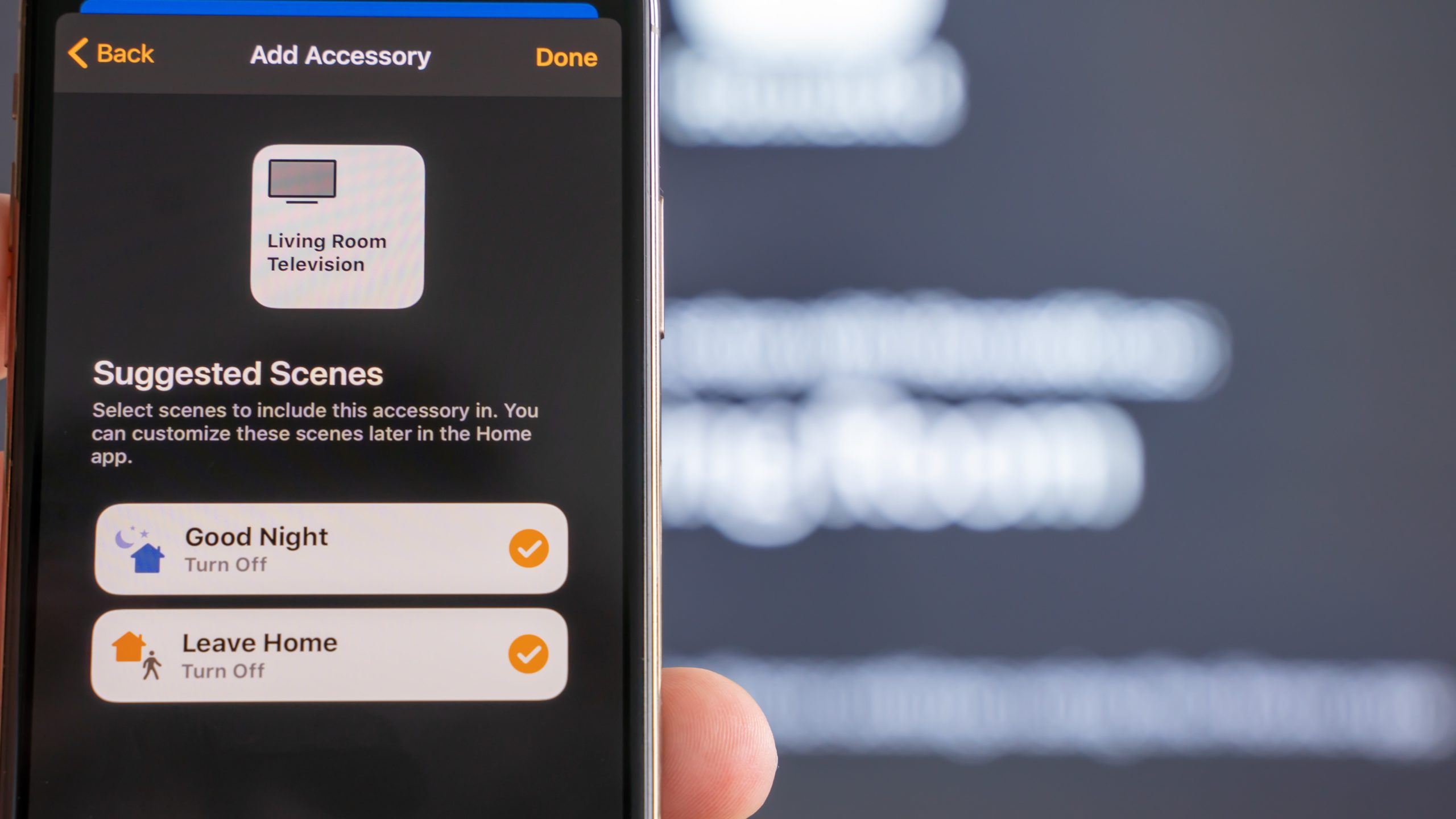
Why It’s So Easy to Hack Your Smart Home
Every day, new smart home accessories go online for the first time to join the Internet of Things. Many of them enjoy the unwarranted trust of their owners.
HAFNIUM EXCHANGE SERVER ATTACKS – What happened and how to protect yourself
an article by Carina Szkudlarek, Niklas Schildhauer and Jannik Smidt This post is going to review the zero day exploit of the Microsoft Exchange Servers starting in January 2021.It will look into the methods of SSRF and the exploitation of mistakes in the deserialization of input values to procure privileged code execution. INTRODUCTION In early…
Die elektronische Patientenakte – Wie sicher ist die zentrale Digitalisierung im Gesundheitswesen?
Oftmals ist es für Ärzte schwer Behandlungen optimal durchzuführen, weil Befunde fehlen oder der Arzt keine Informationen darüber hat wie frühere Behandlungen abgelaufen sind. Um dies in Zukunft vermeiden zu können, wurde am 01. Januar 2021 die elektronische Patientenakte (kurz: ePA) in einem 3 Phasen Modell eingeführt. In der ersten Phase konnten alle gesetzlich Versicherten…
Digital Ghostbusters – Der Malware auf der Spur
Die Suche nach Malware der Cyberkriminellen im Darknet: Welche Absichten stecken hinter den globalen Ransomware-Angriffen und besteht ein Zusammenhang zwischen Hacker und Regierungen?
Der Staat und die IT-Sicherheit: Was Staatstrojaner, Luca und die CDU-Wahlkampf-App verbindet
In der IT-Sicherheit war viel los in letzter Zeit. Das haben wir auch in der Vorlesung „Sichere Systeme“ bei Herrn Kriha gemerkt, in der wir jede Woche aktuelle IT-Sicherheits-News gesammelt haben – im Laufe des Semesters kamen wir auf über 20 Seiten mit Links zu Heise, Golem und Co. Im Rahmen dieser Lehrveranstaltung schreibe ich…
Mechanismen bei System-Programmiersprachen zum Erreichen von Memory-, Thread- und Type-Safety
Motivation Ende letzten Monats (Juli, 2021) hat die CWE (Common Weakness Enumeration) einen Bericht veröffentlicht, welcher die Top 25 der Software-Schwachstellen aufzeigt. Es handelt sich dabei um eine Auswertung von gefundenen Schwachstellen der letzten zwei Jahre in verschiedenen Software-Systemen. Der Bericht umfasst eine Liste der 40 schwerwiegensten Schwachstellen. Dabei handelt es sich um Schwachstellen, welche…
Unsafe Languages, Inadequate Defense Mechanisms and Our Dangerous Addiction to Legacy Code
Over the last 20 years, developing secure software has become increasingly important. To this day, we write a significant amount of code in languages with manual memory management. However, the Peter Parker principle states that “great power comes with great responsibility”. Many scoring systems classify, enumerate and rank prevalence of known vulnerabilities. In theory, developers…
Supply Chain Attacks – Die Lieferkette schlägt zurück
ein Artikel von Verena Eichinger, Amelie Kassner und Elisa Zeller Nach SolarWinds schafft es eine neue Schlagzeile aus der IT-Welt in den Massenmedien ihre Kreise zu ziehen. Über 500 Supermärkte in Schweden mussten wegen eines Cyberangriffs schließen. Wie bereits bei SolarWinds handelt es sich auch hier um eine Supply Chain Attack (SCA). Mittlerweile fällt dieser…
Buzzwords
AI Amazon Web Services architecture artificial intelligence AWS AWS Lambda Ci-Pipeline CI/CD Cloud Cloud-Computing Cloud Computing Containers Continuous Integration deep learning DevOps distributed systems Docker Enterprise IT Git gitlab Gitlab CI IBM Bluemix Jenkins Kubernetes Linux loadbalancing machine learning Microservices Monitoring Node.js Python scaling secure systems security serverless social media Sustainability System Engineering System Engineering and Management Terraform Test-Driven Development Testing ULS ultra large scale systems Web Performance
